規格比較表:
Sunday, December 04, 2011
X10 VS P7100
最近想買類單相機呀!找了一個table比較一下各家的spec,要不是X10在資訊會價格硬又沒送東西的話,今天就會買了吧..... 看了一看P7100好像也不錯,省下來的錢還可以買一台3DS。
RAMDisk tool on Mac OSX
現在的RAM比起以往便宜了許多,多餘的記憶體空間若空閒在那邊的確是有點可惜,把RAM當disk使用不論在Linux或是Windows上都有相對應的方法與工具,當然Mac上也是有的,最簡單的工具首推TmpDisk,怎麼設定呢?那真是簡單到不行呀,不用多說看下面的截圖您必定明白。
這邊也提供MacOSX手動產生RAMdisk的方法:
最常用的就是將RAMdisk當成瀏覽器的快取,以下提供我用Google Chrome實作的步驟:
Step1. 透過TmpDisk產生RAMDisk,並且將Auto Create與Always start on login啟動。
Step2. 關閉Google Chrome。
Step3. 開啟OSX的終端機。
Step4. 將Chrome目前的快取目錄刪除。
rm -rf ~/Library/Caches/Google/Chrome/Default
Step5. 產生一個softlink將~/Library/Caches/Google/Chrome/Default連接到Step1產生的快取.
ln -s /Volumes/Chrome\ Cache/ ~/Library/Caches/Google/Chrome/Default/Volumes/Chrome\ Cache/就是我透過TmpDisk產生的快取。
Configure Apache to use SSL on CentOS5.X
預設CentOS5.X啟動Apache時,https並沒有跟著被帶起來,其實只要裝上mod_ssl這個套件後,當下次重新啟動Apache時,就會自動打開https了,而其主要的配置檔案會自動產生於/etc/httpd/conf.d/ssl.conf檔案中。
這個方法固然快速,然而如果你想手動自己來的話還是可以的。
Saturday, December 03, 2011
RuckusWireless TDC誠徵QA Engineer
敝公司目前有在找QA Engineer,有興趣的人不妨可以投履歷看看!
順便貼上一段當初看完影片後,讓我百分之百想進入RuckusWireless工作的影片,現在看起來還是很熱血。
http://www.youtube.com/watch?v=62-3m5N8X1g&feature=related
Sunday, November 06, 2011
Tips: 找尋欲編輯的檔案內容並且直接開啟
[root@centos6 etc]# vi `find /etc/ | xargs grep "vsftpd.pem" | cut -d: -f1`
Explain:
1. 在/etc folder透過find指令尋找全部的檔案。2. 透過xargs將pipe前的stdout轉變成餵給grep的參數。3. 透過cut指令做簡單的filter。4. 將`find /etc/ | xargs grep "vsftpd.pem" | cut -d: -f1`看成一個指令的輸出,餵給vi。
Tips: 查看user屬於那一個group
傳統的方法是透過/etc/group的文檔來查看user屬於哪一些group。
[root@centos6 ~]# cat /etc/group | grep rootroot:x:0:rootbin:x:1:root,bin,daemondaemon:x:2:root,bin,daemonsys:x:3:root,bin,admadm:x:4:root,adm,daemondisk:x:6:rootwheel:x:10:root
其實可以透過groups指令來查詢的。
[root@centos6 ~]# groups rootroot : root bin daemon sys adm disk wheel[root@centos6 ~]#
Saturday, November 05, 2011
於CentOS6架設FTP-SSL
如果要在Internet上開放FTP的服務給使用者使用,比較安全的做法有SFTP與FTPs,但是SFTP必需也要開放sshd,萬一OpenSSH存在系統漏洞的話,整個系統是很容易受到攻擊的!所以FTPs看起來是比較安全的應用,以下便簡單記錄怎麼在CentOS6中透過vsftpd架設FTPs。
Steps:
1. 檢查vsftpd是否有支援ssl:
[root@centos6 ~]# ldd `which vsftpd` | grep ssllibssl.so.10 => /usr/lib/libssl.so.10 (0x00af1000) -> 看到libssl則代表有支援。
2. 產生vsftpd所需要的憑證:
[root@centos6 ~]# cd /etc/pki/tls/certs/[root@centos6 certs]# make vsftpd.pem[root@centos6 certs]# cp -a vsftpd.pem /etc/vsftpd/
3. 設定vsftpd.conf:
anonymous_enable=YESlocal_enable=YESwrite_enable=YESlocal_umask=022dirmessage_enable=YESxferlog_enable=YESconnect_from_port_20=YESxferlog_file=/var/log/vsftpd.logxferlog_std_format=YESchroot_local_user=YESchroot_list_enable=YESchroot_list_file=/etc/vsftpd/chroot_list ->注意!必需要手動產生一個chroot_list的空檔listen=YESpam_service_name=vsftpduserlist_enable=YEStcp_wrappers=YESssl_enable=YESallow_anon_ssl=NOforce_local_data_ssl=YESforce_local_logins_ssl=YESssl_tlsv1=YESssl_sslv2=NOssl_sslv3=NOrsa_cert_file=/etc/vsftpd/vsftpd.pem
4. 啟動vsftpd
[root@centos6 vsftpd]# /etc/init.d/vsftpd restart正在關閉 vsftpd: [ 確定 ]正在啟動 vsftpd 中的 vsftpd: [ 確定 ][root@centos6 vsftpd]#
5. 在OSX透過Cyperduck測試:
5.1 設定連線為FTP-SSL
5.2 輸入FTP Server的IP address,系統會警告一個不被信任的憑證,當然此憑證是我剛剛產生的,所以要信任它囉:
大功告成!
