這算是一個蠻特別的需求,只有針對特定的domain時,才會將DNS query轉送到特定的DNS Server,不過似乎挺多單位常有這樣的需求,所以還是趕緊給它記下來吧:
zone "test.com"
{
type forward;
forwarders { 192.168.0.254; 192.168.0.253; };
};
就是這麼簡單囉,凡是看到test.com的DNS查詢時便forward到192.168.0.254與192.168.0.253這兩台DNS Server。
Tuesday, December 25, 2007
Fix NFS ports
NFS Server有一個特性,那就是除了portmapper與nfs分別是使用固定的port number外(portmapper:111,nfs:2049),其它的port都是隨機產生的,如下所示:
[root@server3 ~]# rpcinfo -p
program vers proto port
100000 2 tcp 111 portmapper
100000 2 udp 111 portmapper
100011 1 udp 745 rquotad
100011 2 udp 745 rquotad
100011 1 tcp 748 rquotad
100011 2 tcp 748 rquotad
100003 2 udp 2049 nfs
100003 3 udp 2049 nfs
100003 4 udp 2049 nfs
100003 2 tcp 2049 nfs
100003 3 tcp 2049 nfs
100003 4 tcp 2049 nfs
100021 1 udp 1028 nlockmgr
100021 3 udp 1028 nlockmgr
100021 4 udp 1028 nlockmgr
100021 1 tcp 3767 nlockmgr
100021 3 tcp 3767 nlockmgr
100021 4 tcp 3767 nlockmgr
100005 1 udp 760 mountd
100005 1 tcp 763 mountd
100005 2 udp 760 mountd
100005 2 tcp 763 mountd
100005 3 udp 760 mountd
100005 3 tcp 763 mountd
100024 1 udp 832 status
100024 1 tcp 835 status
[root@server3 ~]# service nfs restart; service nfslock restart
Shutting down NFS mountd: [ OK ]
Shutting down NFS daemon: [ OK ]
Shutting down NFS quotas: [ OK ]
Shutting down NFS services: [ OK ]
Starting NFS services: [ OK ]
Starting NFS quotas: [ OK ]
Starting NFS daemon: [ OK ]
Starting NFS mountd: [ OK ]
Stopping NFS locking: [ OK ]
Stopping NFS statd: [ OK ]
Starting NFS statd: [ OK ]
[root@server3 ~]# rpcinfo -p
program vers proto port
100000 2 tcp 111 portmapper
100000 2 udp 111 portmapper
100011 1 udp 904 rquotad
100011 2 udp 904 rquotad
100011 1 tcp 907 rquotad
100011 2 tcp 907 rquotad
100003 2 udp 2049 nfs
100003 3 udp 2049 nfs
100003 4 udp 2049 nfs
100003 2 tcp 2049 nfs
100003 3 tcp 2049 nfs
100003 4 tcp 2049 nfs
100021 1 udp 1028 nlockmgr
100021 3 udp 1028 nlockmgr
100021 4 udp 1028 nlockmgr
100021 1 tcp 2229 nlockmgr
100021 3 tcp 2229 nlockmgr
100021 4 tcp 2229 nlockmgr
100005 1 udp 919 mountd
100005 1 tcp 922 mountd
100005 2 udp 919 mountd
100005 2 tcp 922 mountd
100005 3 udp 919 mountd
100005 3 tcp 922 mountd
100024 1 udp 971 status
100024 1 tcp 974 status
如果要利用iptables加以控管實在是有些困難之處,所以我們可以做的是將這些daemon指定使用固定的port number,以下的步驟將告訴你怎麼做到這一點:
Linux distro: CentOS 5.0
1. 修改/etc/sysconfig/nfs檔案中的參數如下:
RQUOTAD_PORT=9000
LOCKD_TCPPORT=9001
LOCKD_UDPPORT=9001
MOUNTD_PORT=9002
STATD_PORT=9003
2. 重啟nfs與nfslock daemon,並驗證:
[root@server3 ~]# service nfs restart; service nfslock restart
Shutting down NFS mountd: [ OK ]
Shutting down NFS daemon: [ OK ]
Shutting down NFS quotas: [ OK ]
Shutting down NFS services: [ OK ]
Starting NFS services: [ OK ]
Starting NFS quotas: [ OK ]
Starting NFS daemon: [ OK ]
Starting NFS mountd: [ OK ]
Stopping NFS locking: [ OK ]
Stopping NFS statd: [ OK ]
Starting NFS statd: [ OK ]
[root@server3 ~]# rpcinfo -p
program vers proto port
100000 2 tcp 111 portmapper
100000 2 udp 111 portmapper
100011 1 udp 9000 rquotad
100011 2 udp 9000 rquotad
100011 1 tcp 9000 rquotad
100011 2 tcp 9000 rquotad
100003 2 udp 2049 nfs
100003 3 udp 2049 nfs
100003 4 udp 2049 nfs
100003 2 tcp 2049 nfs
100003 3 tcp 2049 nfs
100003 4 tcp 2049 nfs
100021 1 udp 9001 nlockmgr
100021 3 udp 9001 nlockmgr
100021 4 udp 9001 nlockmgr
100021 1 tcp 9001 nlockmgr
100021 3 tcp 9001 nlockmgr
100021 4 tcp 9001 nlockmgr
100005 1 udp 9002 mountd
100005 1 tcp 9002 mountd
100005 2 udp 9002 mountd
100005 2 tcp 9002 mountd
100005 3 udp 9002 mountd
100005 3 tcp 9002 mountd
100024 1 udp 9003 status
100024 1 tcp 9003 status
如此便完成了固定NFS Server的port number。
[root@server3 ~]# rpcinfo -p
program vers proto port
100000 2 tcp 111 portmapper
100000 2 udp 111 portmapper
100011 1 udp 745 rquotad
100011 2 udp 745 rquotad
100011 1 tcp 748 rquotad
100011 2 tcp 748 rquotad
100003 2 udp 2049 nfs
100003 3 udp 2049 nfs
100003 4 udp 2049 nfs
100003 2 tcp 2049 nfs
100003 3 tcp 2049 nfs
100003 4 tcp 2049 nfs
100021 1 udp 1028 nlockmgr
100021 3 udp 1028 nlockmgr
100021 4 udp 1028 nlockmgr
100021 1 tcp 3767 nlockmgr
100021 3 tcp 3767 nlockmgr
100021 4 tcp 3767 nlockmgr
100005 1 udp 760 mountd
100005 1 tcp 763 mountd
100005 2 udp 760 mountd
100005 2 tcp 763 mountd
100005 3 udp 760 mountd
100005 3 tcp 763 mountd
100024 1 udp 832 status
100024 1 tcp 835 status
[root@server3 ~]# service nfs restart; service nfslock restart
Shutting down NFS mountd: [ OK ]
Shutting down NFS daemon: [ OK ]
Shutting down NFS quotas: [ OK ]
Shutting down NFS services: [ OK ]
Starting NFS services: [ OK ]
Starting NFS quotas: [ OK ]
Starting NFS daemon: [ OK ]
Starting NFS mountd: [ OK ]
Stopping NFS locking: [ OK ]
Stopping NFS statd: [ OK ]
Starting NFS statd: [ OK ]
[root@server3 ~]# rpcinfo -p
program vers proto port
100000 2 tcp 111 portmapper
100000 2 udp 111 portmapper
100011 1 udp 904 rquotad
100011 2 udp 904 rquotad
100011 1 tcp 907 rquotad
100011 2 tcp 907 rquotad
100003 2 udp 2049 nfs
100003 3 udp 2049 nfs
100003 4 udp 2049 nfs
100003 2 tcp 2049 nfs
100003 3 tcp 2049 nfs
100003 4 tcp 2049 nfs
100021 1 udp 1028 nlockmgr
100021 3 udp 1028 nlockmgr
100021 4 udp 1028 nlockmgr
100021 1 tcp 2229 nlockmgr
100021 3 tcp 2229 nlockmgr
100021 4 tcp 2229 nlockmgr
100005 1 udp 919 mountd
100005 1 tcp 922 mountd
100005 2 udp 919 mountd
100005 2 tcp 922 mountd
100005 3 udp 919 mountd
100005 3 tcp 922 mountd
100024 1 udp 971 status
100024 1 tcp 974 status
如果要利用iptables加以控管實在是有些困難之處,所以我們可以做的是將這些daemon指定使用固定的port number,以下的步驟將告訴你怎麼做到這一點:
Linux distro: CentOS 5.0
1. 修改/etc/sysconfig/nfs檔案中的參數如下:
RQUOTAD_PORT=9000
LOCKD_TCPPORT=9001
LOCKD_UDPPORT=9001
MOUNTD_PORT=9002
STATD_PORT=9003
2. 重啟nfs與nfslock daemon,並驗證:
[root@server3 ~]# service nfs restart; service nfslock restart
Shutting down NFS mountd: [ OK ]
Shutting down NFS daemon: [ OK ]
Shutting down NFS quotas: [ OK ]
Shutting down NFS services: [ OK ]
Starting NFS services: [ OK ]
Starting NFS quotas: [ OK ]
Starting NFS daemon: [ OK ]
Starting NFS mountd: [ OK ]
Stopping NFS locking: [ OK ]
Stopping NFS statd: [ OK ]
Starting NFS statd: [ OK ]
[root@server3 ~]# rpcinfo -p
program vers proto port
100000 2 tcp 111 portmapper
100000 2 udp 111 portmapper
100011 1 udp 9000 rquotad
100011 2 udp 9000 rquotad
100011 1 tcp 9000 rquotad
100011 2 tcp 9000 rquotad
100003 2 udp 2049 nfs
100003 3 udp 2049 nfs
100003 4 udp 2049 nfs
100003 2 tcp 2049 nfs
100003 3 tcp 2049 nfs
100003 4 tcp 2049 nfs
100021 1 udp 9001 nlockmgr
100021 3 udp 9001 nlockmgr
100021 4 udp 9001 nlockmgr
100021 1 tcp 9001 nlockmgr
100021 3 tcp 9001 nlockmgr
100021 4 tcp 9001 nlockmgr
100005 1 udp 9002 mountd
100005 1 tcp 9002 mountd
100005 2 udp 9002 mountd
100005 2 tcp 9002 mountd
100005 3 udp 9002 mountd
100005 3 tcp 9002 mountd
100024 1 udp 9003 status
100024 1 tcp 9003 status
如此便完成了固定NFS Server的port number。
Thursday, December 13, 2007
Linux command: screen 應用小技巧
上一篇介紹了screen的基本用法,這一篇呢,就來分享一下screen更進階的一種實用方法。
假使您所要維護的Linux機器有好幾台,每一天都要logon進去關心一下,或是操作一番,每次都要ssh過去的確是有點麻煩,搞不好一天中還要ssh進去好幾次,不太smart。
所以用screen來偷懶吧!用screen所產生的console就算你退出了screen,還是可以保留當時的使用狀況,所以我只需要把screen叫出來用就好了。好處就是快速且又保留當時操作的情境。
假想今天的Server有2台,您每天都要進去關心一下,那麼您可以寫一個script如下:
#!/bin/bash
screen -d -m -S SRV1 -t root@srv1 ssh root@192.168.0.254
screen -d -m -S SRV2 -t root@srv2 ssh root@192.168.0.253
講解一下參數:
-d -m -> 不要去attach這個screen
-S -> 設定screen name,用screen -ls時可以查看,到時可以用screen -r叫回來,有點像這個樣子:
#screen -ls
There are screens on:
555.svr1 (Detached)
560.svr2 (Detached)
# screen -r 555
-> 這樣就會回到Server1
-t -> 設定screen的title,在screen中按下CTRL+a,w時,好方便查詢。
這樣一來呢,當我想到Server1時就執行screen -ls查一下並用screen -r 555切到Server1,夠方便吧!當然你可以讓這隻script在開機時便執行,並搭配SSH免密碼登入。
假使您所要維護的Linux機器有好幾台,每一天都要logon進去關心一下,或是操作一番,每次都要ssh過去的確是有點麻煩,搞不好一天中還要ssh進去好幾次,不太smart。
所以用screen來偷懶吧!用screen所產生的console就算你退出了screen,還是可以保留當時的使用狀況,所以我只需要把screen叫出來用就好了。好處就是快速且又保留當時操作的情境。
假想今天的Server有2台,您每天都要進去關心一下,那麼您可以寫一個script如下:
#!/bin/bash
screen -d -m -S SRV1 -t root@srv1 ssh root@192.168.0.254
screen -d -m -S SRV2 -t root@srv2 ssh root@192.168.0.253
講解一下參數:
-d -m -> 不要去attach這個screen
-S -> 設定screen name,用screen -ls時可以查看,到時可以用screen -r叫回來,有點像這個樣子:
#screen -ls
There are screens on:
555.svr1 (Detached)
560.svr2 (Detached)
# screen -r 555
-> 這樣就會回到Server1
-t -> 設定screen的title,在screen中按下CTRL+a,w時,好方便查詢。
這樣一來呢,當我想到Server1時就執行screen -ls查一下並用screen -r 555切到Server1,夠方便吧!當然你可以讓這隻script在開機時便執行,並搭配SSH免密碼登入。
Thursday, December 06, 2007
Linux command: screen
screen是可遠端登入Linux建立多重終端機的一個非常好用的指令,比如你習慣用putty透過SSH登入到遠端的Linux機器,同時想開啟多個終端機時,怎麼辦呢?這時screen就派上用場了,另一個好處是在screen下所執行的命令,即使你登出了還是會繼續執行,不需另外透過nohup,以下整理一下screen常用到的一些功能。
1. 執行screen: #screen
2. screen熱鍵:
2.1 新增screen: CTRL+a,c
2.2 切換至下個screen: CTRL+a,n
2.3 切換至前一個screen: CTRL+a,a
2.4 查看目前有幾個screen: CTRL+a,w
2.5 離開screen: CTRL+a,d
2.6 刪除screen: #exit or CTRL+a,k
3. 查看目前screen status: #screen -ls
4. 回到screen: #screen -r
1. 執行screen: #screen
2. screen熱鍵:
2.1 新增screen: CTRL+a,c
2.2 切換至下個screen: CTRL+a,n
2.3 切換至前一個screen: CTRL+a,a
2.4 查看目前有幾個screen: CTRL+a,w
2.5 離開screen: CTRL+a,d
2.6 刪除screen: #exit or CTRL+a,k
3. 查看目前screen status: #screen -ls
4. 回到screen: #screen -r
Wednesday, November 21, 2007
FUSE+SSHFS
在Linux中要去mount遠端的Server某個分享資料夾,大部份是透過NFS或是Samba的方法來實做,在此帽客提供另一種方法來做,那便是利用SSH來mount。
OS: CentOS5 kernel version: 2.6.18-8.1.14.el5
透過sshfs便可以達到這樣的需求,但由於使用sshfs之前,必需安裝FUSE module,所以請先至rpm.pbone.net抓取以下的RPM並安裝:
fuse-2.7.0-1.el5.rf.i386.rpm
fuse-devel-2.7.0-3_7.el5.i386.rpm
fuse-kmdl-2.6.18-8.1.14.el5-2.7.0-3_7.el5.i686.rpm
fuse-libs-2.7.0-3_7.el5.i386.rpm
在抓取fuse-sshfs-1.8-1.el5.rf.i386.rpm安裝完後將機器重新開機或是執行modprove fuse。
由於sshfs在mount遠端時都會要求輸入密碼,如同使用ssh一樣,所以我利用了免密碼就可登入到對方主機來做。(在此server2代表client要mount server1的root家目錄)
server2: 產生金鑰並scp到server1
[root@server2 ~]# ssh-keygen -t dsa
Generating public/private dsa key pair.
Enter file in which to save the key (/root/.ssh/id_dsa): Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_dsa.
Your public key has been saved in /root/.ssh/id_dsa.pub.
The key fingerprint is:
97:49:77:78:b0:82:13:59:fa:0b:70:ad:cd:7d:31:f1 root@server2.example.com
[root@server2 ~]# scp .ssh/id_dsa.pub root@10.4.1.33:~/server2.key.pub
Password:
id_dsa.pub
100% 614 0.6KB/s 00:00
server1: 將server2的金鑰copy到~/.ssh/authorized_keys
server1:~/.ssh # touch authorized_keys
server1:~/.ssh # cat ../server2.key.pub > authorized_keys
server2: 使用sshfs mount server1的root家目錄至/mnt/server1
[root@server2 ~]# sshfs root@10.4.1.33:/root /mnt/server1/
[root@server2 ~]# df -h
Filesystem Size Used Avail Use% Mounted on
/dev/hda5 13G 3.6G 8.8G 29% /
/dev/hda1 99M 14M 80M 15% /boot
tmpfs 506M 0 506M 0% /dev/shm
/dev/hda2 4.8G 138M 4.4G 4% /home
sshfs#root@10.4.1.33:/root
1000G 0 1000G 0% /mnt/server1
完成。
OS: CentOS5 kernel version: 2.6.18-8.1.14.el5
透過sshfs便可以達到這樣的需求,但由於使用sshfs之前,必需安裝FUSE module,所以請先至rpm.pbone.net抓取以下的RPM並安裝:
fuse-2.7.0-1.el5.rf.i386.rpm
fuse-devel-2.7.0-3_7.el5.i386.rpm
fuse-kmdl-2.6.18-8.1.14.el5-2.7.0-3_7.el5.i686.rpm
fuse-libs-2.7.0-3_7.el5.i386.rpm
在抓取fuse-sshfs-1.8-1.el5.rf.i386.rpm安裝完後將機器重新開機或是執行modprove fuse。
由於sshfs在mount遠端時都會要求輸入密碼,如同使用ssh一樣,所以我利用了免密碼就可登入到對方主機來做。(在此server2代表client要mount server1的root家目錄)
server2: 產生金鑰並scp到server1
[root@server2 ~]# ssh-keygen -t dsa
Generating public/private dsa key pair.