Friday, November 04, 2011
透過網路安裝RHEL6
其實做法跟RHEL5一樣,只是與RHEL5不同的是開機時沒有boot:的提示,以下透過CentOS6簡單演練一下:
Steps:
1. 放入CentOS6的開機光碟,但是與RHEL5不一樣的是沒有boot:的提示,取而代之的是grub直接帶出以下的選項:
2. 按下ESC帶出boot: 並且輸入linux askmethod叫系統帶出安裝的方法。
3. 選擇語系:
4. 選擇鍵盤的配置:
5. 選擇安裝的方法,此例子選擇來源為NFS Server:
6. 設定IP address:
7. 設定NFS Server:
8. 之後anaconda就可以順利啟動了:
Tuesday, October 11, 2011
在Linux中可媲美foobar的播放器: DeadBeef
如果對聽音樂很注重"品質"的朋友一定聽說過foobar2000這套軟體,小弟不才是經過公司同事的介紹後才認識到它,但是瘋狂帽客真的不是叫假的,我是很不習慣使用Windows的使用者,於是今天想找看看有沒有可媲美foobar2000的軟體,所幸GNU tools是有的,它叫做DeadBeef,死牛?喔喔~這名稱有點可怕哩,一開始以為是教你怎麼把一隻活生生的牛處理掉了...... 忽然想到LPIC封面的那隻牛 XD。
經過實測,把檔案放到ramdisk透過deadbeef來聽,感覺上真的有比Rhythmbox帶給我更不同的感受,以下列出我的測試設備/條件:
1. 作業系統: OpenSUSE 11.4 X86_642. 耳機: AKG K5143. Deadbeef: 0.5.1-1
說說看如何安裝Deadbeef到OpenSUSE 11.4吧。
1. 至Packman搜尋deadbeef(http://packman.links2linux.org/package/deadbeef/251257)2. 安裝libzip.so.1()(64bit): # zyppe in libzip.so.1\(\)\(64bit\)3. 安裝deadbeef: # rpm -ivh deadbeef*rpm
接下來就把音樂檔案放到/dev/shm(ramdisk)中透過Deadbeef來播放看看吧!
Thursday, October 06, 2011
Wednesday, September 28, 2011
Upgrade CentOS6 to CentOS6.x
RHEL6.1已經出來一陣子了, 但是CentOS似乎沒有趕上? 一直停留在6.0, 我們該懷疑CentOS不再繼續提供更新了嗎? 喔~不! CentOS team還是有持續努力的! 只要裝上一個extra repository就可以將CentOS6.0升級到CentOS6.1了.
Steps:
# yum install centos-release-cr# yum update
強烈建議每位CentOS users一定要裝上這個extra repository才能繼續讓你的CentOS6頭好壯壯.
Tuesday, September 27, 2011
檢查MacOSX的partition layout
MacOSX沒有fdisk的指令,但是還是有類似的指令的,其指令如下:
# diskutil list/dev/disk0#: TYPE NAME SIZE IDENTIFIER0: GUID_partition_scheme *160.0 GB disk01: EFI 209.7 MB disk0s12: Apple_HFS Macintosh 60.2 GB disk0s23: Apple_HFS Data 99.4 GB disk0s3/dev/disk1#: TYPE NAME SIZE IDENTIFIER0: *8.0 GB disk1/dev/disk2#: TYPE NAME SIZE IDENTIFIER0: Garmin-Asus *3.3 GB disk2
話說diskutil還真是MacOSX下的好工具呀!