Enter file in which to save the key (/root/.ssh/id_dsa): Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_dsa.
Your public key has been saved in /root/.ssh/id_dsa.pub.
The key fingerprint is:
97:49:77:78:b0:82:13:59:fa:0b:70:ad:cd:7d:31:f1 root@server2.example.com
[root@server2 ~]# scp .ssh/id_dsa.pub root@10.4.1.33:~/server2.key.pub
Password:
id_dsa.pub
100% 614 0.6KB/s 00:00
server1: 將server2的金鑰copy到~/.ssh/authorized_keys
server1:~/.ssh # touch authorized_keys
server1:~/.ssh # cat ../server2.key.pub > authorized_keys
server2: 使用sshfs mount server1的root家目錄至/mnt/server1
[root@server2 ~]# sshfs root@10.4.1.33:/root /mnt/server1/
[root@server2 ~]# df -h
Filesystem Size Used Avail Use% Mounted on
/dev/hda5 13G 3.6G 8.8G 29% /
/dev/hda1 99M 14M 80M 15% /boot
tmpfs 506M 0 506M 0% /dev/shm
/dev/hda2 4.8G 138M 4.4G 4% /home
sshfs#root@10.4.1.33:/root
1000G 0 1000G 0% /mnt/server1
完成。
Monday, November 19, 2007
[Vsftp] Allow anonymous rewrite files
今天發現到在RHEL/SLES的vsftp中,即使我開放讓anonymous有上傳與建立目錄的權限,但當要上傳並覆蓋原本的檔案時會發生權限不足的問題,原來還要多加一個設定anon_other_write_enable=YES
在此總結允許anonymous所有權限的參數:
anonymous_enable=YES
anon_other_write_enable=YES
anon_upload_enable=YES
anon_mkdir_write_enable=YES
write_enable=YES
在此總結允許anonymous所有權限的參數:
anonymous_enable=YES
anon_other_write_enable=YES
anon_upload_enable=YES
anon_mkdir_write_enable=YES
write_enable=YES
Friday, November 16, 2007
[Shell Script] 執行結果變指令!
#!/bin/bash
## A=100
## ls -l
## free -m
eval "`grep "^## " $0 | sed 's/^## //'`"
echo "A=$A"
短短的幾行,卻內含許多觀念!
## A=100
## ls -l
## free -m
eval "`grep "^## " $0 | sed 's/^## //'`"
echo "A=$A"
短短的幾行,卻內含許多觀念!
Friday, November 02, 2007
Top 10 Reasons Not to Use Ubuntu
http://blog.linuxtoday.com/blog/archives/071031-103438.html
這應該是反諷MS吧,雖然我不太prefer MS ,但青菜蘿菠各有所好囉~
當我把compiz特效展現給同事看時,沒有一個不心動的,已經有人安裝Ubuntu了,不過帽客也當起了免費的技術支援。
這應該是反諷MS吧,雖然我不太prefer MS ,但青菜蘿菠各有所好囉~
當我把compiz特效展現給同事看時,沒有一個不心動的,已經有人安裝Ubuntu了,不過帽客也當起了免費的技術支援。
Thursday, November 01, 2007
DNS cache issue
一般來說,DNS cache的值是以TTL來決定,而TTL也只對於DNS Server與Server之間才有用!如果對DNS Client來說它是不會去做DNS cache的,每查詢一次就update一次RR,但帽客今天發現到了一個非常有趣的現象,當你在DNS Client透過 host / nslookup /dig 來做名稱解析時,每問一次就update一次,這不難理解,合乎常規,但當你用ping時,此時就很怪異了,你會發現!被cache住了!比如我設定 server.example.com 對映到192.168.0.254 / 253, 當你用host查尋時,會每問一次就改變一次對映的IP,但ping確沒有唷!主要的原因是被nscd這隻daemon cache住囉!
nscd daemon就是用來設定DNS Client要cache住Name Server cache查尋的結果多久,這個跟TTL值一點關係也沒有,它也可以應用在LDAP,ypserver等等,以下是它的example config file:
enable-cache passwd yes
positive-time-to-live passwd 600
negative-time-to-live passwd 20
suggested-size passwd 211
check-files passwd yes
persistent passwd yes
shared passwd yes
enable-cache group yes
positive-time-to-live group 3600
negative-time-to-live group 60
suggested-size group 211
check-files group yes
persistent group yes
shared group yes
enable-cache hosts yes
positive-time-to-live hosts 5
negative-time-to-live hosts 0
suggested-size hosts 211
check-files hosts yes
persistent hosts no
shared hosts yes
hosts -> 就是針對DNS cache用的。 :)
nscd daemon就是用來設定DNS Client要cache住Name Server cache查尋的結果多久,這個跟TTL值一點關係也沒有,它也可以應用在LDAP,ypserver等等,以下是它的example config file:
enable-cache passwd yes
positive-time-to-live passwd 600
negative-time-to-live passwd 20
suggested-size passwd 211
check-files passwd yes
persistent passwd yes
shared passwd yes
enable-cache group yes
positive-time-to-live group 3600
negative-time-to-live group 60
suggested-size group 211
check-files group yes
persistent group yes
shared group yes
enable-cache hosts yes
positive-time-to-live hosts 5
negative-time-to-live hosts 0
suggested-size hosts 211
check-files hosts yes
persistent hosts no
shared hosts yes
hosts -> 就是針對DNS cache用的。 :)
Saturday, October 27, 2007
list all PCI devices
在Linux的作業系統下,如果想要check HW info的方法其實有很多種,比如我想看CPU時,我可以打cat /proc/cpuinfo,想看記憶體時可打free -m,想看HDD space時,可透過fdisk -l等等。
在以前我如果想要看電腦的網卡或是顯示是那家的chip時,我會透過dmesg然後配合grep去找出我想要知道的資訊,不過現在發現到一個更好用的指令lspci,可以透過它很簡單的撈出所有PCI devices的資訊,以下是我HP nc6230的info,真是方便呀。
00:00.0 Host bridge: Intel Corporation Mobile 915GM/PM/GMS/910GML Express Processor to DRAM Controller (rev 03)
00:01.0 PCI bridge: Intel Corporation Mobile 915GM/PM Express PCI Express Root Port (rev 03)
00:1c.0 PCI bridge: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) PCI Express Port 1 (rev 03)
00:1c.1 PCI bridge: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) PCI Express Port 2 (rev 03)
00:1d.0 USB Controller: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) USB UHCI #1 (rev 03)
00:1d.1 USB Controller: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) USB UHCI #2 (rev 03)
00:1d.2 USB Controller: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) USB UHCI #3 (rev 03)
00:1d.7 USB Controller: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) USB2 EHCI Controller (rev 03)
00:1e.0 PCI bridge: Intel Corporation 82801 Mobile PCI Bridge (rev d3)
00:1e.2 Multimedia audio controller: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) AC'97 Audio Controller (rev 03)
00:1e.3 Modem: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) AC'97 Modem Controller (rev 03)
00:1f.0 ISA bridge: Intel Corporation 82801FBM (ICH6M) LPC Interface Bridge (rev 03)
00:1f.1 IDE interface: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) IDE Controller (rev 03)
01:00.0 VGA compatible controller: ATI Technologies Inc M22 [Mobility Radeon X300]
02:04.0 Network controller: Intel Corporation PRO/Wireless 2200BG Network Connection (rev 05)
02:06.0 CardBus bridge: Texas Instruments PCIxx21/x515 Cardbus Controller
02:06.3 Mass storage controller: Texas Instruments PCIxx21 Integrated FlashMedia Controller
02:06.4 Generic system peripheral [0805]: Texas Instruments PCI6411/6421/6611/6621/7411/7421/7611/7621 Secure Digital Controller
02:06.5 Communication controller: Texas Instruments PCI6411/6421/6611/6621/7411/7421/7611/7621 Smart Card Controller
10:00.0 Ethernet controller: Broadcom Corporation NetXtreme BCM5751M Gigabit Ethernet PCI Express (rev 11)
在以前我如果想要看電腦的網卡或是顯示是那家的chip時,我會透過dmesg然後配合grep去找出我想要知道的資訊,不過現在發現到一個更好用的指令lspci,可以透過它很簡單的撈出所有PCI devices的資訊,以下是我HP nc6230的info,真是方便呀。
00:00.0 Host bridge: Intel Corporation Mobile 915GM/PM/GMS/910GML Express Processor to DRAM Controller (rev 03)
00:01.0 PCI bridge: Intel Corporation Mobile 915GM/PM Express PCI Express Root Port (rev 03)
00:1c.0 PCI bridge: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) PCI Express Port 1 (rev 03)
00:1c.1 PCI bridge: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) PCI Express Port 2 (rev 03)
00:1d.0 USB Controller: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) USB UHCI #1 (rev 03)
00:1d.1 USB Controller: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) USB UHCI #2 (rev 03)
00:1d.2 USB Controller: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) USB UHCI #3 (rev 03)
00:1d.7 USB Controller: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) USB2 EHCI Controller (rev 03)
00:1e.0 PCI bridge: Intel Corporation 82801 Mobile PCI Bridge (rev d3)
00:1e.2 Multimedia audio controller: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) AC'97 Audio Controller (rev 03)
00:1e.3 Modem: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) AC'97 Modem Controller (rev 03)
00:1f.0 ISA bridge: Intel Corporation 82801FBM (ICH6M) LPC Interface Bridge (rev 03)
00:1f.1 IDE interface: Intel Corporation 82801FB/FBM/FR/FW/FRW (ICH6 Family) IDE Controller (rev 03)
01:00.0 VGA compatible controller: ATI Technologies Inc M22 [Mobility Radeon X300]
02:04.0 Network controller: Intel Corporation PRO/Wireless 2200BG Network Connection (rev 05)
02:06.0 CardBus bridge: Texas Instruments PCIxx21/x515 Cardbus Controller
02:06.3 Mass storage controller: Texas Instruments PCIxx21 Integrated FlashMedia Controller
02:06.4 Generic system peripheral [0805]: Texas Instruments PCI6411/6421/6611/6621/7411/7421/7611/7621 Secure Digital Controller
02:06.5 Communication controller: Texas Instruments PCI6411/6421/6611/6621/7411/7421/7611/7621 Smart Card Controller
10:00.0 Ethernet controller: Broadcom Corporation NetXtreme BCM5751M Gigabit Ethernet PCI Express (rev 11)
Thursday, October 18, 2007
Wednesday, October 17, 2007
Mac OSX 10.5 Leopard 即將於2007.10.26 PM6:00開賣
根據官方消息,Apple將於今年的10月26號下午6:00開始於Apple Retail Store開賣MAC OSX 10.5 Leopard,帽客真是感到高興呀!不過在高興之餘忽然驚覺我的iBook,能裝嗎?
於是乎馬上去Apple網站瞧瞧,喔!一進首頁就看到在倒數計時呀!ㄟ~Apple真是個大壞蛋呀!來這招搞得我心癢癢,差點忘了要做什麼,二話不說馬上點選Leopard的Tech Specs的頁面,好險上面有說支援PowerPC G4&G5的CPU,這下子放心的許多,等著升級吧我的小白。
Apple MAC OSX 10.5 Leopard Specs
於是乎馬上去Apple網站瞧瞧,喔!一進首頁就看到在倒數計時呀!ㄟ~Apple真是個大壞蛋呀!來這招搞得我心癢癢,差點忘了要做什麼,二話不說馬上點選Leopard的Tech Specs的頁面,好險上面有說支援PowerPC G4&G5的CPU,這下子放心的許多,等著升級吧我的小白。
Apple MAC OSX 10.5 Leopard Specs
Friday, October 12, 2007
熱鬧的10月
Novell於10月4日發表了OpenSUSE 10.3, 而Ubuntu也準備於10月18日發表Ubuntu 7.10 (Gutsy Gibbon), Apple就更讓人興奮了,將於10月底發表MAC OS 10.5 Leopard!
真是個熱鬧的10月呀!目前帽客所用的OS大概有:
1. CentOS5.0 on IBM desktop
2. MAC OS 10.4 on iBook
3. Ubuntu 7.04 on HP nc6230
4. Windows XP PRO SP2 on IBM desktop
5. 以模擬的方式跑RHEL5, SLES10與OpenSUSE 10.3
這麼多的OS,我覺得MAC還是桌面應用的王者,好用直覺夠簡單,Linux則是我吃飯的工具,應用廣泛,沒有它還真的不知道怎麼辦.... 那Windows...... 嗯...... 讓我想一想
真是個熱鬧的10月呀!目前帽客所用的OS大概有:
1. CentOS5.0 on IBM desktop
2. MAC OS 10.4 on iBook
3. Ubuntu 7.04 on HP nc6230
4. Windows XP PRO SP2 on IBM desktop
5. 以模擬的方式跑RHEL5, SLES10與OpenSUSE 10.3
這麼多的OS,我覺得MAC還是桌面應用的王者,好用直覺夠簡單,Linux則是我吃飯的工具,應用廣泛,沒有它還真的不知道怎麼辦.... 那Windows...... 嗯...... 讓我想一想
Tuesday, October 09, 2007
最近狀況
女兒:
快滿8個月了, 嗯 把戲越來越多了,很可愛但也很抓弄人,但我發現到她不太有耐心同時脾氣也很大,老婆說這點像我 @@ 我承認我EQ是低了點, 但我應該還算有耐心吧 呵
人家都說女兒外表也像我, 嗯!感覺好像是耶~ 拿出小時候的照片一比,果然活生生是我的分身~
看來小孩子真是不能偷生,還需要DNA鑑定嗎?
她的外號是企鵝妹,至於為何呢?這點有空我以後在說明,不過不是因為我喜歡玩Linux的關係就是了.
工作:
對於有在瀏覽本Blog的網友,真是感到抱歉,最近公司有一些改變且案子也都排的很趕,所以就沒有太多的心力update一些心得到Blog上,我想應該會一直忙到年底吧.... 沒辦法 @@ 又因為我是Sr. 級的, 所以總是對自己要求高一點,不然怎麼有資格掛Sr.哩~
Linux:
前幾天OpenSUSE 10.3 release了,於是乎當然是馬上download來玩看看囉~ 誰知道在VirtualBox下NIC有些問題get不到IP? 這真是奇怪 我等會在來試看看,如果不行,就問問Google大神看看吧
學習:
1.公司變美商了,所以上面說要加強英文,我的破英文.....的確要加強!以後每個星期 1 3 5 就強迫自己讀英文吧!
2.至於每個星期2 4,預計review一下以前所學的Linux skill吧 我一直很想去考LPIC,但我記憶體小,這種筆試對我來說是比上機考還痛苦...
娛樂:
1. 預計會買Wii送老婆,一來是可以讓她減肥,二來是結婚記念日快到了,應該要表示一下.
2. 假日會玩玩NDSL,雷頓教授與不可思議的小鎮實在很有趣唷! 有NDSL的朋友可千萬不要錯過呀!
快滿8個月了, 嗯 把戲越來越多了,很可愛但也很抓弄人,但我發現到她不太有耐心同時脾氣也很大,老婆說這點像我 @@ 我承認我EQ是低了點, 但我應該還算有耐心吧 呵
人家都說女兒外表也像我, 嗯!感覺好像是耶~ 拿出小時候的照片一比,果然活生生是我的分身~
看來小孩子真是不能偷生,還需要DNA鑑定嗎?
她的外號是企鵝妹,至於為何呢?這點有空我以後在說明,不過不是因為我喜歡玩Linux的關係就是了.
工作:
對於有在瀏覽本Blog的網友,真是感到抱歉,最近公司有一些改變且案子也都排的很趕,所以就沒有太多的心力update一些心得到Blog上,我想應該會一直忙到年底吧.... 沒辦法 @@ 又因為我是Sr. 級的, 所以總是對自己要求高一點,不然怎麼有資格掛Sr.哩~
Linux:
前幾天OpenSUSE 10.3 release了,於是乎當然是馬上download來玩看看囉~ 誰知道在VirtualBox下NIC有些問題get不到IP? 這真是奇怪 我等會在來試看看,如果不行,就問問Google大神看看吧
學習:
1.公司變美商了,所以上面說要加強英文,我的破英文.....的確要加強!以後每個星期 1 3 5 就強迫自己讀英文吧!
2.至於每個星期2 4,預計review一下以前所學的Linux skill吧 我一直很想去考LPIC,但我記憶體小,這種筆試對我來說是比上機考還痛苦...
娛樂:
1. 預計會買Wii送老婆,一來是可以讓她減肥,二來是結婚記念日快到了,應該要表示一下.
2. 假日會玩玩NDSL,雷頓教授與不可思議的小鎮實在很有趣唷! 有NDSL的朋友可千萬不要錯過呀!