Sunday, September 04, 2011
Linux上的網路流量監控程式iftop
在Linux上我常使用iptraf去監控本機的網路流量,然而今天又發現到了另一套簡單而有用的程式也可以在Linux上監控流量,它叫做iftop
以下是在CentOS6中的安裝與使用:
1. 抓取source:
# wget ftp://rpmfind.net/linux/dag/redhat/el6/en/i386/dag/RPMS/iftop-0.17-1.el6.rf.i686.rpm(這是i386的版本 for CentOS6)
2. 安裝:
# rpm -ivh iftop*
3. 使用:
# iftop。
4. 加上-P,顯示port number:
More parameters:
[root@centos6 ~]# iftop -h
iftop: display bandwidth usage on an interface by host
Synopsis: iftop -h | [-npbBP] [-i interface] [-f filter code] [-N net/mask]
-h display this message
-n don't do hostname lookups
-N don't convert port numbers to services
-p run in promiscuous mode (show traffic between other
hosts on the same network segment)
-b don't display a bar graph of traffic
-B Display bandwidth in bytes
-i interface listen on named interface
-f filter code use filter code to select packets to count
(default: none, but only IP packets are counted)
-F net/mask show traffic flows in/out of network
-P show ports as well as hosts
-m limit sets the upper limit for the bandwidth scale
-c config file specifies an alternative configuration file
iftop, version 0.17
copyright (c) 2002 Paul Warren and contributors
[root@centos6 ~]#
Wednesday, August 24, 2011
Iperf under IPv6 mode
Prepare Iperf version 1.6.3 or later.
Server side:
iperf -s -V
Client side:
iperf -c [IPv6 IPaddress]-V
That's all.
Saturday, July 30, 2011
BackTrack Linux 5
從事資安相關領域的人員應該有聽說過BackTrack這套Linux distro吧? 這套整合針對網路設備與系統偵測的各種資安與壓力測試工具的Linux distro的確替我省去了很多找尋與安裝軟體的時間, 目前BT5有for i386, x86_64與ARM的版本, 於download時可以選擇你偏好的desktop, VM image or ISO.
BT是based on Ubuntu, 所以使用起來沒有太大的難度, 剩下的就是針對各個軟體學習如何使用了.
我常用的hping2, hping3, Nessus, nmap, netcat, tcpreplay, tcpdump, wireshark...等等都有內建於其中, 然而還有更多工具是我沒用過的, BT果然是一套好的distro來測試網路設備或系統漏洞, 但是若拿它來做非法的事情, 可就不是我推薦的了.
RHEL6 Clone distro
除了CentOS外, 目前還有兩套頗受好評的Red Hat clone版 , 分別是Oracle Linux與Scientific Linux, 目前這兩套distro都已經release 6.1的clone版本了, 老牌的CentOS目前只有追到6.0.
Sunday, July 24, 2011
Linux Kernel 3.0 has been released!
Linux Kernel 3.0釋出了, 請到www.kernel.org瞧瞧吧! Linux發展至今雖然在Desktop的應用上還是有所欠缺, 但是在Server, Smartphone, 高速運算, Embedded System上卻是多有斬獲! 因此讓我們繼續朝向Linux Kernel 3.0前進吧!
Tuesday, July 12, 2011
How to fix Wireshark no interfaces error on OSX
That's simple, please see it below:
# sudo chown username/dev/bpf*
Monday, July 11, 2011
CentOS 6.0 now available
經過漫長的等待(Since November of 2010),CentOS終於release 6.0了,必需給它一個讚。
The CentOS team is pleased to announce the immediate availability of CentOS-6.0 for i386 and x86_64 Architectures.
CentOS-6.0 is based on the upstream release EL 6.0 and includes
packages from all variants. All upstream repositories have been combined into one, to make it easier for end users to work with.
There are some important changes to this release compared with the previous versions of CentOS and we highly recommend reading this announcement along with the Release Notes.
There are no CD images being released with CentOS-6, however we have some CD variants in the pipeline.
Since upstream has a 6.1 version already released, we will be using a Continous Release repository for 6.0 to bring all 6.1 and post 6.1 security updates to all 6.0 users, till such time as CentOS-6.1 is released itself.
LiveCDs and LiveDVDs for i386 and x86_64 will be released the
next few days. These will bring in the ability to directly install from the live media.
There will also be a minimal install CD, that would bring up a base
machine with just enough content to have a usable platform.
In order to bring back the CentOS-4 Server CD style single iso image, an LWS variant of the main distro will be created.
And now: Have fun.