Friday, September 21, 2007
Setup bridging network interface on Virtualbox
在Virtualbox中,如果要用bridging到某一張NIC上,是需要一些設定的,不像VMware跑跑它的script就設定好了 @@ 不過這樣還是可以克服的,手動自己搞定就好了,在實作前先講講要怎麼做好了:
1. 新增一bridge到NIC上的interface (bri0 <-> eth0)
2.替Guest OS新增一個Virtual host interface (vbox0 <-> bri0)
3.在Virtualbox中指定要使用的虛擬NIC (vbox0)
Ubuntu 設定步驟:
Setup1. 安裝bridge的套件:
# sudo apt-get install bridge-utils
Setup2. 設定bri0:
# sudo vi /etc/network/interfaces
->
auto br0
iface br0 inet dhcp
bridge_ports eth0
Setup3. 重啟NIC interface:
# sudo /etc/init.d/networking restart
Setup4. 替Guest OS新增一個Virtual host interface
#sudo VBoxAddIF vbox0 br0
Setup5. 在Virtualbox中指定要使用的虛擬NIC (vbox0)
開啟Virtualbox,並設定Guest OS的其中一張NIC bind到vbox0上
搞定收工! 下面是在Ubuntu下的Guest OS: FC7正在更新套件的畫面:
1. 新增一bridge到NIC上的interface (bri0 <-> eth0)
2.替Guest OS新增一個Virtual host interface (vbox0 <-> bri0)
3.在Virtualbox中指定要使用的虛擬NIC (vbox0)
Ubuntu 設定步驟:
Setup1. 安裝bridge的套件:
# sudo apt-get install bridge-utils
Setup2. 設定bri0:
# sudo vi /etc/network/interfaces
->
auto br0
iface br0 inet dhcp
bridge_ports eth0
Setup3. 重啟NIC interface:
# sudo /etc/init.d/networking restart
Setup4. 替Guest OS新增一個Virtual host interface
#sudo VBoxAddIF vbox0
Setup5. 在Virtualbox中指定要使用的虛擬NIC (vbox0)
開啟Virtualbox,並設定Guest OS的其中一張NIC bind到vbox0上
搞定收工! 下面是在Ubuntu下的Guest OS: FC7正在更新套件的畫面:
Install VirtualBox in Ubuntu 7.04
聽說VirtualBox非常好用,所以帽客也來嘗試裝看看,以下是帽客的安裝步驟.
Setup1. 至官網抓for Ubuntu 7.04的套件 virtualbox download
Setup2. # sudo dkpg -i virtualbox_1.5.0-24069-1_Ubuntu_feisty_i386.deb
Setup3. 發生了套件相依性的問題用apt來一解決: # sudo apt-get -f install
Setup4. 將User加入到virtualbox的group: # sudo usermod -G vboxusers -a lawrence
啟動Virtualbox: #
Setup1. 至官網抓for Ubuntu 7.04的套件 virtualbox download
Setup2. # sudo dkpg -i virtualbox_1.5.0-24069-1_Ubuntu_feisty_i386.deb
Setup3. 發生了套件相依性的問題用apt來一解決: # sudo apt-get -f install
Setup4. 將User加入到virtualbox的group: # sudo usermod -G vboxusers -a lawrence
啟動Virtualbox: #
VirtualBox
裝好了,今天先裝個FC7玩看看 :)
Friday, September 14, 2007
Linux AntiSpoofing method
寫個簡單的script來做吧! 這樣會套用到所有的interface上.
#!/bin/bash
for i in /proc/sys/net/ipv4/conf/*/rp_filter
do
echo 1 > "$i"
echo "$i"
cat `echo "$i"`
done
參考: OReilly.LPI.Linux.Certification.in.a.Nutshell.2nd.Edition
#!/bin/bash
for i in /proc/sys/net/ipv4/conf/*/rp_filter
do
echo 1 > "$i"
echo "$i"
cat `echo "$i"`
done
參考: OReilly.LPI.Linux.Certification.in.a.Nutshell.2nd.Edition
Tuesday, September 11, 2007
Setup IPSec Host to Host Tunnel Connection
1. Test Environment:
Left PC ----- Right PC
Letf PC:
IP address: 192.168.0.2/24
OS: opensuse 10
Install openswan-2.4.4-1.1
Right PC:
IP address: 192.168.0.100/24
OS: CentOS 5.0
Install openswan-2.4.9-31.el5
2.Setup procedure:
2.1 Left PC:
2.1.1 Setup PSK:
# vi /etc/ipsec.secrets
192.168.0.2 192.168.0.100 : PSK "1234567890"
192.168.0.100 192.168.0.2 : PSK "1234567890"
2.1.2 Setup IPSec:
# vi /etc/ipsec.conf
conn hosttohost
# Left security gateway, subnet behind it, nexthop toward right.
left=192.168.0.2
#leftsubnet=192.168.0.0/24
#leftnexthop=10.4.0.1
# Right security gateway, subnet behind it, nexthop toward left.
right=192.168.0.100
#rightsubnet=192.168.1.0/24
#rightnexthop=10.5.30.254
# To authorize this connection, but not actually start it,
# at startup, uncomment this.
type=tunnel
auto=add
authby=secret
2.1.3 Start IPSec
# rcipsec start
# ipsec auto --up hosttohost
2.2 Right PC:
2.2.1 Setup PSK:
# vi /etc/ipsec.secrets
192.168.0.100 192.168.0.2 : PSK "1234567890"
192.168.0.2 192.168.0.100 : PSK "1234567890"
2.2.2 Setup IPSec:
# cp /etc/ipsec.d/examples/linux-linux.conf ..
# vi /etc/ipsec.d/linux-linux.conf
conn linux-to-linux
#
# Simple use raw RSA keys
# After starting openswan, run: ipsec showhostkey --left (or --right)
# and fill in the connection similarly to the example below.
#
left=192.168.0.100
# optional
# leftsubnet=10.0.1.0/24
#leftid=@bofh.xelerance.com
#leftrsasigkey=0sAQPWTXt8DDlEhTZJ91ngNMxTSyuos6JZxXQmtRcwUl6ppUCcuuWvjXrF/qiz6eiL1LMlpGJyG1oVhtFhTaFJl7ZkF/4J1B9LCFzYxvYI97AnLuC0op5pVAZ1SZx29+aRjeMcKC4zbZ6dMMjUdn9H1gqG9rpE0MBEFNSVLEu9U8rtlz14RfxQAQ9ePj64HnGLfgJlDB0VYhKEIcRihy72bvjZ4eoX16S1EY1FgnHyrveZPxRi8sgn6Q19RytEzSmUAlGjvMDhNfenq6WCSYMeqgj0jFSArTNBQmR2QBkUG6NSOXfb+18c6jDPicGmbmWfoRx/PUJo46WiRF4RRmsxnFpbHpklILFzEJ+/k6qHVAekpVfp
# The remote user.
#
right=192.168.0.2
#rightid=@tla.xelerance.com
# optional
# rightsubnet=10.0.2.0/24
#rightrsasigkey=0sAQNxf6caKULJklYZycuo66Ko0U+iHaJUDr0QZHnG4MJ9IRNYi5H6kPxcwKIXkg+OGo+NeUyyWDEc+ox27BFYViAHQNEyBRLZu0kyE681h+cHm7lfCSy0AOEBSCyZF3aGcL8GWxVhtimpJQ4tNxXZg7tLX5sfYw8mZnUBjkHvyccIred/q3cNWbDlq2WU4TL+NBb5FnxXi9Hk/SRV7sMe56fvZuXkcJu4e2C7uocltzzF1b0BZx7yeXwHjzqAWnW/UA54fbSTvzgnrpSC+FMuhWTI1EdxcqGaOFIjGWWGV2nxg/QaPU9i8vpwFwrEEdCJTiqlbYYNudblg4vYthnVNez0/RkfZHfhAaHdbJRSaQzOu88h
authby=secret
auto=add
type=tunnel
2.2.3 Start IPSec:
# service ipsec start
# ipsec auto --up linux-to-linux
3.Verify:
Ping Right PC from Left PC and to check that traffic actually got encrypted!
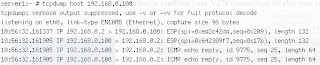
Left PC ----- Right PC
Letf PC:
IP address: 192.168.0.2/24
OS: opensuse 10
Install openswan-2.4.4-1.1
Right PC:
IP address: 192.168.0.100/24
OS: CentOS 5.0
Install openswan-2.4.9-31.el5
2.Setup procedure:
2.1 Left PC:
2.1.1 Setup PSK:
# vi /etc/ipsec.secrets
192.168.0.2 192.168.0.100 : PSK "1234567890"
192.168.0.100 192.168.0.2 : PSK "1234567890"
2.1.2 Setup IPSec:
# vi /etc/ipsec.conf
conn hosttohost
# Left security gateway, subnet behind it, nexthop toward right.
left=192.168.0.2
#leftsubnet=192.168.0.0/24
#leftnexthop=10.4.0.1
# Right security gateway, subnet behind it, nexthop toward left.
right=192.168.0.100
#rightsubnet=192.168.1.0/24
#rightnexthop=10.5.30.254
# To authorize this connection, but not actually start it,
# at startup, uncomment this.
type=tunnel
auto=add
authby=secret
2.1.3 Start IPSec
# rcipsec start
# ipsec auto --up hosttohost
2.2 Right PC:
2.2.1 Setup PSK:
# vi /etc/ipsec.secrets
192.168.0.100 192.168.0.2 : PSK "1234567890"
192.168.0.2 192.168.0.100 : PSK "1234567890"
2.2.2 Setup IPSec:
# cp /etc/ipsec.d/examples/linux-linux.conf ..
# vi /etc/ipsec.d/linux-linux.conf
conn linux-to-linux
#
# Simple use raw RSA keys
# After starting openswan, run: ipsec showhostkey --left (or --right)
# and fill in the connection similarly to the example below.
#
left=192.168.0.100
# optional
# leftsubnet=10.0.1.0/24
#leftid=@bofh.xelerance.com
#leftrsasigkey=0sAQPWTXt8DDlEhTZJ91ngNMxTSyuos6JZxXQmtRcwUl6ppUCcuuWvjXrF/qiz6eiL1LMlpGJyG1oVhtFhTaFJl7ZkF/4J1B9LCFzYxvYI97AnLuC0op5pVAZ1SZx29+aRjeMcKC4zbZ6dMMjUdn9H1gqG9rpE0MBEFNSVLEu9U8rtlz14RfxQAQ9ePj64HnGLfgJlDB0VYhKEIcRihy72bvjZ4eoX16S1EY1FgnHyrveZPxRi8sgn6Q19RytEzSmUAlGjvMDhNfenq6WCSYMeqgj0jFSArTNBQmR2QBkUG6NSOXfb+18c6jDPicGmbmWfoRx/PUJo46WiRF4RRmsxnFpbHpklILFzEJ+/k6qHVAekpVfp
# The remote user.
#
right=192.168.0.2
#rightid=@tla.xelerance.com
# optional
# rightsubnet=10.0.2.0/24
#rightrsasigkey=0sAQNxf6caKULJklYZycuo66Ko0U+iHaJUDr0QZHnG4MJ9IRNYi5H6kPxcwKIXkg+OGo+NeUyyWDEc+ox27BFYViAHQNEyBRLZu0kyE681h+cHm7lfCSy0AOEBSCyZF3aGcL8GWxVhtimpJQ4tNxXZg7tLX5sfYw8mZnUBjkHvyccIred/q3cNWbDlq2WU4TL+NBb5FnxXi9Hk/SRV7sMe56fvZuXkcJu4e2C7uocltzzF1b0BZx7yeXwHjzqAWnW/UA54fbSTvzgnrpSC+FMuhWTI1EdxcqGaOFIjGWWGV2nxg/QaPU9i8vpwFwrEEdCJTiqlbYYNudblg4vYthnVNez0/RkfZHfhAaHdbJRSaQzOu88h
authby=secret
auto=add
type=tunnel
2.2.3 Start IPSec:
# service ipsec start
# ipsec auto --up linux-to-linux
3.Verify:
Ping Right PC from Left PC and to check that traffic actually got encrypted!

Thursday, August 30, 2007
Setup a L2TP over IPSec VPN Server on Linux
Test Environment:
L2TP Client ---------- L2TP Server
L2TP Client: Windows XP SP2
L2TP Server: CentOS 5.0
IP address of L2TP Client: 10.5.30.200
IP address of L2TP Server: 10.5.30.3
必要套件:
xl2tpd-1.1.09-1.fc5.src.rpm
openswan-2.4.9-31.el5.i386.rpm
ipsec-tools* (預設已安裝)
ppp* (預設已安裝)
Setup Procedure:
1.Install RPM:
# rpm –ivh openswan*
# rpm –ivh xl2tpd* (That’s source rpm you must rebuild it)
2.Configure L2TP Server:
2.1 設定帳號與密碼:
# vi /etc/ppp/chap-secrets
lawrence * “redhat” *
2.2 設定xl2tpd設定檔:
[global]
; listen-addr = 192.168.1.98
;
;requires openswan-3.1
;ipsec saref = yes
;
;debug tunnel = yes
auth file = /etc/ppp/chap-secrets
[lns default]
ip range = 192.168.1.128-192.168.1.254
local ip = 192.168.1.99
require chap = yes
refuse pap = yes
require authentication = yes
name = LinuxVPNserver
ppp debug = yes
pppoptfile = /etc/ppp/options.xl2tpd
length bit = yes
2.3 設定/etc/ppp/options.xl2tpd
ipcp-accept-local
ipcp-accept-remote
ms-dns 192.168.1.1
ms-dns 192.168.1.3
ms-wins 192.168.1.2
ms-wins 192.168.1.4
noccp
auth
crtscts
idle 1800
#mtu 1410
#mru 1410
nodefaultroute
debug
lock
proxyarp
connect-delay 5000
logfile /var/log/xl2tpd.log
2.4 啟動L2TP Server
# service xl2tpd start; chkconfig xl2tpd on
3. 設定IPSec
3.1 PSK setting:
# vi /etc/ipsec.secrets
include /etc/ipsec.d/*.secrets
10.5.30.3 %any : PSK "1234567890"
10.5.30.3 -> Server IP address
%any -> allow all machines
格式要一模一樣,不然會出錯
3.2 設定l2tp-psk.conf
套用範例即可:
# cp /etc/ipsec.d/examples/l2tp-psk.conf /etc/ipsec.d/
# chmod 755 l2tp-psk.conf
3.3 啟動IPSec
# service ipsec start; chkconfig ipsec on
3.4 Check IPSec status
# ipsec verify
Checking your system to see if IPsec got installed and started correctly:
Version check and ipsec on-path [OK]
Linux Openswan Uopenswan-2.4.9-31.el5/K2.6.18-8.1.8.el5 (netkey)
Checking for IPsec support in kernel [OK]
NETKEY detected, testing for disabled ICMP send_redirects [OK]
NETKEY detected, testing for disabled ICMP accept_redirects [OK]
Checking for RSA private key (/etc/ipsec.d/hostkey.secrets) [OK]
Checking that pluto is running [OK]
Two or more interfaces found, checking IP forwarding [OK]
Checking NAT and MASQUERADEing [N/A]
Checking for 'ip' command [OK]
Checking for 'iptables' command [OK]
Opportunistic Encryption Support [DISABLED]
這麼一來L2TP over IPSec就成功架設起來了,如果有問題的話可查看以下的log file
/var/log/message
/var/log/secure
/var/log/xl2tpd.log
4. L2TP Client setting:
4.1新增連線
1. 開始->設定->網路連線->新增連線精靈
2. 選擇連線到公司網路(使用指定撥號或是vpn)
3. 選擇虛擬私人網路連線
4. 輸入名稱(可以隨意選)
5. 輸入VPN server IP (10.5.30.3)
4.2 修改設定
1.在安全性的分頁中->選擇進階->只勾選CHAP->可省加密
2. 點選"ipsec 設定"選項,輸入PSK(pre-shared key)
L2TP Client ---------- L2TP Server
L2TP Client: Windows XP SP2
L2TP Server: CentOS 5.0
IP address of L2TP Client: 10.5.30.200
IP address of L2TP Server: 10.5.30.3
必要套件:
xl2tpd-1.1.09-1.fc5.src.rpm
openswan-2.4.9-31.el5.i386.rpm
ipsec-tools* (預設已安裝)
ppp* (預設已安裝)
Setup Procedure:
1.Install RPM:
# rpm –ivh openswan*
# rpm –ivh xl2tpd* (That’s source rpm you must rebuild it)
2.Configure L2TP Server:
2.1 設定帳號與密碼:
# vi /etc/ppp/chap-secrets
lawrence * “redhat” *
2.2 設定xl2tpd設定檔:
[global]
; listen-addr = 192.168.1.98
;
;requires openswan-3.1
;ipsec saref = yes
;
;debug tunnel = yes
auth file = /etc/ppp/chap-secrets
[lns default]
ip range = 192.168.1.128-192.168.1.254
local ip = 192.168.1.99
require chap = yes
refuse pap = yes
require authentication = yes
name = LinuxVPNserver
ppp debug = yes
pppoptfile = /etc/ppp/options.xl2tpd
length bit = yes
2.3 設定/etc/ppp/options.xl2tpd
ipcp-accept-local
ipcp-accept-remote
ms-dns 192.168.1.1
ms-dns 192.168.1.3
ms-wins 192.168.1.2
ms-wins 192.168.1.4
noccp
auth
crtscts
idle 1800
#mtu 1410
#mru 1410
nodefaultroute
debug
lock
proxyarp
connect-delay 5000
logfile /var/log/xl2tpd.log
2.4 啟動L2TP Server
# service xl2tpd start; chkconfig xl2tpd on
3. 設定IPSec
3.1 PSK setting:
# vi /etc/ipsec.secrets
include /etc/ipsec.d/*.secrets
10.5.30.3 %any : PSK "1234567890"
10.5.30.3 -> Server IP address
%any -> allow all machines
格式要一模一樣,不然會出錯
3.2 設定l2tp-psk.conf
套用範例即可:
# cp /etc/ipsec.d/examples/l2tp-psk.conf /etc/ipsec.d/
# chmod 755 l2tp-psk.conf
3.3 啟動IPSec
# service ipsec start; chkconfig ipsec on
3.4 Check IPSec status
# ipsec verify
Checking your system to see if IPsec got installed and started correctly:
Version check and ipsec on-path [OK]
Linux Openswan Uopenswan-2.4.9-31.el5/K2.6.18-8.1.8.el5 (netkey)
Checking for IPsec support in kernel [OK]
NETKEY detected, testing for disabled ICMP send_redirects [OK]
NETKEY detected, testing for disabled ICMP accept_redirects [OK]
Checking for RSA private key (/etc/ipsec.d/hostkey.secrets) [OK]
Checking that pluto is running [OK]
Two or more interfaces found, checking IP forwarding [OK]
Checking NAT and MASQUERADEing [N/A]
Checking for 'ip' command [OK]
Checking for 'iptables' command [OK]
Opportunistic Encryption Support [DISABLED]
這麼一來L2TP over IPSec就成功架設起來了,如果有問題的話可查看以下的log file
/var/log/message
/var/log/secure
/var/log/xl2tpd.log
4. L2TP Client setting:
4.1新增連線
1. 開始->設定->網路連線->新增連線精靈
2. 選擇連線到公司網路(使用指定撥號或是vpn)
3. 選擇虛擬私人網路連線
4. 輸入名稱(可以隨意選)
5. 輸入VPN server IP (10.5.30.3)
4.2 修改設定
1.在安全性的分頁中->選擇進階->只勾選CHAP->可省加密
2. 點選"ipsec 設定"選項,輸入PSK(pre-shared key)
Thursday, August 23, 2007
Shell Script: 計算CPU的使用率
Monday, August 20, 2007
Setup a POP3 Server that enables SSL/TLS function
OS: CentOS4.5
POP3 Server: dovecot
Setup procedure:
1. Edit /etc/dovecot.conf
->
protocols = pop3 pop3s
imap_listen = [::]
pop3_listen = [::]
ssl_disable = no
ssl_cert_file = /usr/share/ssl/certs/dovecot.pem
ssl_key_file = /usr/share/ssl/private/dovecot.pem
disable_plaintext_auth = no
login_dir = /var/run/dovecot-login
login = imap
login = pop3
mbox_locks = fcntl
auth = default
auth_mechanisms = plain
auth_userdb = passwd
auth_passdb = pam
auth_user = root
2. Start dovecot
# service dovecot start; chkconfig dovecot on
POP3 Server: dovecot
Setup procedure:
1. Edit /etc/dovecot.conf
->
protocols = pop3 pop3s
imap_listen = [::]
pop3_listen = [::]
ssl_disable = no
ssl_cert_file = /usr/share/ssl/certs/dovecot.pem
ssl_key_file = /usr/share/ssl/private/dovecot.pem
disable_plaintext_auth = no
login_dir = /var/run/dovecot-login
login = imap
login = pop3
mbox_locks = fcntl
auth = default
auth_mechanisms = plain
auth_userdb = passwd
auth_passdb = pam
auth_user = root
2. Start dovecot
# service dovecot start; chkconfig dovecot on
Friday, August 17, 2007
讓Linux可以讀寫NTFS磁區
帽客家裡的大黑(IBM桌機)有兩顆HDD,一顆是安裝CentOS5另一顆是Windows XP PRO SP2,所以有時開到CentOS的工作環境而想讀寫NTFS磁區時,我記得我之前只解決了讀的問題,昨天上Google發現到現在連寫的問題也解決了,我真是後知後覺呀!
只要安裝好ntfs-3g與fuse後,並以下面的方法mount NTFS的磁區就可以work囉~
# mount /dev/hda7 /mnt/ntfs -t ntfs-3g
# vi /etc/fstab
->
ntfs-3g
只要安裝好ntfs-3g與fuse後,並以下面的方法mount NTFS的磁區就可以work囉~
# mount /dev/hda7 /mnt/ntfs -t ntfs-3g
# vi /etc/fstab
->
/dev/hda7 /mnt/ntfs ntfs-3g defaults 0 0官網:
ntfs-3g
Wednesday, August 15, 2007
Shell Script: 每日檢查硬碟的使用量,當到達90%時寄出Alert mail給root
1. 至/root/bin目錄下,新增一shell script的檔案,名為diskspace.sh,內容如下:
#!/bin/bash
df -h | grep -vE '^Filesystem|tmpfs|cdrom' | awk '{ print $5 " " $1 }' | while read output;
do
usep=$(echo $output | awk '{ print $1}' | cut -d'%' -f1 )
partition=$(echo $output | awk '{ print $2 }' )
if [ $usep -ge 90 ]; then
echo "Running out of space "$partition $usep%" on $(hostname) as on $(date)" | mail -s "Alert: Almost out of disk space $usep%" root
fi
done
2. # chmod 755 diskspace.sh
3. # crontab -e
-> 10 5 * * * /root/bin/diskspace.sh
這個範例用了grep,awk與cut指令來實作,可以見得它們有多好用了 :)
參考來源: http://www.cyberciti.biz/tips/shell-script-to-watch-the-disk-space.html
#!/bin/bash
df -h | grep -vE '^Filesystem|tmpfs|cdrom' | awk '{ print $5 " " $1 }' | while read output;
do
usep=$(echo $output | awk '{ print $1}' | cut -d'%' -f1 )
partition=$(echo $output | awk '{ print $2 }' )
if [ $usep -ge 90 ]; then
echo "Running out of space "$partition $usep%" on $(hostname) as on $(date)" | mail -s "Alert: Almost out of disk space $usep%" root
fi
done
2. # chmod 755 diskspace.sh
3. # crontab -e
-> 10 5 * * * /root/bin/diskspace.sh
這個範例用了grep,awk與cut指令來實作,可以見得它們有多好用了 :)
參考來源: http://www.cyberciti.biz/tips/shell-script-to-watch-the-disk-space.html
Thursday, August 09, 2007
Friday, August 03, 2007
Setup a mail server that enables smtp auth function
Mail Server IP address: 192.168.1.254
OS: OpenSUSE 10
Setup procedure:
1. Setup Hostname (server1.example.com)
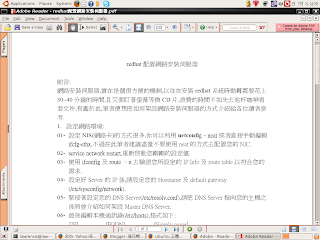
# vi /etc/HOSTNAME
server1.example.com
# vi /etc/hosts
192.168.1.254 server1.example.com server1
2. Setup DNS Server:
# vi /etc/named.conf
# cd /var/lib/named/master
# vi example.com.zone
# chown root.named example.com.zone
# rcnamed start
# chkconfig named on
# vi /etc/resolv.conf
3. Setup Postfix mail server and enables smtp auth function:
# vi /etc/postfix/main.cf
# rcsaslauthd start
# chkconfig saslauthd on
# rcpostfix start
# chkconfig postfix on
4. Enable pop3 server:
# chkconfig qpopper on
# rcxinetd restart
5. Add user account:
# useradd -m lawrence
# passwd lawrence
-> Finished
OS: OpenSUSE 10
Setup procedure:
1. Setup Hostname (server1.example.com)
# vi /etc/HOSTNAME
server1.example.com
# vi /etc/hosts
192.168.1.254 server1.example.com server1
2. Setup DNS Server:
# vi /etc/named.conf
| Configure: |
options { # The directory statement defines the name server's working directory directory "/var/lib/named"; # Write dump and statistics file to the log subdirectory. The # pathenames are relative to the chroot jail. dump-file "/var/log/named_dump.db"; statistics-file "/var/log/named.stats"; # The forwarders record contains a list of servers to which queries # should be forwarded. Enable this line and modify the IP address to # your provider's name server. Up to three servers may be listed. #forwarders { 192.0.2.1; 192.0.2.2; }; # Enable the next entry to prefer usage of the name server declared in # the forwarders section. #forward first; # The listen-on record contains a list of local network interfaces to # listen on. Optionally the port can be specified. Default is to # listen on all interfaces found on your system. The default port is # 53. #listen-on port 53 { 127.0.0.1; }; # The listen-on-v6 record enables or disables listening on IPv6 # interfaces. Allowed values are 'any' and 'none' or a list of # addresses. listen-on-v6 { any; }; # The next three statements may be needed if a firewall stands between # the local server and the internet. #query-source address * port 53; #transfer-source * port 53; #notify-source * port 53; # The allow-query record contains a list of networks or IP addresses # to accept and deny queries from. The default is to allow queries # from all hosts. #allow-query { 127.0.0.1; }; # If notify is set to yes (default), notify messages are sent to other # name servers when the the zone data is changed. Instead of setting # a global 'notify' statement in the 'options' section, a separate # 'notify' can be added to each zone definition. notify no; }; zone "." in { type hint; file "root.hint"; }; zone "localhost" in { type master; file "localhost.zone"; }; zone "0.0.127.in-addr.arpa" in { type master; file "127.0.0.zone"; }; zone "example.com" { type master; file "master/example.com.zone"; }; |
# cd /var/lib/named/master
# vi example.com.zone
| Configure: |
$TTL 1W @ IN SOA server1.example.com. root.server1.example.com. ( 42 ; serial (d. adams) 2D ; refresh 4H ; retry 6W ; expiry 1W ) ; minimum IN NS server1 server1 IN A 192.168.1.254 |
# chown root.named example.com.zone
# rcnamed start
# chkconfig named on
# vi /etc/resolv.conf
| Configure: |
nameserver 192.168.1.254 |
3. Setup Postfix mail server and enables smtp auth function:
# vi /etc/postfix/main.cf
| Configure: |
queue_directory = /var/spool/postfix command_directory = /usr/sbin daemon_directory = /usr/lib/postfix mail_owner = postfix unknown_local_recipient_reject_code = 550 mynetworks = 127.0.0.0/8 debug_peer_level = 2 debugger_command = PATH=/bin:/usr/bin:/usr/local/bin:/usr/X11R6/bin xxgdb $daemon_directory/$process_name $process_id & sleep 5 sendmail_path = /usr/sbin/sendmail newaliases_path = /usr/bin/newaliases mailq_path = /usr/bin/mailq setgid_group = maildrop html_directory = /usr/share/doc/packages/postfix/html manpage_directory = /usr/share/man sample_directory = /usr/share/doc/packages/postfix/samples readme_directory = /usr/share/doc/packages/postfix/README_FILES inet_protocols = all biff = no mail_spool_directory = /var/mail canonical_maps = hash:/etc/postfix/canonical virtual_alias_maps = hash:/etc/postfix/virtual virtual_alias_domains = hash:/etc/postfix/virtual relocated_maps = hash:/etc/postfix/relocated transport_maps = hash:/etc/postfix/transport sender_canonical_maps = hash:/etc/postfix/sender_canonical masquerade_exceptions = root masquerade_classes = envelope_sender, header_sender, header_recipient myhostname = server1.example.com program_directory = /usr/lib/postfix inet_interfaces = all masquerade_domains = mydestination = $myhostname, localhost.$mydomain defer_transports = disable_dns_lookups = no relayhost = mailbox_command = mailbox_transport = strict_8bitmime = no disable_mime_output_conversion = no smtpd_sender_restrictions = hash:/etc/postfix/access smtpd_client_restrictions = smtpd_helo_required = no smtpd_helo_restrictions = strict_rfc821_envelopes = no smtpd_recipient_restrictions = permit_mynetworks,reject_unauth_destination smtp_sasl_auth_enable = no smtpd_sasl_auth_enable = no smtpd_use_tls = no smtp_use_tls = no alias_maps = hash:/etc/aliases mailbox_size_limit = 0 message_size_limit = 10240000 smtpd_sasl_auth_enable = yes smtpd_sasl_security_options = noanonymous broken_sasl_auth_clients = yes smtpd_recipient_restrictions = permit_sasl_authenticated,permit_mynetworks,reject_unauth_destination |
# rcsaslauthd start
# chkconfig saslauthd on
# rcpostfix start
# chkconfig postfix on
4. Enable pop3 server:
# chkconfig qpopper on
# rcxinetd restart
5. Add user account:
# useradd -m lawrence
# passwd lawrence
-> Finished
Sunday, July 29, 2007
Linux Distribution Chooser
Linux Distribution百百種,你適合那一種版本呢?嘿~現在有個網站可以幫您做個分析,帽客做完後,它推薦我用Fedora與OpenSUSE,哇!!真準呀!剛好是我最熟悉的!真好玩 :)

Linux Distribution Chooser

Linux Distribution Chooser
網路效能測試工具: iperf
最近測試的案子中,利用了一套軟體來測試網路的效能,它叫做iperf,iperf支援大多數的作業系統,如: Windows,Linux,FreeBSD,MACOSX,Solaris等等,使用上非常簡單,在你的網路環境中準備兩台電腦,各架設於兩端點間,如core switch到RD switch之間,一邊設定為iperf server,另一邊設定成iperf client,這麼一來你就可以知道core switch與RD switch之間的throughput能達到多少,它可針對TCP or UDP來做測試唷!由於命令參數挺多,所以在這邊我就不多提了,您可以至以下連結取得iperf來安裝,並參考設定範例,經過測試,iperf可以很成功的在Windows XP SP2,RHEL4/5與Ubuntu上執行。
iperf
iperf
Saturday, July 28, 2007
找RPM的好地方
以下列出帽客常去找RPM的網址:
http://rpmfind.net
http://rpm.pbone.net/
http://www.rpmseek.com/index.html
http://benjiweber.co.uk:8080/webpin/
http://rpmfind.net
http://rpm.pbone.net/
http://www.rpmseek.com/index.html
http://benjiweber.co.uk:8080/webpin/
Thursday, July 12, 2007
Crossover for Linux
今天帽客要跟大家介紹一個還不錯用的軟體,它叫做Crossover,它是一個能讓你在Linux or MAC OSX下安裝MS applcations的一套軟體。
老實說啦,很多時候迫於無耐,還是要跑跑MS的東西,比如MS office,沒辦法....大部份的公司還是用MS office,為了這樣,我只好在我的Linux下裝個MS office來用吧。
安裝Crossover,一點也不難,先至官網抓下試用版後(它是一個script file),你只要給它有x的權限後就可以安裝了,這時它會引導你一步一步完成安裝。
安裝完畢後,登出並登入X window後,你應該會在Applications選單中看見Crossover,選擇Install Windows Software,並依照它的引導,很簡單的就能安裝好一些MS下的apps,帽客在RHEL,CentOS與Ubuntu測試過都能安裝成功並執行,最後附上幾張圖給大家參考。
圖1:
圖2 Word:
圖3 Excel:
圖4 IE6.0:

老實說啦,很多時候迫於無耐,還是要跑跑MS的東西,比如MS office,沒辦法....大部份的公司還是用MS office,為了這樣,我只好在我的Linux下裝個MS office來用吧。
安裝Crossover,一點也不難,先至官網抓下試用版後(它是一個script file),你只要給它有x的權限後就可以安裝了,這時它會引導你一步一步完成安裝。
安裝完畢後,登出並登入X window後,你應該會在Applications選單中看見Crossover,選擇Install Windows Software,並依照它的引導,很簡單的就能安裝好一些MS下的apps,帽客在RHEL,CentOS與Ubuntu測試過都能安裝成功並執行,最後附上幾張圖給大家參考。
圖1:

圖2 Word:

圖3 Excel:

圖4 IE6.0:

Tuesday, July 10, 2007
Ubuntu 架設nfs server
1. Install
$ sudo apt-get install nfs-common
$ sudo apt-get install nfs-kernel-server
2. 設定 /etc/exports (For example: 將/mnt/iso share給all net使用)
$ sudo vi /etc/exports
/mnt/iso *(ro,sync)
3. 啟動 nfs server
$ sudo /etc/init.d/nfs-kernel-server start
4. 檢查
$ showmount -e localhost
成功的話應該可以看到這樣的訊息:
Export list for localhost:
/mnt/iso *
$ sudo apt-get install nfs-common
$ sudo apt-get install nfs-kernel-server
2. 設定 /etc/exports (For example: 將/mnt/iso share給all net使用)
$ sudo vi /etc/exports
/mnt/iso *(ro,sync)
3. 啟動 nfs server
$ sudo /etc/init.d/nfs-kernel-server start
4. 檢查
$ showmount -e localhost
成功的話應該可以看到這樣的訊息:
Export list for localhost:
/mnt/iso *
Sunday, July 08, 2007
Ubuntu之旅2-Install AdobeReader 7.x
Procedure:
1. 新增apt server:
1.1 加入金鑰:
$ wget -q http://medibuntu.sos-sts.com/repo/medibuntu-key.gpg -O- sudo apt-key add -
1.2 新增套件來源庫:
$ sudo vi /etc/apt/sources.list
## Medibuntu - Ubuntu 7.04 "feisty fawn" ## Please report any bug on https://launchpad.net/products/medibuntu/+bugs deb http://medibuntu.sos-sts.com/repo/ feisty free non-free deb-src http://medibuntu.sos-sts.com/repo/ feisty free non-free
2. 更新與安裝AdobeReader
$ sudo apt-get update; $ sudo apt-get install acroread
3. 新增中文套件:
3.1 download tarball file from here
3.2 解開:
$ sudo tar zxvf FontPack708_cht_i386-linux.tar.gz
3.3 安裝:
$ sudo ./install
圖:
1. 新增apt server:
1.1 加入金鑰:
$ wget -q http://medibuntu.sos-sts.com/repo/medibuntu-key.gpg -O- sudo apt-key add -
1.2 新增套件來源庫:
$ sudo vi /etc/apt/sources.list
## Medibuntu - Ubuntu 7.04 "feisty fawn" ## Please report any bug on https://launchpad.net/products/medibuntu/+bugs deb http://medibuntu.sos-sts.com/repo/ feisty free non-free deb-src http://medibuntu.sos-sts.com/repo/ feisty free non-free
2. 更新與安裝AdobeReader
$ sudo apt-get update; $ sudo apt-get install acroread
3. 新增中文套件:
3.1 download tarball file from here
3.2 解開:
$ sudo tar zxvf FontPack708_cht_i386-linux.tar.gz
3.3 安裝:
$ sudo ./install
圖:

Wednesday, June 27, 2007
Ubuntu 安裝VMware Server
帽客常常透過VMware將一台電腦當兩台用,所以當然也要試著在Ubuntu上安裝看看囉,跟RHEL與SLES不一樣的是,Ubuntu不可透過rpm來安裝唷!要用tarball file與上個path之後才能順利安裝成功,至於怎麼裝,請參考這個連結: 在Ubuntu7.04上安裝vmware server
附上一張圖,有圖有真相嘛 :p

附上一張圖,有圖有真相嘛 :p

Friday, June 22, 2007
Ubuntu之旅
人家都說用Ubuntu來當Linux Desktop是很方便的選擇,於是乎帽客我也想來體驗看看,去官網抓下Desktop版的iso後,利用我那小白把它燒成CD(只要一片就好ㄟ!),放到測試的機器安裝,嗯~果然非常之簡單,一會便裝完了。
待開機完成後,用剛剛所建立的User登入,第一件事便是來裝個Beryl玩看看,呵呵~真是方便呀!利用apt來安裝真是好用呀~~ 搞定了3D桌面後,便開始安裝各種Applications。
Amule,d4x,gFTP,k3b....都很好裝,跟以往我把RHEL3當桌面,被rpm相依性問題搞爆的痛苦來比真是太美妙了,只是在安裝gcin與stardict時有點小不順,所以先po上來記一下:
-Install stardict
# sudo apt-get install stardict
預設是沒有辭典可以用的唷,這時請到stardict官網抓下辭典,解開後將檔案搬到/usr/share/stardict/dic就可以了。
-Install gcin
# sudo apt-get install gcin
# sudo apt-get install im-switch
# im-switch -s gcin
重新登入,便可使用gcin。
待開機完成後,用剛剛所建立的User登入,第一件事便是來裝個Beryl玩看看,呵呵~真是方便呀!利用apt來安裝真是好用呀~~ 搞定了3D桌面後,便開始安裝各種Applications。
Amule,d4x,gFTP,k3b....都很好裝,跟以往我把RHEL3當桌面,被rpm相依性問題搞爆的痛苦來比真是太美妙了,只是在安裝gcin與stardict時有點小不順,所以先po上來記一下:
-Install stardict
# sudo apt-get install stardict
預設是沒有辭典可以用的唷,這時請到stardict官網抓下辭典,解開後將檔案搬到/usr/share/stardict/dic就可以了。
-Install gcin
# sudo apt-get install gcin
# sudo apt-get install im-switch
# im-switch -s gcin
重新登入,便可使用gcin。
Friday, June 15, 2007
G4Fancontrol
話說,帽客的小白開機久了就會發高燒到60度上下,非常之燙手,同時對小白的壽命也會有影響,所以我都有用散熱墊來幫忙讓它的工作溫度保持在40度上下,但是當我人在外面使用時,就不想帶著散熱墊呀!所以只好讓它發高燒。
之前Intel base的Mac有出控制風扇的軟體,心想~為何PPC沒有呀!哭~~~難道PPC的使用者就沒有明天了嗎? 哭~~~~ 不過,今天讓我找到了For PPC的風扇控制軟體,哈哈!我的小白出運囉~~ 先測試看看會不會work先。
Website: G4Fancontrol
之前Intel base的Mac有出控制風扇的軟體,心想~為何PPC沒有呀!哭~~~難道PPC的使用者就沒有明天了嗎? 哭~~~~ 不過,今天讓我找到了For PPC的風扇控制軟體,哈哈!我的小白出運囉~~ 先測試看看會不會work先。
Website: G4Fancontrol
Thursday, June 07, 2007
Final Fantasy XII:歸來之翼

最近趁有空閒的時候,將NDS上的一款遊戲Final Fantasy XII:歸來之翼破關了,整個遊戲必需使用觸碰筆操作,一開始很不習慣,但玩久了還覺得蠻有趣的!