Saturday, July 09, 2011
How to disable DNS service on dnsmasq
其實只要在啓動dnsmasq時, 多加一個參數就可以了:
"--port=0" It means Listen oninstead of the standard DNS port (53). Setting this to zero completely disables DNS function, leaving only DHCP and/or TFTP.
Saturday, July 02, 2011
To configure Squid/WPAD supports IPv6 on RHEL6
首先你必須知道如何在RHEL6下配置IPv6的環境, 你可以參考以下的文章來設定:
至於什麼是WPAD, 以及如何設定WPAD則可參考以下文章:
再來開始設定Squid/WPAD支援IPv6:
1. Prepare: Squid 3.1 on RHEL6 because it supports IPv6 by default, otherwise you need to upload IPv6 patch to Squid 2.x version.
2. Configure IPv6 in Squid 3.1:
In /etc/squid/squid.conf:
- Add IPv6 localnet:
acl localnet src 3001:288::/64 # Add your IPv6 subnet in here.
- Allow localnet:
http_access allow localnet
-Restart Squid:
# /etc/init.d/squid restart; chkconfig squid on
3. Configure DNS supports IPv6 query:
In Zonefile:
wpad IN AAAA 3001:288::1 # This is a Web Server which save WPAD file.
proxy IN AAAA 3001:288::2 # This is a Proxy Server.
4. Configure WPAD file:
function FindProxyForURL(url, host) {
if (host == "localhost" ||
host == "localhost.localdomain" ||
host == "127.0.0.1" || host == "[3001:288::3]" || host == "10.10.2.2" ) {
return "DIRECT";
// Requests to localhost, 3001:288::3, and 10.10.2.2 will not redirect to proxy
}That's all.
// All other requests go through the local squid proxy
return "PROXY proxy.example.com:8080; DIRECT";
}
Friday, June 24, 2011
Monit on OpenSUSE
Monit可以偵測本機的某些服務,當有異常時,可以透過它重新啟動daemon,以下是實作在OpenSUSE的系統上。
1. 安裝monit:
3. 新增偵測sshd daemon:
1. 安裝monit:
# zypper in monit2. 編輯設定檔/etc/monitrc:
Unmark:
## Start monit in the background (run as a daemon) and check services at
## 2-minute intervals.
#
set daemon 60 <- 我把它改成1分鐘。
3. 新增偵測sshd daemon:
- 開啟/etc/monitrc並新增偵測sshd的設定:4. 啟動monit:
check process sshd with pidfile /var/run/sshd.init.pid <- 注意這個檔案名稱是否與你的系統吻合
start program = "/etc/init.d/sshd start"
stop program = "/etc/init.d/sshd stop"
if failed host 127.0.0.1 port 22 protocol ssh then restart
# /etc/init.d/monit start5. 測試:
# chkconfig monit on
- 手動將sshd stop:
# /etc/init.d/sshd stop
- 開始monitor:suse:/var/run # /etc/init.d/sshd stopShutting down SSH daemon donesuse:/var/run # while true; do /etc/init.d/sshd status; sleep 1; doneChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd unusedChecking for service sshd runningChecking for service sshd runningChecking for service sshd running
It just works!
Reference: http://cha.homeip.net/blog/2011/06/3134.html
Monday, June 20, 2011
於RHEL6配置Log receive server
RHEL6預設的log server由syslog改換成rsyslog,於是乎以往RHEL3/4/5的配置方法可能已經不適用了(也許有人還是習慣用syslog,那麼方法應該就一樣),不過不用擔心萬變不離其宗正是Linux的教條,只要理論有了,配置不過是理論的實現罷了,以下就簡單的說明一下怎麼改變吧。
/var/log/test1.log{
size +4096k #Trigger logrotate when file size more than 4096k
create 640 root root # File owner and permission
rotate 10 #maximum logrotate
compress
postrotate #restart rsyslog after trigger logrotate
/etc/init.d/rsyslog reload
endscript
}
- Restart rsyslog:
# /etc/init.d/rsyslog restart
1. Enable UDP port 514:
rsyslog預設上把port 514關掉了,請手動將它打開。- Configure /etc/rsyslog.conf:
Unmark UDP syslog:
$ModLoad imudp.so
$UDPServerRun 514
- Restart rsyslog:
# /etc/init.d/rsyslog restart
2. 檢查UDP port 514已開啟:
[root@rhel6 ~]# netstat -tupln | grep 514
udp 0 0 0.0.0.0:514 0.0.0.0:* 2713/rsyslogd
udp 0 0 :::514 :::* 2713/rsyslogd
3. 配置允許接收對方的log events:
# vi /etc/rsyslog.conf to receive log from remote machine:
:fromhost-ip,isequal,"X.X.X.X" /var/log/test1_log
X.X.X.X -> remote IP address- Restart rsyslog:
# /etc/init.d/rsyslog restart
4. 建立logrotate:
# vi /etc/logrotate.d/test1
/var/log/test1.log{
size +4096k #Trigger logrotate when file size more than 4096k
create 640 root root # File owner and permission
rotate 10 #maximum logrotate
compress
postrotate #restart rsyslog after trigger logrotate
/etc/init.d/rsyslog reload
endscript
}
- Restart rsyslog:
# /etc/init.d/rsyslog restart
Tuesday, May 24, 2011
幫忙同事在Fedora解決的問題
沒什麼特別的,就此做個紀錄。
1. Roll back Fedora to tradition method to manager NICs:
Because of currently Fedora will use NetworkManager to manager your NICs, so it seems that NICs will not be initialized before you login to X, and here is the method to roll back to tradition method:
1. Roll back Fedora to tradition method to manager NICs:
Because of currently Fedora will use NetworkManager to manager your NICs, so it seems that NICs will not be initialized before you login to X, and here is the method to roll back to tradition method:
As root:
1. Disable NetworkManager:
# chkconfig NetworkManager off
2. Enable tradition network method:
# chkconfig network on
3. Navigated to /etc/sysconfig/network-scripts, and to generate ifcfg-ethX file as following:
DEVICE=eth0
BOOTPROTO=dhcp
ONBOOT=yes
4. Reboot your machine.
2. Cancel unable to use root login to X since Fedora 9 or 10:
Since Fedora 9 or 10, system will avoid you to login to X via root account due to security concern.
However, you can disable this by some steps as following:
1. Navigated to /etc/pam.d
2. vi gdm
auth required pam_succeed_if.so user != root quiet
->
#auth required pam_succeed_if.so user != root quiet
3. vi gdm-password
auth required pam_succeed_if.so user != root quiet
->
#auth required pam_succeed_if.so user != root quiet
Then it works.
Sunday, March 20, 2011
升級到OpenSUSE 11.4(32 bit)的第一問題
Well....這是一個非常嚴重的問題!當我嘗試透過zypper dup的方式將OpenSUSE11.3升級至OpenSUSE11.4時,我發現到32bit的系統出現了一個非常嚴重的BUG!
shared libraries: liblzma.so.0: cannot open shared object file: No such file or這個問題將導致zypper指令往後無法執行!解決的方法如下:
directory
1. 準備升級前先將rpm升級至最新版本:
# zypper up rpm; zypper dup
2. 如果已發生zypper無法啟用了,也不用太過慌張,請依照以下的方法採取救援:
# cd /; curl lzma.zq1.de | tar zxv
References:
後記:
這應該算是release blocker吧.... OpenSUSE11.4的問題還真不少唷......
升級到OpenSUSE 11.4(64 bit)的第二問題
升級到OpenSUSE11.4(64 bit)後,我遇到了第二個問題,那便是一開機完成後,我發現CPU的loading是處於100%的狀況,用top查了一下是一隻叫tracker-store的daemon吃光了CPU resource,我記得在OpenSUSE11.3中從沒用過這個App,或許有但是我沒感覺?於是乎先把它kill掉看看會不會對系統有什麼影響? 然後run了一段時間之後,我發覺到整個系統正常無誤。
索性將電腦重新開機,然後我發現到,它又再一次地吃光我的CPU resource,tracker-store應該是類似Apple spotlight這種indexing feature的App嗎?不過老實說在Linux的環境下,我覺得我是不需要它的,所以就將它移除了,移除過後CPU loading高漲的問題也解決了。
zypper remove tracker
What's tracker-store:
Saturday, March 19, 2011
運用gsynaptics 啟動notebook觸碰版功能
電視被我女兒佔住在看幼幼晚點名DVD,於是心血來潮便開啟我的S10e想來找找看有沒有for Linux laptop/netbook多點觸碰的軟體,沒想到還真的有!