遊戲的難度不高,幾乎給它來個大軍壓境都能輕鬆獲勝,除了後面幾關之外 :p
雖然我沒玩過PS2的FF12,但這款外傳也帶給我不少樂趣!
官方網站: http://www.square-enix.co.jp/ff12rw/
Wednesday, June 06, 2007
在RHEL5架設DNS Server
RHEL5跟以往RHEL4與RHEL3在架設DNS Server時,有些不一樣,不一樣的地方在於,ㄟ~~configure file怎麼都沒看到哩,還有預設的zone files哩,怎麼都沒有呀?!要我自己產生嗎? OH MY GOD! 那有可能呀!所幸今天在高人的指點下,找到了這些檔案身在何處呀!果然是高手高手高高手呀!
01- 安裝system-config-bind這隻套件
02- 到/usr/share/system-config-bind/profiles/下就可以找到named.conf與zone files.
03- 接下來把named.conf copy到 /var/named/chroot/etc/
04- 再把zone files copy到 /var/named/chroot/var/named/
05- 最後把將 /usr/share/doc/bind-*/sample/var/named/named.root copy到/var/named/chroot/var/named/
這樣就大功告成啦!剩下的就是自己改named.conf與新增網域正反解的zone files囉!
01- 安裝system-config-bind這隻套件
02- 到/usr/share/system-config-bind/profiles/下就可以找到named.conf與zone files.
03- 接下來把named.conf copy到 /var/named/chroot/etc/
04- 再把zone files copy到 /var/named/chroot/var/named/
05- 最後把將 /usr/share/doc/bind-*/sample/var/named/named.root copy到/var/named/chroot/var/named/
這樣就大功告成啦!剩下的就是自己改named.conf與新增網域正反解的zone files囉!
Friday, June 01, 2007
Fedora 7 出了!
今天Fedora Project release Fedora 7囉!這次的版本支援i386,x86_64 and ppc,預計今晚回家download後,安裝在IBM X24上測試看看。
如果您需要更多的資訊,請參考Fedora Project的官方網站。
Fedora Project
如果您需要更多的資訊,請參考Fedora Project的官方網站。
Fedora Project
Thursday, May 31, 2007
Linux發行者大收集
Linux發行的套件到底有幾個呀?呵~這我也不知道,以下這個網站整理了目前發行者的logo與連結(看得我眼睛都花了!)。目前看起來是352個,不過應該不止吧 :p
http://www.gridter.com/linx/linux.html
http://www.gridter.com/linx/linux.html
Tuesday, May 29, 2007
Partimage & SystemRescueCd
最近找到一個很好用的工具: Partimage,它是個類似Ghost這樣的軟體,可對分割區做備份與還原的功能(Support ReiserFS, ext2fs/ext3fs, FAT16/32: DOS and Windows, and NTFS),經過我的測試過後,它真是不錯用!快速又簡單,然後又找到了SystemRescueCd,它算是個Linux Live cd,而且它內建了許多系統救援的工具,當然Partimage也是內建於其中的囉!
Note: 當您在備份分割區時,記得要先把它umount掉唷!
Partimage: http://www.partimage.org/Main_Page
SystemRescueCd: http://www.sysresccd.org/Main_Page
Note: 當您在備份分割區時,記得要先把它umount掉唷!
Partimage: http://www.partimage.org/Main_Page
SystemRescueCd: http://www.sysresccd.org/Main_Page
Monday, May 28, 2007
Chkrootkit
擔心你的Linux system被植入後門嗎?試看看這套軟體吧!
您可以從 http://www.chkrootkit.org/download下載,目前的版本是0.47,如果您是用RHEL,Fedora or SUSE的使用者,到rpmfind.net可以下載到rpm來安裝。
您可以從 http://www.chkrootkit.org/download下載,目前的版本是0.47,如果您是用RHEL,Fedora or SUSE的使用者,到rpmfind.net可以下載到rpm來安裝。
Wednesday, May 23, 2007
在多台Linux Server上同時執行相同的commands
用multixterm這隻程式可以同時在不同的Server上,執行指令,分享出來給大家參考看看:
-安裝:
請安裝expect,expect-devel與expectk這三個套件,帽客是RHEL的愛好者,剛好在光碟片中有這三個套件。
-執行:
# multixterm -xc "ssh %n" host1 host2
-這時會跳出三個視窗,其中兩個為host1與host2的console,另一個為multixterm的主視窗,如果你要將命令同時在host1與host2執行的話,請將滑鼠移到stdin window再敲入指令就可以了。
-安裝:
請安裝expect,expect-devel與expectk這三個套件,帽客是RHEL的愛好者,剛好在光碟片中有這三個套件。
-執行:
# multixterm -xc "ssh %n" host1 host2
-這時會跳出三個視窗,其中兩個為host1與host2的console,另一個為multixterm的主視窗,如果你要將命令同時在host1與host2執行的話,請將滑鼠移到stdin window再敲入指令就可以了。
Monday, May 21, 2007
讓使用者暫時無法登入到Linux系統
Linux是個多人多工的系統,有時萬一碰到要系統升級或除錯時,最好是不要讓使用者登入到系統中,有一個很簡單的方法,可以達成這個要求:
# touch /etc/nologin
這樣一來只有root可以登入到系統中,待系統維護好了之後,再把這個檔案刪除即可。
# touch /etc/nologin
這樣一來只有root可以登入到系統中,待系統維護好了之後,再把這個檔案刪除即可。
Thursday, May 17, 2007
Windows2000下解決抓不到大硬碟容量的方法
遇到了就記一下囉:
在開始->執行中輸入regedit,在HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services \Atapi\Parameters下,建立一個DWORD值,名為EnableBigLba,数值填1。 修改後重啟機器即可。
在開始->執行中輸入regedit,在HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services \Atapi\Parameters下,建立一個DWORD值,名為EnableBigLba,数值填1。 修改後重啟機器即可。
Tuesday, May 15, 2007
利用shell script大量建立帳號
-先建立一個純文字檔(userlist),裡面存放著欲建立的user帳號,格式為 username:password,
user1:123456
user2:123456
user3:123456
-撰寫shell script如下:
#!/bin/bash
FILE=$1
for i in `awk -F: '{ print $1 }' $FILE`
do
useradd $i
grep $i $FILE | cut -d":" -f2 | passwd --stdin $i
done
-執行:
# ./mkuser.sh userlist
這樣便可大量建立帳號。
user1:123456
user2:123456
user3:123456
-撰寫shell script如下:
#!/bin/bash
FILE=$1
for i in `awk -F: '{ print $1 }' $FILE`
do
useradd $i
grep $i $FILE | cut -d":" -f2 | passwd --stdin $i
done
-執行:
# ./mkuser.sh userlist
這樣便可大量建立帳號。
Tuesday, April 17, 2007
Monday, April 16, 2007
架設OpenNMS
今天花了一點時間來架設OpenNMS,想說以後可以用它來monitor Lab network,不料卡在某個環節,上網找到了opennms的官方說明文件,發現到原來是書中漏掉了一個設定,頓時......不知該說些什麼...... 官方的說明文件寫的非常棒!感謝OpenNMS開發團隊!
OpenNMS安裝指南
OpenNMS安裝指南
Thursday, April 12, 2007
在RHEL5安裝NTOP
1.首先請先至rpmfind.net抓取給RHEL5所使用的NTOP,筆者的系統少安裝了glib套件,故自己抓下source rpm 來rebuild。
[root@new-host-6 tmp]# rpm -ivh ntop-3.2-2.el5.rf.i386.rpm
warning: ntop-3.2-2.el5.rf.i386.rpm: Header V3 DSA signature: NOKEY, key ID 6b8d79e6
error: Failed dependencies:
libglib-1.2.so.0 is needed by ntop-3.2-2.el5.rf.i386
[root@new-host-6 tmp]# rpmbuild --rebuild glib-1.2.10-15.src.rpm
Rebuild畫面跳過
[root@new-host-6 tmp]# cd /usr/src/redhat/RPMS/i386/
[root@new-host-6 i386]# ll
total 516
-rw-r--r-- 1 root root 145245 Apr 10 20:08 glib-1.2.10-15.i386.rpm
-rw-r--r-- 1 root root 236817 Apr 10 20:08 glib-debuginfo-1.2.10-15.i386.rpm
-rw-r--r-- 1 root root 129049 Apr 10 20:08 glib-devel-1.2.10-15.i386.rpm
[root@new-host-6 i386]# rpm -ivh *
Preparing... ########################################### [100%]
1:glib ########################################### [ 33%]
2:glib-debuginfo ########################################### [ 67%]
3:glib-devel ########################################### [100%]
[root@new-host-6 tmp]# rpm -ivh ntop-3.2-2.el5.rf.i386.rpm
warning: ntop-3.2-2.el5.rf.i386.rpm: Header V3 DSA signature: NOKEY, key ID 6b8d79e6
Preparing... ########################################### [100%]
1:ntop ########################################### [100%]
2.備份ntop.conf
[root@new-host-6 tmp]# cp /etc/ntop.conf /etc/ntop.conf.bak
3.建立NTOP儲存db的資料夾:
[root@new-host-6 tmp]# mkdir /var/www/html/ntop
[root@new-host-6 tmp]# chown ntop.ntop /var/www/html/ntop
4.啟動NTOP:
啟動NTOP的方法有兩種,一種是依照/etc/ntop.conf的設定並透過/etc/init.d/ntop start來啟動,另一種則是以命令列的方法啟動NTOP,第一種方法筆者有遇過啟動後一點反應也沒有,用status來看,也沒有任何的訊息,用echo $?才知道指令執行的結果是失敗的,但卻不知原因為何?於是乎,我個人偏愛用命令列的方式啟動NTOP。第一次啟動NTOP時會要求輸入帳號與密碼,請用admin/admin輸入即可。
[root@new-host-6 tmp]# ntop -P /var/www/html/ntop/ -u nobody
啟動畫面跳過,跑到一半時會要求輸入密碼
ntop startup - waiting for user response!
Please enter the password for the admin user:
Please enter the password again:
5.瀏覽NTOP website:
預設的port為3000,如果您要自訂port的話,請在啟動NTOP時,加上一個參數,-w 比如說如果我要把它改成6000的話,可以這樣做: ntop –P /var/www/html/ntop –u nobody –w 6000
接下來開啟瀏覽器,輸入 http://IP address:3000,就可以看到NTOP的流量統計的網頁。
後記:
更多有關於NTOP的參數,請參考man page。
[root@new-host-6 tmp]# rpm -ivh ntop-3.2-2.el5.rf.i386.rpm
warning: ntop-3.2-2.el5.rf.i386.rpm: Header V3 DSA signature: NOKEY, key ID 6b8d79e6
error: Failed dependencies:
libglib-1.2.so.0 is needed by ntop-3.2-2.el5.rf.i386
[root@new-host-6 tmp]# rpmbuild --rebuild glib-1.2.10-15.src.rpm
Rebuild畫面跳過
[root@new-host-6 tmp]# cd /usr/src/redhat/RPMS/i386/
[root@new-host-6 i386]# ll
total 516
-rw-r--r-- 1 root root 145245 Apr 10 20:08 glib-1.2.10-15.i386.rpm
-rw-r--r-- 1 root root 236817 Apr 10 20:08 glib-debuginfo-1.2.10-15.i386.rpm
-rw-r--r-- 1 root root 129049 Apr 10 20:08 glib-devel-1.2.10-15.i386.rpm
[root@new-host-6 i386]# rpm -ivh *
Preparing... ########################################### [100%]
1:glib ########################################### [ 33%]
2:glib-debuginfo ########################################### [ 67%]
3:glib-devel ########################################### [100%]
[root@new-host-6 tmp]# rpm -ivh ntop-3.2-2.el5.rf.i386.rpm
warning: ntop-3.2-2.el5.rf.i386.rpm: Header V3 DSA signature: NOKEY, key ID 6b8d79e6
Preparing... ########################################### [100%]
1:ntop ########################################### [100%]
2.備份ntop.conf
[root@new-host-6 tmp]# cp /etc/ntop.conf /etc/ntop.conf.bak
3.建立NTOP儲存db的資料夾:
[root@new-host-6 tmp]# mkdir /var/www/html/ntop
[root@new-host-6 tmp]# chown ntop.ntop /var/www/html/ntop
4.啟動NTOP:
啟動NTOP的方法有兩種,一種是依照/etc/ntop.conf的設定並透過/etc/init.d/ntop start來啟動,另一種則是以命令列的方法啟動NTOP,第一種方法筆者有遇過啟動後一點反應也沒有,用status來看,也沒有任何的訊息,用echo $?才知道指令執行的結果是失敗的,但卻不知原因為何?於是乎,我個人偏愛用命令列的方式啟動NTOP。第一次啟動NTOP時會要求輸入帳號與密碼,請用admin/admin輸入即可。
[root@new-host-6 tmp]# ntop -P /var/www/html/ntop/ -u nobody
啟動畫面跳過,跑到一半時會要求輸入密碼
ntop startup - waiting for user response!