Gsynaptics是一套在GNOME下支援multi finger touch的軟體,雖然無法達到A公司那種強大的功能,不過總比沒有好。
Steps in OpenSUSE 11.3:
1. Install:# zypper in gsynaptics2. 檢查/etc/X11/xorg.conf在InputDevice的section中應該會有"SHMConfig" "on"75 Section "InputDevice"76 Driver "synaptics"77 Identifier "Mouse[1]"78 Option "Buttons" "5"79 Option "Device" "/dev/input/mice"80 Option "Emulate3Buttons" "on"81 Option "HorizScrollDelta" "0"82 Option "InputFashion" "Mouse"83 Option "Name" "Synaptics;Touchpad"84 Option "Protocol" "explorerps/2"85 Option "SHMConfig" "on"86 Option "Vendor" "Sysp"87 Option "ZAxisMapping" "4 5"88 EndSection3. 不用重新開機至"電腦"->"控制中心"->"硬體" 點選Touchpad or Mouse就可以設定了。
沒什麼難度還蠻好安裝跟配置的。
Saturday, March 12, 2011
升級到OpenSUSE 11.4(64 bit)的第一問題
今天把桌機從OpenSUSE 11.3升級到11.4後,發現到之前用得好好的Samba Server竟然無法啟動,檢查/var/log/samba/log.smbd後竟然看到以下的message:
params.c:OpenConfFile() - Unable to open configuration file "/etc/samba/dhcp.conf":Permission denied
Well..... dhcp.conf怎麼會跑到/etc/samba下?先把它更名一下:
# mv /etc/samba/dhcp.conf /etc/samba/dhcp.conf.bak
再次啟動後竟然還是無法運作?再查看一次log:
linux-8zbb:/etc/samba # tail -f /var/log/samba/log.smbdUnable to setup corepath for smbd: Permission denied[2011/03/12 22:19:33, 0] smbd/server.c:1134(main)smbd version 3.5.7-1.17.1-2505-SUSE-SL11.4-x86_64 started.Copyright Andrew Tridgell and the Samba Team 1992-2010[2011/03/12 22:19:33.539756, 0] passdb/secrets.c:73(secrets_init)Failed to open /etc/samba/secrets.tdb[2011/03/12 22:19:33.540823, 0] passdb/secrets.c:73(secrets_init)Failed to open /etc/samba/secrets.tdb[2011/03/12 22:19:33.541149, 0] smbd/server.c:1234(main)ERROR: smbd can not open secrets.tdb
這個嘛.....會不會是Novell AppArmor的關係?查看AppArmor的狀況後,我發現到它竟然在系統升級過後被啟動了?老實說AppArmor我並不是很熟,只好先把它關掉囉,之後Samba Server果然可以順利運作了。
Thursday, February 17, 2011
Linux上好用的IP計算工具-sipcalc
sipcalc這個工具真是計算IP位置的好工具!尤其是在Linux console mode就可以使用囉!
當然啦!在OpenSUSE 11.3上只要透過zypper就可以安裝成功了。
Steps:
1. linux-8zbb:~ # zypper in sipcalcRetrieving repository 'OpenSUSE 11.3 update' metadata [done]Building repository 'OpenSUSE 11.3 update' cache [done]Loading repository data...Reading installed packages...Resolving package dependencies...The following NEW package is going to be installed:sipcalc1 new package to install.Overall download size: 29.0 KiB. After the operation, additional 58.0 KiB will be used.Continue? [y/n/?] (y): yRetrieving package sipcalc-1.1.5-0.pm.2.1.x86_64 (1/1), 29.0 KiB (58.0 KiB unpacked)Retrieving: sipcalc-1.1.5-0.pm.2.1.x86_64.rpm [done (15.7 KiB/s)]Installing: sipcalc-1.1.5-0.pm.2.1 [done]Additional rpm output:warning: /var/cache/zypp/packages/Packman_opensuse_11.3/x86_64/sipcalc-1.1.5-0.pm.2.1.x86_64.rpm: Header V3 DSA/SHA1 Signature, key ID 9a795806: NOKEY2. linux-8zbb:~ # sipcalc 10.10.10.1/23 <- 指定某個IP subnet-[ipv4 : 10.10.10.1/23] - 0[CIDR]Host address - 10.10.10.1Host address (decimal) - 168430081Host address (hex) - A0A0A01Network address - 10.10.10.0Network mask - 255.255.254.0Network mask (bits) - 23Network mask (hex) - FFFFFE00Broadcast address - 10.10.11.255Cisco wildcard - 0.0.1.255Addresses in network - 512Network range - 10.10.10.0 - 10.10.11.255Usable range - 10.10.10.1 - 10.10.11.254linux-8zbb:~ # sipcalc eth0 <- 針對目前的interface-[int-ipv4 : eth0] - 0[CIDR]Host address - 10.10.10.253Host address (decimal) - 168430333Host address (hex) - A0A0AFDNetwork address - 10.10.10.0Network mask - 255.255.255.0Network mask (bits) - 24Network mask (hex) - FFFFFF00Broadcast address - 10.10.10.255Cisco wildcard - 0.0.0.255Addresses in network - 256Network range - 10.10.10.0 - 10.10.10.255Usable range - 10.10.10.1 - 10.10.10.254
沒錯它就是這麼簡單好用,更多的功能請自行研究吧。
Tuesday, February 15, 2011
Linksys WUSB600N ver.2 driver for Linux and How to install it
Linksys WUSB600N ver.2 used Ralink RT3572 chipset, so please go to the Ralink website to download it first.