Please enter the password for the admin user:
Please enter the password again:
5.瀏覽NTOP website:
預設的port為3000,如果您要自訂port的話,請在啟動NTOP時,加上一個參數,-w 比如說如果我要把它改成6000的話,可以這樣做: ntop –P /var/www/html/ntop –u nobody –w 6000
接下來開啟瀏覽器,輸入 http://IP address:3000,就可以看到NTOP的流量統計的網頁。
後記:
更多有關於NTOP的參數,請參考man page。
Tuesday, April 10, 2007
在RHEL5下實作LVM
需求:
-新增三個LVM的partition,各100M
-新增三個PV
-新增一個VG,size=100M
-新增一個LV,size=50M
-動態放大VG,size+200M
-動態放大LV,size+50M
-新增三個LVM的partition,各100M
root@new-host-6:~^G[root@new-host-6 ~]# fdisk /dev/hda
The number of cylinders for this disk is set to 1044.
There is nothing wrong with that, but this is larger than 1024,
and could in certain setups cause problems with:
1) software that runs at boot time (e.g., old versions of LILO)
2) booting and partitioning software from other OSs
(e.g., DOS FDISK, OS/2 FDISK)
Command (m for help): n
First cylinder (908-1044, default 908):
Using default value 908
Last cylinder or +size or +sizeM or +sizeK (908-1044, default 1044): +100M
Command (m for help): n
First cylinder (921-1044, default 921):
Using default value 921
Last cylinder or +size or +sizeM or +sizeK (921-1044, default 1044): +100M
Command (m for help): n
First cylinder (934-1044, default 934):
Using default value 934
Last cylinder or +size or +sizeM or +sizeK (934-1044, default 1044): +100M
Command (m for help): p
Disk /dev/hda: 8589 MB, 8589934592 bytes
255 heads, 63 sectors/track, 1044 cylinders
Units = cylinders of 16065 * 512 = 8225280 bytes
Device Boot Start End Blocks Id System
/dev/hda1 * 1 13 104391 83 Linux
/dev/hda2 14 778 6144862+ 83 Linux
/dev/hda3 779 843 522112+ 82 Linux swap / Solaris
/dev/hda4 844 1044 1614532+ 5 Extended
/dev/hda5 844 907 514048+ 83 Linux
/dev/hda6 908 920 104391 83 Linux
/dev/hda7 921 933 104391 83 Linux
/dev/hda8 934 946 104391 83 Linux
Command (m for help): t
Partition number (1-8): 6
Hex code (type L to list codes): 8e
Changed system type of partition 6 to 8e (Linux LVM)
Command (m for help): t
Partition number (1-8): 7
Hex code (type L to list codes): 8e
Changed system type of partition 7 to 8e (Linux LVM)
Command (m for help): t
Partition number (1-8): 8
Hex code (type L to list codes): 8e
Changed system type of partition 8 to 8e (Linux LVM)
Command (m for help): p
Disk /dev/hda: 8589 MB, 8589934592 bytes
255 heads, 63 sectors/track, 1044 cylinders
Units = cylinders of 16065 * 512 = 8225280 bytes
Device Boot Start End Blocks Id System
/dev/hda1 * 1 13 104391 83 Linux
/dev/hda2 14 778 6144862+ 83 Linux
/dev/hda3 779 843 522112+ 82 Linux swap / Solaris
/dev/hda4 844 1044 1614532+ 5 Extended
/dev/hda5 844 907 514048+ 83 Linux
/dev/hda6 908 920 104391 8e Linux LVM
/dev/hda7 921 933 104391 8e Linux LVM
/dev/hda8 934 946 104391 8e Linux LVM
Command (m for help): w
The partition table has been altered!
Calling ioctl() to re-read partition table.
WARNING: Re-reading the partition table failed with error 16: Device or resource busy.
The kernel still uses the old table.
The new table will be used at the next reboot.
Syncing disks.
重新開機,讓它生效!
[root@new-host-6 ~]# reboot
-新增三個PV
[root@new-host-6 ~]# pvcreate /dev/hda6
Physical volume "/dev/hda6" successfully created
[root@new-host-6 ~]# pvcreate /dev/hda7
Physical volume "/dev/hda7" successfully created
[root@new-host-6 ~]# pvcreate /dev/hda8
Physical volume "/dev/hda8" successfully created
驗證一下
[root@new-host-6 ~]# pvdisplay
--- NEW Physical volume ---
PV Name /dev/hda6
VG Name
PV Size 101.94 MB
Allocatable NO
PE Size (KByte) 0
Total PE 0
Free PE 0
Allocated PE 0
PV UUID NPXgcU-Pad8-EsG7-gFtI-hK66-8ua8-H0c78U
--- NEW Physical volume ---
PV Name /dev/hda7
VG Name
PV Size 101.94 MB
Allocatable NO
PE Size (KByte) 0
Total PE 0
Free PE 0
Allocated PE 0
PV UUID NeXk3q-RKtl-Ias2-TIO0-0gbq-IdU9-XuL5DC
--- NEW Physical volume ---
PV Name /dev/hda8
VG Name
PV Size 101.94 MB
Allocatable NO
PE Size (KByte) 0
Total PE 0
Free PE 0
Allocated PE 0
PV UUID Y9ERKn-oo61-mWj3-IOIZ-ba2p-QJID-UGzi4Q
-新增一個VG,size=100M
[root@new-host-6 ~]# vgcreate rootvg /dev/hda6
Volume group "rootvg" successfully created
驗證一下
[root@new-host-6 ~]# vgdisplay
--- Volume group ---
VG Name rootvg
System ID
Format lvm2
Metadata Areas 1
Metadata Sequence No 1
VG Access read/write
VG Status resizable
MAX LV 0
Cur LV 0
Open LV 0
Max PV 0
Cur PV 1
Act PV 1
VG Size 100.00 MB
PE Size 4.00 MB
Total PE 25
Alloc PE / Size 0 / 0
Free PE / Size 25 / 100.00 MB
VG UUID 2XpLIi-L1Cp-IbbB-cJ38-id6b-U6Qh-K4j3Gu
-新增一個LV,size=50M
[root@new-host-6 ~]# lvcreate -L +50M -n lv01 rootvg
Rounding up size to full physical extent 52.00 MB
Logical volume "lv01" created
驗證一下
[root@new-host-6 ~]# lvdisplay
--- Logical volume ---
LV Name /dev/rootvg/lv01
VG Name rootvg
LV UUID zWA1PJ-iy4L-PZcG-NgNw-eSue-7xmP-Tw2HNs
LV Write Access read/write
LV Status available
# open 0
LV Size 52.00 MB
Current LE 13
Segments 1
Allocation inherit
Read ahead sectors 0
Block device 253:0
建立一個mount point: /mnt/lvm,並將其格式化成ext3檔案格式,掛載於/mnt/lvm下
[root@new-host-6 ~]# mkdir /mnt/lvm
[root@new-host-6 ~]# mke2fs -j /dev/rootvg/lv01
mke2fs 1.39 (29-May-2006)
Filesystem label=
OS type: Linux
Block size=1024 (log=0)
Fragment size=1024 (log=0)
13328 inodes, 53248 blocks
2662 blocks (5.00%) reserved for the super user
First data block=1
Maximum filesystem blocks=54525952
7 block groups
8192 blocks per group, 8192 fragments per group
1904 inodes per group
Superblock backups stored on blocks:
8193, 24577, 40961
Writing inode tables: done
Creating journal (4096 blocks): done
Writing superblocks and filesystem accounting information: done
This filesystem will be automatically checked every 20 mounts or
180 days, whichever comes first. Use tune2fs -c or -i to override.
[root@new-host-6 ~]# mount /dev/rootvg/lv01 /mnt/lvm/
[root@new-host-6 ~]# df -h
Filesystem Size Used Avail Use% Mounted on
/dev/hda2 5.7G 2.9G 2.6G 53% /
/dev/hda1 99M 9.8M 84M 11% /boot
tmpfs 125M 0 125M 0% /dev/shm
/dev/hda5 487M 11M 451M 3% /home
/dev/mapper/rootvg-lv01
51M 4.9M 43M 11% /mnt/lvm
Copy一些檔案到此目錄下,以供等會驗證動態放大檔案系統時,資料不會消失
[root@new-host-6 ~]# cp -r /boot/ /mnt/lvm/
[root@new-host-6 ~]# cd /mnt/lvm/
[root@new-host-6 lvm]# ll
total 13
drwxr-xr-x 4 root root 1024 Apr 10 20:17 boot
drwx------ 2 root root 12288 Apr 10 20:15 lost+found
[root@new-host-6 lvm]#
-動態放大VG,size+200M
[root@new-host-6 lvm]# vgextend rootvg /dev/hda7 /dev/hda8
Volume group "rootvg" successfully extended
驗證一下
[root@new-host-6 lvm]# vgdisplay
--- Volume group ---
VG Name rootvg
System ID
Format lvm2
Metadata Areas 3
Metadata Sequence No 3
VG Access read/write
VG Status resizable
MAX LV 0
Cur LV 1
Open LV 1
Max PV 0
Cur PV 3
Act PV 3
VG Size 300.00 MB
PE Size 4.00 MB
Total PE 75
Alloc PE / Size 13 / 52.00 MB
Free PE / Size 62 / 248.00 MB
VG UUID 2XpLIi-L1Cp-IbbB-cJ38-id6b-U6Qh-K4j3Gu
-動態放大LV,size+50M
[root@new-host-6 lvm]# lvextend -L +50M /dev/rootvg/lv01
Rounding up size to full physical extent 52.00 MB
Extending logical volume lv01 to 104.00 MB
Logical volume lv01 successfully resized
驗證一下
[root@new-host-6 lvm]# lvdisplay
--- Logical volume ---
LV Name /dev/rootvg/lv01
VG Name rootvg
LV UUID zWA1PJ-iy4L-PZcG-NgNw-eSue-7xmP-Tw2HNs
LV Write Access read/write
LV Status available
# open 1
LV Size 104.00 MB
Current LE 26
Segments 2
Allocation inherit
Read ahead sectors 0
Block device 253:0
[root@new-host-6 lvm]# df -h
Filesystem Size Used Avail Use% Mounted on
/dev/hda2 5.7G 2.9G 2.6G 53% /
/dev/hda1 99M 9.8M 84M 11% /boot
tmpfs 125M 0 125M 0% /dev/shm
/dev/hda5 487M 11M 451M 3% /home
/dev/mapper/rootvg-lv01
51M 9.1M 39M 20% /mnt/lvm
此時因為還沒執行線上更新大小的動作,所以磁區大小還不會放大喔!
這裡跟RHEL4不同,改用resize2fs 來線上更新
[root@new-host-6 lvm]# resize2fs /dev/rootvg/lv01
resize2fs 1.39 (29-May-2006)
Filesystem at /dev/rootvg/lv01 is mounted on /mnt/lvm; on-line resizing required
Performing an on-line resize of /dev/rootvg/lv01 to 106496 (1k) blocks.
The filesystem on /dev/rootvg/lv01 is now 106496 blocks long.
[root@new-host-6 lvm]# df -h
Filesystem Size Used Avail Use% Mounted on
/dev/hda2 5.7G 2.9G 2.6G 53% /
/dev/hda1 99M 9.8M 84M 11% /boot
tmpfs 125M 0 125M 0% /dev/shm
/dev/hda5 487M 11M 451M 3% /home
/dev/mapper/rootvg-lv01
101M 9.5M 87M 10% /mnt/lvm
[root@new-host-6 lvm]# cd /mnt/lvm/
[root@new-host-6 lvm]# ll
total 13
drwxr-xr-x 4 root root 1024 Apr 10 20:17 boot
drwx------ 2 root root 12288 Apr 10 20:15 lost+found
資料沒有遺失,磁區確成功放大了!
-新增三個LVM的partition,各100M
-新增三個PV
-新增一個VG,size=100M
-新增一個LV,size=50M
-動態放大VG,size+200M
-動態放大LV,size+50M
-新增三個LVM的partition,各100M
root@new-host-6:~^G[root@new-host-6 ~]# fdisk /dev/hda
The number of cylinders for this disk is set to 1044.
There is nothing wrong with that, but this is larger than 1024,
and could in certain setups cause problems with:
1) software that runs at boot time (e.g., old versions of LILO)
2) booting and partitioning software from other OSs
(e.g., DOS FDISK, OS/2 FDISK)
Command (m for help): n
First cylinder (908-1044, default 908):
Using default value 908
Last cylinder or +size or +sizeM or +sizeK (908-1044, default 1044): +100M
Command (m for help): n
First cylinder (921-1044, default 921):
Using default value 921
Last cylinder or +size or +sizeM or +sizeK (921-1044, default 1044): +100M
Command (m for help): n
First cylinder (934-1044, default 934):
Using default value 934
Last cylinder or +size or +sizeM or +sizeK (934-1044, default 1044): +100M
Command (m for help): p
Disk /dev/hda: 8589 MB, 8589934592 bytes
255 heads, 63 sectors/track, 1044 cylinders
Units = cylinders of 16065 * 512 = 8225280 bytes
Device Boot Start End Blocks Id System
/dev/hda1 * 1 13 104391 83 Linux
/dev/hda2 14 778 6144862+ 83 Linux
/dev/hda3 779 843 522112+ 82 Linux swap / Solaris
/dev/hda4 844 1044 1614532+ 5 Extended
/dev/hda5 844 907 514048+ 83 Linux
/dev/hda6 908 920 104391 83 Linux
/dev/hda7 921 933 104391 83 Linux
/dev/hda8 934 946 104391 83 Linux
Command (m for help): t
Partition number (1-8): 6
Hex code (type L to list codes): 8e
Changed system type of partition 6 to 8e (Linux LVM)
Command (m for help): t
Partition number (1-8): 7
Hex code (type L to list codes): 8e
Changed system type of partition 7 to 8e (Linux LVM)
Command (m for help): t
Partition number (1-8): 8
Hex code (type L to list codes): 8e
Changed system type of partition 8 to 8e (Linux LVM)
Command (m for help): p
Disk /dev/hda: 8589 MB, 8589934592 bytes
255 heads, 63 sectors/track, 1044 cylinders
Units = cylinders of 16065 * 512 = 8225280 bytes
Device Boot Start End Blocks Id System
/dev/hda1 * 1 13 104391 83 Linux
/dev/hda2 14 778 6144862+ 83 Linux
/dev/hda3 779 843 522112+ 82 Linux swap / Solaris
/dev/hda4 844 1044 1614532+ 5 Extended
/dev/hda5 844 907 514048+ 83 Linux
/dev/hda6 908 920 104391 8e Linux LVM
/dev/hda7 921 933 104391 8e Linux LVM
/dev/hda8 934 946 104391 8e Linux LVM
Command (m for help): w
The partition table has been altered!
Calling ioctl() to re-read partition table.
WARNING: Re-reading the partition table failed with error 16: Device or resource busy.
The kernel still uses the old table.
The new table will be used at the next reboot.
Syncing disks.
重新開機,讓它生效!
[root@new-host-6 ~]# reboot
-新增三個PV
[root@new-host-6 ~]# pvcreate /dev/hda6
Physical volume "/dev/hda6" successfully created
[root@new-host-6 ~]# pvcreate /dev/hda7
Physical volume "/dev/hda7" successfully created
[root@new-host-6 ~]# pvcreate /dev/hda8
Physical volume "/dev/hda8" successfully created
驗證一下
[root@new-host-6 ~]# pvdisplay
--- NEW Physical volume ---
PV Name /dev/hda6
VG Name
PV Size 101.94 MB
Allocatable NO
PE Size (KByte) 0
Total PE 0
Free PE 0
Allocated PE 0
PV UUID NPXgcU-Pad8-EsG7-gFtI-hK66-8ua8-H0c78U
--- NEW Physical volume ---
PV Name /dev/hda7
VG Name
PV Size 101.94 MB
Allocatable NO
PE Size (KByte) 0
Total PE 0
Free PE 0
Allocated PE 0
PV UUID NeXk3q-RKtl-Ias2-TIO0-0gbq-IdU9-XuL5DC
--- NEW Physical volume ---
PV Name /dev/hda8
VG Name
PV Size 101.94 MB
Allocatable NO
PE Size (KByte) 0
Total PE 0
Free PE 0
Allocated PE 0
PV UUID Y9ERKn-oo61-mWj3-IOIZ-ba2p-QJID-UGzi4Q
-新增一個VG,size=100M
[root@new-host-6 ~]# vgcreate rootvg /dev/hda6
Volume group "rootvg" successfully created
驗證一下
[root@new-host-6 ~]# vgdisplay
--- Volume group ---
VG Name rootvg
System ID
Format lvm2
Metadata Areas 1
Metadata Sequence No 1
VG Access read/write
VG Status resizable
MAX LV 0
Cur LV 0
Open LV 0
Max PV 0
Cur PV 1
Act PV 1
VG Size 100.00 MB
PE Size 4.00 MB
Total PE 25
Alloc PE / Size 0 / 0
Free PE / Size 25 / 100.00 MB
VG UUID 2XpLIi-L1Cp-IbbB-cJ38-id6b-U6Qh-K4j3Gu
-新增一個LV,size=50M
[root@new-host-6 ~]# lvcreate -L +50M -n lv01 rootvg
Rounding up size to full physical extent 52.00 MB
Logical volume "lv01" created
驗證一下
[root@new-host-6 ~]# lvdisplay
--- Logical volume ---
LV Name /dev/rootvg/lv01
VG Name rootvg
LV UUID zWA1PJ-iy4L-PZcG-NgNw-eSue-7xmP-Tw2HNs
LV Write Access read/write
LV Status available
# open 0
LV Size 52.00 MB
Current LE 13
Segments 1
Allocation inherit
Read ahead sectors 0
Block device 253:0
建立一個mount point: /mnt/lvm,並將其格式化成ext3檔案格式,掛載於/mnt/lvm下
[root@new-host-6 ~]# mkdir /mnt/lvm
[root@new-host-6 ~]# mke2fs -j /dev/rootvg/lv01
mke2fs 1.39 (29-May-2006)
Filesystem label=
OS type: Linux
Block size=1024 (log=0)
Fragment size=1024 (log=0)
13328 inodes, 53248 blocks
2662 blocks (5.00%) reserved for the super user
First data block=1
Maximum filesystem blocks=54525952
7 block groups
8192 blocks per group, 8192 fragments per group
1904 inodes per group
Superblock backups stored on blocks:
8193, 24577, 40961
Writing inode tables: done
Creating journal (4096 blocks): done
Writing superblocks and filesystem accounting information: done
This filesystem will be automatically checked every 20 mounts or
180 days, whichever comes first. Use tune2fs -c or -i to override.
[root@new-host-6 ~]# mount /dev/rootvg/lv01 /mnt/lvm/
[root@new-host-6 ~]# df -h
Filesystem Size Used Avail Use% Mounted on
/dev/hda2 5.7G 2.9G 2.6G 53% /
/dev/hda1 99M 9.8M 84M 11% /boot
tmpfs 125M 0 125M 0% /dev/shm
/dev/hda5 487M 11M 451M 3% /home
/dev/mapper/rootvg-lv01
51M 4.9M 43M 11% /mnt/lvm
Copy一些檔案到此目錄下,以供等會驗證動態放大檔案系統時,資料不會消失
[root@new-host-6 ~]# cp -r /boot/ /mnt/lvm/
[root@new-host-6 ~]# cd /mnt/lvm/
[root@new-host-6 lvm]# ll
total 13
drwxr-xr-x 4 root root 1024 Apr 10 20:17 boot
drwx------ 2 root root 12288 Apr 10 20:15 lost+found
[root@new-host-6 lvm]#
-動態放大VG,size+200M
[root@new-host-6 lvm]# vgextend rootvg /dev/hda7 /dev/hda8
Volume group "rootvg" successfully extended
驗證一下
[root@new-host-6 lvm]# vgdisplay
--- Volume group ---
VG Name rootvg
System ID
Format lvm2
Metadata Areas 3
Metadata Sequence No 3
VG Access read/write
VG Status resizable
MAX LV 0
Cur LV 1
Open LV 1
Max PV 0
Cur PV 3
Act PV 3
VG Size 300.00 MB
PE Size 4.00 MB
Total PE 75
Alloc PE / Size 13 / 52.00 MB
Free PE / Size 62 / 248.00 MB
VG UUID 2XpLIi-L1Cp-IbbB-cJ38-id6b-U6Qh-K4j3Gu
-動態放大LV,size+50M
[root@new-host-6 lvm]# lvextend -L +50M /dev/rootvg/lv01
Rounding up size to full physical extent 52.00 MB
Extending logical volume lv01 to 104.00 MB
Logical volume lv01 successfully resized
驗證一下
[root@new-host-6 lvm]# lvdisplay
--- Logical volume ---
LV Name /dev/rootvg/lv01
VG Name rootvg
LV UUID zWA1PJ-iy4L-PZcG-NgNw-eSue-7xmP-Tw2HNs
LV Write Access read/write
LV Status available
# open 1
LV Size 104.00 MB
Current LE 26
Segments 2
Allocation inherit
Read ahead sectors 0
Block device 253:0
[root@new-host-6 lvm]# df -h
Filesystem Size Used Avail Use% Mounted on
/dev/hda2 5.7G 2.9G 2.6G 53% /
/dev/hda1 99M 9.8M 84M 11% /boot
tmpfs 125M 0 125M 0% /dev/shm
/dev/hda5 487M 11M 451M 3% /home
/dev/mapper/rootvg-lv01
51M 9.1M 39M 20% /mnt/lvm
此時因為還沒執行線上更新大小的動作,所以磁區大小還不會放大喔!
這裡跟RHEL4不同,改用resize2fs 來線上更新
[root@new-host-6 lvm]# resize2fs /dev/rootvg/lv01
resize2fs 1.39 (29-May-2006)
Filesystem at /dev/rootvg/lv01 is mounted on /mnt/lvm; on-line resizing required
Performing an on-line resize of /dev/rootvg/lv01 to 106496 (1k) blocks.
The filesystem on /dev/rootvg/lv01 is now 106496 blocks long.
[root@new-host-6 lvm]# df -h
Filesystem Size Used Avail Use% Mounted on
/dev/hda2 5.7G 2.9G 2.6G 53% /
/dev/hda1 99M 9.8M 84M 11% /boot
tmpfs 125M 0 125M 0% /dev/shm
/dev/hda5 487M 11M 451M 3% /home
/dev/mapper/rootvg-lv01
101M 9.5M 87M 10% /mnt/lvm
[root@new-host-6 lvm]# cd /mnt/lvm/
[root@new-host-6 lvm]# ll
total 13
drwxr-xr-x 4 root root 1024 Apr 10 20:17 boot
drwx------ 2 root root 12288 Apr 10 20:15 lost+found
資料沒有遺失,磁區確成功放大了!
Todos
Mac用久了,就會安裝一堆應用程式,這時就會覺得Dock放了太多icon會覺得很亂的感覺,如果不放在Dock裡,每次要用到時又必需到應用程式資料夾去翻箱倒櫃的找,非常沒有效率,好在有Todos這套軟體,它會scan您的應用程式資料夾,並可利用快速鍵叫出應用程式選單,非常方便唷!

下載處: http://www.macupdate.com/info.php/id/22275/todos
Mac OS真是桌面環境的領導品牌呀!
下載處: http://www.macupdate.com/info.php/id/22275/todos
Mac OS真是桌面環境的領導品牌呀!
Monday, April 09, 2007
Tuesday, April 03, 2007
最近研讀的書籍
Monday, April 02, 2007
透過NTP自動更新系統時間與硬體時間
1.首先先設定時區位置為: 亞洲台灣
[root@server1 ~]# cp /usr/share/zoneinfo/Asia/Taipei /etc/localtime
cp: overwrite `/etc/localtime'? y
[root@server1 ~]# vi /etc/sysconfig/clock
ZONE="Asia/Taipei"
UTC=false
ARC=false
2.利用ntpdate更新系統時間:
[root@server1 ~]# date
Mon Apr 2 13:00:05 CST 2007
[root@server1 ~]# ntpdate time.stdtime.gov.tw
2 Apr 16:44:31 ntpdate[2904]: step time server 220.130.158.52 offset 13454.935451 sec
[root@server1 ~]# date
Mon Apr 2 16:44:32 CST 200
3.更新硬體時間:
[root@server1 ~]# hwclock –w
4.利用crontab設定每小時自動更新系統時間與硬體時間:
[root@server1 ~]# crontab –e
01 * * * * /usr/sbin/ntpdate time.stdtime.gov.tw;/sbin/hwclock -w
[root@server1 ~]# cp /usr/share/zoneinfo/Asia/Taipei /etc/localtime
cp: overwrite `/etc/localtime'? y
[root@server1 ~]# vi /etc/sysconfig/clock
ZONE="Asia/Taipei"
UTC=false
ARC=false
2.利用ntpdate更新系統時間:
[root@server1 ~]# date
Mon Apr 2 13:00:05 CST 2007
[root@server1 ~]# ntpdate time.stdtime.gov.tw
2 Apr 16:44:31 ntpdate[2904]: step time server 220.130.158.52 offset 13454.935451 sec
[root@server1 ~]# date
Mon Apr 2 16:44:32 CST 200
3.更新硬體時間:
[root@server1 ~]# hwclock –w
4.利用crontab設定每小時自動更新系統時間與硬體時間:
[root@server1 ~]# crontab –e
01 * * * * /usr/sbin/ntpdate time.stdtime.gov.tw;/sbin/hwclock -w
Monday, March 26, 2007
以SLES10快速架設閘道式防火牆
前言:
以Linux架設Firewall算是一個蠻物美價廉的方案,因為筆者在真實的環境中利用PIII這種老機器架設Firewall ,發覺還挺穩定的,使用到現在還沒發現有任何的問題,因此若您手邊有一些退役的機器,不如將它當成Firewall來用,給它個第二春吧!好了,廢話不多說,您可以參考以下的文件,快速建立一台Linux的Firewall。
概念:
這裡要介紹的是所謂的閘道式防火牆,目的在於隔開內外網路的連線,需求如下:
外部主機 -> 防火牆主機 (不可)
內部主機 -> 防火牆主機 (不可)
外部主機 -> 內部主機 (不可)
內部主機 -> 外部主機 (可, 但應只開放某些對外的連線)
事實上這種設定的方法,還說不上真正的安全!因為對內部的主機我採用的是完全信任的方案,但所謂:內賊難防!最好的方法還是要對內部主機採取安全控管,不過因為筆者是在家中自行架設並測試的,所以我就採用了較鬆散的方法,這一點請原諒。
環境:
eth0 外部網路 (10.6.7.0/24)-----Linux Firewall----- eth1內部網(172.17.2.0/24)
開啟ip_forwarding的功能:
# vi /etc/sysctl.conf
net.ipv4.ip_forward=1
# sysctl –p
# vi /etc/init.d/boot.local
sysctl –p
設定iptables的相關規則:
預設阻擋所有連線之基本原則:
# iptables –P INPUT DROP
# iptables –P FORWARD DROP
允許loopback介面的連線:
#iptables –A INPUT –i lo –j ACCEPT
阻擋非loopback介面但確是127.0.0.0/8的IP
# iptables –A INPUT –i ! lo –s 127.0.0.0/8 –j DROP
# iptables –A OUTPUT –o ! lo –s 127.0.0.0/8 –j DROP
允許後續連線:
# iptables –A INPUT –m state --state RELATED,ESTABLISHED –j ACCEPT
# iptables –A FORWARD –m state --state RELATED,ESTABLISHED –j ACCEPT
阻擋可疑的封包:
# iptables –A INPUT –m state --state INVALID –j DROP
# iptables –A FORWARD –m state --state INVALID –j DROP
阻擋TCP第一個連線非SYN類型的封包:
# iptables –A INPUT –p tcp ! –syn –m state --state NEW –j DROP
# iptables –A FORWARD –p tcp ! –syn –m state --state NEW –j DROP
允許內部主機對外的連線:
# iptables –A FORWARD –i eth1 –o eth0 –j ACCEPT
設定NAT規則:
# iptables –t nat –A POSTROUTING –o eth0 –s 172.17.2.0/24 –j MASQUERADE
以上是iptables的相關設定,第一次接觸的iptables的人可能會罵,到底你是在寫什麼東西呀!有看沒有懂,這點也是非常抱歉,網路上已經有許多先進撰寫過很多很棒的iptables規則說明與基本語法了,請您不妨利用google大神,去尋找吧!這裡講求的是快速架設,所以不會多加論述背後的原理。
辛辛苦苦打了這麼多指令,重開機是否會不見呢?答案是會的!如果您沒有將其存起來,當您重開機時是會叫苦連天的,所以請您依照以下的方法,將它先存成一個文字檔,待開機時再將它載入。
# iptables-save > /etc/sysconfig/iptables.save (將iptables的規則存成一文字檔)
# vi /etc/init.d/boot.local
iptables-restore < /etc/sysconfig/iptables.save (開機時將iptables的規則從檔案讀入)
後記:
以上便是快速架設Linux Firewall的方法,強烈建議您先懂原理再來實作將會讓您對於iptables更加了解,用起來也會順手些,畢竟iptables的語法看起來是有那麼一點小複雜。
以Linux架設Firewall算是一個蠻物美價廉的方案,因為筆者在真實的環境中利用PIII這種老機器架設Firewall ,發覺還挺穩定的,使用到現在還沒發現有任何的問題,因此若您手邊有一些退役的機器,不如將它當成Firewall來用,給它個第二春吧!好了,廢話不多說,您可以參考以下的文件,快速建立一台Linux的Firewall。
概念:
這裡要介紹的是所謂的閘道式防火牆,目的在於隔開內外網路的連線,需求如下:
外部主機 -> 防火牆主機 (不可)
內部主機 -> 防火牆主機 (不可)
外部主機 -> 內部主機 (不可)
內部主機 -> 外部主機 (可, 但應只開放某些對外的連線)
事實上這種設定的方法,還說不上真正的安全!因為對內部的主機我採用的是完全信任的方案,但所謂:內賊難防!最好的方法還是要對內部主機採取安全控管,不過因為筆者是在家中自行架設並測試的,所以我就採用了較鬆散的方法,這一點請原諒。
環境:
eth0 外部網路 (10.6.7.0/24)-----Linux Firewall----- eth1內部網(172.17.2.0/24)
開啟ip_forwarding的功能:
# vi /etc/sysctl.conf
net.ipv4.ip_forward=1
# sysctl –p
# vi /etc/init.d/boot.local
sysctl –p
設定iptables的相關規則:
預設阻擋所有連線之基本原則:
# iptables –P INPUT DROP
# iptables –P FORWARD DROP
允許loopback介面的連線:
#iptables –A INPUT –i lo –j ACCEPT
阻擋非loopback介面但確是127.0.0.0/8的IP
# iptables –A INPUT –i ! lo –s 127.0.0.0/8 –j DROP
# iptables –A OUTPUT –o ! lo –s 127.0.0.0/8 –j DROP
允許後續連線:
# iptables –A INPUT –m state --state RELATED,ESTABLISHED –j ACCEPT
# iptables –A FORWARD –m state --state RELATED,ESTABLISHED –j ACCEPT
阻擋可疑的封包:
# iptables –A INPUT –m state --state INVALID –j DROP
# iptables –A FORWARD –m state --state INVALID –j DROP
阻擋TCP第一個連線非SYN類型的封包:
# iptables –A INPUT –p tcp ! –syn –m state --state NEW –j DROP
# iptables –A FORWARD –p tcp ! –syn –m state --state NEW –j DROP
允許內部主機對外的連線:
# iptables –A FORWARD –i eth1 –o eth0 –j ACCEPT
設定NAT規則:
# iptables –t nat –A POSTROUTING –o eth0 –s 172.17.2.0/24 –j MASQUERADE
以上是iptables的相關設定,第一次接觸的iptables的人可能會罵,到底你是在寫什麼東西呀!有看沒有懂,這點也是非常抱歉,網路上已經有許多先進撰寫過很多很棒的iptables規則說明與基本語法了,請您不妨利用google大神,去尋找吧!這裡講求的是快速架設,所以不會多加論述背後的原理。
辛辛苦苦打了這麼多指令,重開機是否會不見呢?答案是會的!如果您沒有將其存起來,當您重開機時是會叫苦連天的,所以請您依照以下的方法,將它先存成一個文字檔,待開機時再將它載入。
# iptables-save > /etc/sysconfig/iptables.save (將iptables的規則存成一文字檔)
# vi /etc/init.d/boot.local
iptables-restore < /etc/sysconfig/iptables.save (開機時將iptables的規則從檔案讀入)
後記:
以上便是快速架設Linux Firewall的方法,強烈建議您先懂原理再來實作將會讓您對於iptables更加了解,用起來也會順手些,畢竟iptables的語法看起來是有那麼一點小複雜。
Thursday, March 22, 2007
OSX Startup keyboard commands help in troubleshooting
亂逛時不小心看到的,覺得挺實用所以趕緊po上來。
When troubleshooting, performing maintenance, or otherwise starting up your Mac OSX computer in an abnormal fashion, there are a few keyboard shortcuts that you may or may not know about that can help you. Below is a list of them with an explanation of what they do:
When troubleshooting, performing maintenance, or otherwise starting up your Mac OSX computer in an abnormal fashion, there are a few keyboard shortcuts that you may or may not know about that can help you. Below is a list of them with an explanation of what they do:
- X = Force Mac OS X startup
- Option = Brings up a screen with startup volume choices (slow process, may take a while)
- Option+Command+Shift+Delete = Bypass primary startup volume and seek a different startup volume (such as a CD or external disk)
- C = Start up from a CD that has a system folder
- N = Attempt to start up from a compatible network server (NetBoot)
- T = Start up in FireWire Target Disk mode (very handy for plugging your Mac into another as an external hard drive)
- Shift = start up in Safe Boot mode and temporarily disable login items and non-essential kernel extension files (Mac OS X 10.2 and later)
- Command+V = Start up in Verbose mode.
- Command+S = Start up in Single-User mode
- Command+Option+p+r = Zap PRAM. Hold down until second chime.
- Command+Option+n+v = Clear NV RAM. Similar to reset-all in Open Firmware.
- Command+Option+o+f = Boot into open firmware
- Hold mouse button down = Force eject a CD/DVD
調查利用 | (pipe) 連結各指令的執行結果
相信大家在Linux下都使用過|(pipe)來連結過指令, 比如 cat docu.txt | wc -l 可以得知docu.txt有幾行, 但是如果今天串連了許多指令,系統確告知指令不能正確被執行時該怎麼辦呢? 到底是卡在那一個了呢?
此時便可以透過PIPESTATUS這個"陣列變數"來得到每一個指令執行的結果是否正確!