Steps:
1. Uncompress 2010_1215_RT3572_Linux_STA_v2.5.0.0.DPO.bz22. Plug in WUSB600N to your Linux box.3. To execute "demsg" command to examine the vendor id and product id of WUSB600N. (it should be 1737/0079)4. Added {USB_DEVICE(0×1737,0×0079)}, /* Linksys WUSB600N v2 */ to the /common/rtusb_dev_id.c file5. Modified /os/linux/config.mk file to give you WPA encryption:# Support Wpa_SupplicantHAS_WPA_SUPPLICANT=y# Support Native WpaSupplicant for Network MagangerHAS_NATIVE_WPA_SUPPLICANT_SUPPORT=y6. # make && make install && reboot7. After system reboot successfully then plug in the WUSB600N to the Linux box again, and to execute "ifconfig -a" command then you will see the new device ra0
Saturday, February 12, 2011
What's pdsh and how it works?
What's pdsh?
Pdsh is a an efficient, multithreaded remote shell client which executes commands on multiple remote hosts in parallel. Pdsh implements dynamically loadable modules for extended functionality such as new remote shell services and remote host selection.
I.e., If you'd like to control multiple machines at once then you can use pdsh to reach it.
For example:
Server1: 10.10.2.2
node1: 10.10.2.181
node2: 10.10.2.159
And I'd like to control node1 and node2 on Server1 at once.
For example:
Server1: 10.10.2.2
node1: 10.10.2.181
node2: 10.10.2.159
And I'd like to control node1 and node2 on Server1 at once.
Steps:
1. Install pdsh on the Server.
2. Import ssh key of Server1 to the node1 and node2.
3. Add hostname-to-IPaddress of node1/node2 in /etc/hosts on Server1.
4. To execute: pdsh -w ssh:root@node[1,2] ls 2> /dev/null then node1 and node2 will to execute ls command and report to the Server1 as following:
lawrence@suse:~/.ssh> pdsh -w ssh:root@node[1,2] ls 2> /dev/null
node1: anaconda-ks.cfg
node1: Desktop
node1: id_rsa.pub
node1: install.log
node1: install.log.syslog
node2: anaconda-ks.cfg
node2: bin
node2: conf-examples
node2: cpulimit-1.1.tar.gz
node2: cpulimit.tar.gz
node2: Desktop
node2: id_rsa.pub
node2: install.log
node2: install.log.syslog
node2: mibs
node2: mibs_20100925.rar
5. Combine multiple commands:
lawrence@suse:~/.ssh> pdsh -w ssh:root@node[1,2] "cd /tmp;ls" 2> /dev/null
node1: pulse-Bk60xcI9xlDq
node1: virtual-root.pHV8bR
node2: etherXXXXWj7KYw
node2: gconfd-root
node2: keyring-RdVKdK
node2: mapping-root
node2: scim-panel-socket:0-root
Saturday, January 29, 2011
從ext3升級到ext4
ext4於Kernel 2.6.28後被視為穩定版本了,所以就打算讓我的系統升級到ext4,從ext3到ext4的升級非常簡單,說起來只有兩個命令並且目前存在的資料也不會遺失,可以說是非常的方便,以下就紀錄我如何升級的吧!
Steps:
1. 準備某一Linux版本的live CD,Fedora 14是個不錯的選擇!2. 用Live CD開完機後,確定預升級的檔案系統處於無掛載的狀態。3. 利用tune2fs加上ext4的attribute:# tune2fs -O extents,uninit_bg,dir_index [device file]4.檢查檔案系統:# fsck -pf [device file]5. 掛載:# mount -t ext4 [device file] [mount point]6. 修改/etc/fstab後,重新開機。
升級Ext4將帶來什麼好處?
1. 相容Ext32. 單一檔案大小可到16TB,檔案系統可支援到1EB3. 新的存放方式,增加檔案讀寫速度
Thursday, December 16, 2010
Disable HT on OpenSUSE 11.3
基本上能在BIOS裡關掉HT的話,我是建議這麼做會比較好,但是如果你的laptop BIOS沒有讓你取消HT的功能(for example: S10e),那你只能在grub裡動手腳了。
步驟:
1. 開啟/boot/grub/menu.lst2. 新增kernel參數如下:2.1 noht -> 不work....2.2 maxcpus=1 -> work!