看看以下的例子您便能明白:
[root@localhost ~]# cat docu.txt | wc -l
41
[root@localhost ~]# rm docu.txt
rm: remove regular file `docu.txt'? y
[root@localhost ~]# cat docu.txt | wc -l
cat: docu.txt: No such file or directory
0
[root@localhost ~]# echo ${PIPESTATUS[0]}
1
這樣應該瞭解了吧! 從這可知道各指令執行後的結果由0開始, 所以cat docu.txt的執行結果將存在PIPESTATUS[0]中,而wc -l則存放在PIPESTATUS[1]中,如此方便debug用.
Note: 指令若能正確被執行,則$?變數便會是0,非0則代表指令執行有誤,在這個例子中,您並不能以$?來找出那一段的指令執行錯誤,因為利用|(PIPE)所串連起來的指令,$?將會存放最後一個指令執行後的結果.
Note: PIPESTATUS的值將隨著每次指令的執行而異動!
此時便可以透過PIPESTATUS這個"陣列變數"來得到每一個指令執行的結果是否正確!
看看以下的例子您便能明白:
[root@localhost ~]# cat docu.txt | wc -l
41
[root@localhost ~]# rm docu.txt
rm: remove regular file `docu.txt'? y
[root@localhost ~]# cat docu.txt | wc -l
cat: docu.txt: No such file or directory
0
[root@localhost ~]# echo ${PIPESTATUS[0]}
1
這樣應該瞭解了吧! 從這可知道各指令執行後的結果由0開始, 所以cat docu.txt的執行結果將存在PIPESTATUS[0]中,而wc -l則存放在PIPESTATUS[1]中,如此方便debug用.
Note: 指令若能正確被執行,則$?變數便會是0,非0則代表指令執行有誤,在這個例子中,您並不能以$?來找出那一段的指令執行錯誤,因為利用|(PIPE)所串連起來的指令,$?將會存放最後一個指令執行後的結果.
Note: PIPESTATUS的值將隨著每次指令的執行而異動!
Wednesday, March 21, 2007
建構RHEL5的網路安裝Server
與RHEL4不一樣的是,RHEL5不需要將iso image mount起來,只要將iso image透過NFS Server export出來就可以了,所以說RHEL5變簡單了(笑~)。不過萬一您手上只有安裝光碟的時候,這怎麼辦呢? 請依以下的作法製作iso image吧!
For DVD:
# dd if=/dev/dvd of=/NFS/RHEL5/RHEL5.iso
For CD-ROMs:
# dd if=/dev/cdrom of=/NFS/RHEL5/RHEL5_diskX.iso
Note: X代表第幾片光碟。
設定並啟動NFS Server:
# vi /etc/exports
/NFS/RHEL5 *(ro,sync)
# service nfs start; chkconfig nfs on
For DVD:
# dd if=/dev/dvd of=/NFS/RHEL5/RHEL5.iso
For CD-ROMs:
# dd if=/dev/cdrom of=/NFS/RHEL5/RHEL5_diskX.iso
Note: X代表第幾片光碟。
設定並啟動NFS Server:
# vi /etc/exports
/NFS/RHEL5 *(ro,sync)
# service nfs start; chkconfig nfs on
Saturday, March 17, 2007
紅帽推出企業Linux 5 賽門鐵克來相挺-旗下儲存管理產品將支援RHEL 5
就在 紅帽 ( Red Hat )正式推出最新版旗艦作業系統 - Red Hat Enterprise Linux 5( RHEL 5)之後, 賽門鐵克 也宣布旗下儲存管理產品也將支援RHEL 5。
賽門鐵克表示,他們的Veritas Storage Foundation、Veritas Cluster Server以及Veritas NetBackup產品都將在90內完全支援紅帽最新旗艦Linux作業系統。為了協助紅帽用戶來更佳管理他們的資料中心,賽門鐵克將把開原碼Xen伺服 器虛擬工具列入RHEL 5內一起推出。
此外,賽門鐵克與紅帽也推出共同客戶服務方案,用來提供更快速更周詳的客戶支援。新的共同服務方案乃是藉由給予技術支援來讓工程師可以遠端遙控讀取賽門鐵克與紅帽的測試實驗室環境,結合雙方伺服器及儲存基礎架構來充分傳達客戶支援需求。
出處: CPRO 資傳網 http://cpro.com.tw/channel/news/content/?news_id=54431&cid=A0000
賽門鐵克表示,他們的Veritas Storage Foundation、Veritas Cluster Server以及Veritas NetBackup產品都將在90內完全支援紅帽最新旗艦Linux作業系統。為了協助紅帽用戶來更佳管理他們的資料中心,賽門鐵克將把開原碼Xen伺服 器虛擬工具列入RHEL 5內一起推出。
此外,賽門鐵克與紅帽也推出共同客戶服務方案,用來提供更快速更周詳的客戶支援。新的共同服務方案乃是藉由給予技術支援來讓工程師可以遠端遙控讀取賽門鐵克與紅帽的測試實驗室環境,結合雙方伺服器及儲存基礎架構來充分傳達客戶支援需求。
出處: CPRO 資傳網 http://cpro.com.tw/channel/news/content/?news_id=54431&cid=A0000
Friday, March 16, 2007
定期檢查系統中SUID的檔案
Linux系統中,凡具有SUID權限的檔案,可說是兩面刀呀! 好處是在某些時候可以讓user執行某些只有root可執行的檔案 (如: passwd, ping mount)~但壞處是萬一這個執行檔有"洞",就會讓有心人士有機會侵入到Linux作業系統,所以身為系統管理者的我們,必需要對SUID的檔案特別留意,也因此讓我想到,應該讓系統每天檢查SUID的檔案們是不是有被動過手腳:
-首先,在裝完OS後,先執行以下的命令:
find / -path '/proc' -prune -or -perm -u+s -exec ls -l {} \; > /tmp/suidlist-init
簡單的說就是利用find指令將除了/proc目錄外,所有具有suid權限的檔案找出來,並且存到/tmp/suidlist-init中
-撰寫scripr file:
# vi /root/bin/checksuid.sh
#!/bin/bash
LOGFILE="/tmp/suidlist-`date +%Y-%m-%d`"
RESULTFILE="/tmp/suid_check_result-`date +%Y-%m-%d`"
find / -path '/proc' -prune -or -perm -u+s -exec ls -l {} \; > $LOGFILE
diff /tmp/suidlist-init "$LOGFILE" > $RESULTFILE
mutt -s "SUID CHECK RESULT" root < $RESULTFILE
-定期每天AM 3點檢查,並將結果mail給root
#crontab -e
0 3 * * * /root/bin/checksuid.sh
這麼一來,每天收收信就可以知道目前所有具SUID檔案的狀況了!
-首先,在裝完OS後,先執行以下的命令:
find / -path '/proc' -prune -or -perm -u+s -exec ls -l {} \; > /tmp/suidlist-init
簡單的說就是利用find指令將除了/proc目錄外,所有具有suid權限的檔案找出來,並且存到/tmp/suidlist-init中
-撰寫scripr file:
# vi /root/bin/checksuid.sh
#!/bin/bash
LOGFILE="/tmp/suidlist-`date +%Y-%m-%d`"
RESULTFILE="/tmp/suid_check_result-`date +%Y-%m-%d`"
find / -path '/proc' -prune -or -perm -u+s -exec ls -l {} \; > $LOGFILE
diff /tmp/suidlist-init "$LOGFILE" > $RESULTFILE
mutt -s "SUID CHECK RESULT" root < $RESULTFILE
-定期每天AM 3點檢查,並將結果mail給root
#crontab -e
0 3 * * * /root/bin/checksuid.sh
這麼一來,每天收收信就可以知道目前所有具SUID檔案的狀況了!
Thursday, March 15, 2007
bash下array的幾種使用方法
#!/bin/bash
#一舉將變數設定到陣列中
array=(Redhat Novell MicroSoft Sun IBM HP Dell)
#利用for loop將陣列中的變數印出
for i in 0 1 2 3 4 5 6
do
echo "array[$i]=${array[$i]}"
done
#設定間隔符號為: 搭配$*將陣列的值一口氣輸出
IFS=:
echo "${array[*]}"
#設定間隔符號為換行,搭配$*將陣列的值一口氣輸出
IFS=$'\n'
echo "${array[*]}"
#將陣列中的值利用$@一口氣輸出與$*不同的是,不會將值合併成單一字串
echo "${array[@]}"
#印出陣列中有幾筆資料
echo "${#array[@]}"
執行結果:
array[0]=Redhat
array[1]=Novell
array[2]=MicroSoft
array[3]=Sun
array[4]=IBM
array[5]=HP
array[6]=Dell
Redhat:Novell:MicroSoft:Sun:IBM:HP:Dell
Redhat
Novell
MicroSoft
Sun
IBM
HP
Dell
Redhat Novell MicroSoft Sun IBM HP Dell
7
#一舉將變數設定到陣列中
array=(Redhat Novell MicroSoft Sun IBM HP Dell)
#利用for loop將陣列中的變數印出
for i in 0 1 2 3 4 5 6
do
echo "array[$i]=${array[$i]}"
done
#設定間隔符號為: 搭配$*將陣列的值一口氣輸出
IFS=:
echo "${array[*]}"
#設定間隔符號為換行,搭配$*將陣列的值一口氣輸出
IFS=$'\n'
echo "${array[*]}"
#將陣列中的值利用$@一口氣輸出與$*不同的是,不會將值合併成單一字串
echo "${array[@]}"
#印出陣列中有幾筆資料
echo "${#array[@]}"
執行結果:
array[0]=Redhat
array[1]=Novell
array[2]=MicroSoft
array[3]=Sun
array[4]=IBM
array[5]=HP
array[6]=Dell
Redhat:Novell:MicroSoft:Sun:IBM:HP:Dell
Redhat
Novell
MicroSoft
Sun
IBM
HP
Dell
Redhat Novell MicroSoft Sun IBM HP Dell
7
Wednesday, March 14, 2007
半價網
這個網站挺吸引人的,把供應商跟消費者完完全全結合在一起......
如果真得可以半價買的夢想中的商品,那是多麼地令人興奮呀!! 也因此帽客預約了Apple iMac 2.0Ghz MA590TA/A, 呵~原價42900半價21900, 能成功嗎? 期待中 =)
半價網 http://www.50100.com.tw
如果真得可以半價買的夢想中的商品,那是多麼地令人興奮呀!! 也因此帽客預約了Apple iMac 2.0Ghz MA590TA/A, 呵~原價42900半價21900, 能成功嗎? 期待中 =)
半價網 http://www.50100.com.tw
Monday, March 12, 2007
Redhat Enterprise Linux 5.0 蓄勢待發!
Redhat 計畫在美國時間3月14日推出它的旗艦作業系統最新版本 - Red Hat Enterprise Linux 5。
RHEL 5以連結伺服器虛擬與紅帽的叢集支援來整合Xen架構伺服器與儲存虛擬方案。此外,RHEL 5具有虛擬管理功能,能夠使得安裝及管理Xen虛擬機器變得更容易。新版本RHEL從Linux核心2.6.9版升級至2.6.18版,紅帽更宣稱延伸強 化了作業系統的網路與I/O子系統。
資料來源: CPRO 資傳網 http://cpro.com.tw/channel/news/content/?news_id=54344
RHEL 5以連結伺服器虛擬與紅帽的叢集支援來整合Xen架構伺服器與儲存虛擬方案。此外,RHEL 5具有虛擬管理功能,能夠使得安裝及管理Xen虛擬機器變得更容易。新版本RHEL從Linux核心2.6.9版升級至2.6.18版,紅帽更宣稱延伸強 化了作業系統的網路與I/O子系統。
資料來源: CPRO 資傳網 http://cpro.com.tw/channel/news/content/?news_id=54344
Wednesday, March 07, 2007
利用Kickstart安裝Redhat Linux
我想這不是一個很高深的技術,但確是非常實用且方便的方法,最近買了一堆IBM HP and Dell的Server,要帽客自己一台一台手動安裝Redhat嗎? 實在是沒那個美國時間, 所以就利用kickstart來幫我這麼忙囉! 帽客的作法是: 將kickstart configure file放在NFS Server上, 當然這台NFS Server也同樣是Installation Server, 待用第一片開機片開機時,打入以下的指令: linux ks=nfs:IP address:/Share folder/ks.cfg 這麼一來,人就可以不用待在機房在那邊按來按去囉!
Note: ks.cfg這個檔案是依據手動安裝時所選取的選項與設定,自行產生的範例檔, 原來的檔名與位置是在 /root/anaconda-ks.cfg.
Note: ks.cfg這個檔案是依據手動安裝時所選取的選項與設定,自行產生的範例檔, 原來的檔名與位置是在 /root/anaconda-ks.cfg.
Monday, March 05, 2007
Linux下的備份利器-cpio
說到在Linux下備份檔案,最常用的就是使用tar來備份檔案,不過有的時候在某些特定的需求下,是需要利用到其它的工具來備份,比如: 如果將來要回復*.conf的檔案時,利用tar的話就遇到瓶頸了,不過也不必擔心,還有一個好用的備份壓縮工具cpio可以幫我們達成這個需求!
1.首先,先將/etc完整備份到/tmp下:
# cd /etc;find . -print | cpio -oa > /tmp/etc_backup.cpio
2.將*.conf回復到/tmp下:
# cd /tmp; cpio -im "*.conf" < /tmp/etc_backup.cpio
附帶提一下常見的壓縮工具,它們的壓縮比(優到劣)通常是: tar.bz2 > tgz > tar > cpio > dump
1.首先,先將/etc完整備份到/tmp下:
# cd /etc;find . -print | cpio -oa > /tmp/etc_backup.cpio
2.將*.conf回復到/tmp下:
# cd /tmp; cpio -im "*.conf" < /tmp/etc_backup.cpio
附帶提一下常見的壓縮工具,它們的壓縮比(優到劣)通常是: tar.bz2 > tgz > tar > cpio > dump
Thursday, March 01, 2007
Tuesday, January 30, 2007
誰佔用我的硬碟空間??
帽客的小黑X24,用了三年多了,安裝CentOS也跑了兩年多了(都沒重灌唷!),近日覺得"/"的空間有點不大夠用了.....於是乎下達 du -csh /* 來找看看那個目錄佔用我最多的空間,看了一看覺得為何/var會如此肥大? 進到此目錄後,在用剛剛的指令檢查看看,哇! 果然讓我抓到了兇手了, /var/cache/yum竟然有700M那麼大,原來以前用yum升級套件時,忘了把抓下來的packages移除,趕緊用 yum clean all清一下,嗯~好多了!
PS 其實兇手是我自己 =.=" 趕快改寫一下crontable囉~~~
PS 其實兇手是我自己 =.=" 趕快改寫一下crontable囉~~~
Friday, January 26, 2007
NTOP
前些日子把3條ADSL合併在一台Linux的機器,當然想看看traffic的情況,本想用MRTG來看,後來想想還是用NTOP好了,NTOP的確能分析到更多的東西,但不是說MRTG不好,目前我也用MRTG monitor數10台switch的流量,跑了很久也一直很穩定,工具不分好壞能達到目的就好了!
Monday, January 22, 2007
Linux合併頻寬
上星期因為工作需求去K了一下如何用Linux合併三條ADSL線路,公司的應用真的是太吃頻寬了!
我選用CentOS搭配iproute2與iptables來做,不過.....我只能說我做對了一半.....對外都沒有問題,但是如果要透過它連到內部的FTP Server,三條線路就時通時不通了!這點就很奇怪了,讓我有點confuse...... 這樣的下法應該是work的呀.....
iptables -t nat -A PREROUTING -s eth1 -p tcp --dport 21 -j DNAT --to 192.168.1.100:21
iptables -t nat -A PREROUTING -s eth2 -p tcp --dport 21 -j DNAT --to 192.168.1.100:21
iptables -t nat -A PREROUTING -s eth3 -p tcp --dport 21 -j DNAT --to 192.168.1.100:21
我選用CentOS搭配iproute2與iptables來做,不過.....我只能說我做對了一半.....對外都沒有問題,但是如果要透過它連到內部的FTP Server,三條線路就時通時不通了!這點就很奇怪了,讓我有點confuse...... 這樣的下法應該是work的呀.....
iptables -t nat -A PREROUTING -s eth1 -p tcp --dport 21 -j DNAT --to 192.168.1.100:21
iptables -t nat -A PREROUTING -s eth2 -p tcp --dport 21 -j DNAT --to 192.168.1.100:21
iptables -t nat -A PREROUTING -s eth3 -p tcp --dport 21 -j DNAT --to 192.168.1.100:21
Friday, January 12, 2007
改變預設smtp port
SMTP default port是25,今天在裝公司某樣產品時要求要將port 25改成2500,用google找到了方法,趕快先po上來,因為這實在太少用了!
Add a line to your /etc/services:
smtp2 5000/tcp
Now edit your master.cf so the smtpd line starts with smtp2:
smtp2 inet n - n - - smtpd
service postfix restart
原文網址
Add a line to your /etc/services:
smtp2 5000/tcp
Now edit your master.cf so the smtpd line starts with smtp2:
smtp2 inet n - n - - smtpd
service postfix restart
原文網址
Monday, January 08, 2007
小小改造Mac CLI
Mac預設的CLI(console),是不支援中文且ls的輸出也是沒有顏色的,利用以下的方法可以讓CLI變成彩色且支援中文語系:
$ sudo vi /etc/bashrc
alias ll='ls -l -w -G'
alias ls='ls -w -G'
$ sudo vi /etc/bashrc
alias ll='ls -l -w -G'
alias ls='ls -w -G'
Subscribe to:
Comments (Atom)