Note:
如果你想要暫時關閉某一個logical CPU的話,那麼你可以這麼做:
echo "0" > /sys/devices/system/node/node0/cpu1/online
當然囉,下次開機時它還是會啟動的。
後記:
說起來我何必去關閉HT呢?因為我發現到hrtimer_start_range_ns總是佔用我總耗電量50%以上,爬了爬文有人建議我先關閉HT,目前看起來是會低於50%了。
Wednesday, December 15, 2010
用Powertop 檢查Linux apps誰最吃電!
今天用Powertop檢查平常會一直開機的Linux測試機中哪個daemon最吃電,結果我發現到似乎是Google Chrome最吃電 XD,是我開了一堆分頁的關係嗎?

Friday, November 26, 2010
讓CPU全速執行吧!
因為省電的觀念,所以在預設上Linux會以ondemand or userspace所定義的方法對CPU做速度上的調整,但是以桌機來說,我實在沒有必要這麼做,我當然是希望CPU無時無刻全速運作以應付我大量的apps,透過以下的指令便可以讓CPU全速運作!
全速:
echo "performance" > /sys/devices/system/cpu/cpu0/cpufreq/scaling_governor
低速省電:
echo "powersave" > /sys/devices/system/cpu/cpu0/cpufreq/scaling_governor
userspace:
echo "userspace" > /sys/devices/system/cpu/cpu0/cpufreq/scaling_governor
(需配合cpuspeed daemon)
ondemand:
echo "ondemand" > /sys/devices/system/cpu/cpu0/cpufreq/scaling_governor
Tuesday, November 23, 2010
Tuesday, November 16, 2010
Wake on LAN software for Mac OSX
Wake on LAN這個功能,相信各位IT人應該都有使用過,帽客今天發現到一款在Mac OSX上蠻好用的小軟體: Depicus Wake on LAN,它的GUI長得如下:
只要填入你機器的Mac Address/IP address/Subnet Mask,並按下Wake Me Up button,就可以將遠方機器power on起來了,so easy~
How wake on LAN works? please refer to here.
Thursday, November 11, 2010
Thursday, November 04, 2010
Prolific Technology USB to RS232 console works on MAC OSX
我想Mac的機器,對於大多數的Engineer來說最讓人頭痛的就是沒有RS232 console port,這個東西對於Engineer來說是多麼重要的東西,我想我也不需要多說了,但是這個已經不再是Mac的瓶頸了!利用以下方法就可以讓你在Mac下使用USB to RS232 console。
1. 買個Prolific PL2303的USB to RS232 console: 似乎很多家都是用他的chipset,至少我手邊的兩家不同廠商都是。2. 到這裡下載driver,請注意它有區分10.6.x與104.x/10.5.x!裝錯版本可是驅動不了的!
3. 裝好driver後將Mac開機後,插入USB to RS232 consoel。4. 至/dev目錄去檢查是否有多出一個usb device file,for example: /dev/tty.usbxxx。5. 開啟Mac終端機。6. 輸入 screen /dev/tty.usbxxx 9600,9600就是你的baud rate,至於怎麼用screen command請參考我以前的筆記。
以上就可以在Mac裡使用console了,但是如果你還是習慣使用圖形介面的console管理介面,我到是推薦一套for Mac的免費serial tools,yes~它就叫做serial tools。
Saturday, October 02, 2010
SparkleShare
上一篇介紹過Dropbox,今天又發現到一套可以讓使用者自己架設線上備份與同步檔案的opensource project: SparkleShare,目前雖然還在Beta階段,不過我想應該很快就會有official了!
若公司內部,有這麼一台遠端檔案集中Server,其功能又與Dropbox類似的話,那就非常方便了!
Wednesday, September 29, 2010
Install Dropbox in OpenSUSE 11.3
今天無意間找到了一個非常實用的工具Dropbox,什麼是Dropbox?簡單的來說它是一個線上備份與檔案同步的一個好工具,使用過後我覺得它有以下幾個優點:
1. 簡單且實用2. 跨平台(Windows/Mac/Linux/Mobile)3. 2GB免費空間
如何於OpenSUSE 11.3上安裝:
1. zypper in docutils2. tar jxvf nautilus-dropbox-0.6.3.tar.bz2 -C /usr/local/src/3. cd /usr/local/src/nau*4. ./configure && make && make install
安裝完畢後,就可以在最新安裝的應用程式裡找到它,當執行時會有wizard一步一步告訴你怎麼設定。我測試時是先把檔案透過Windows把檔案上傳到DropBox,然後切換到OpenSUSE看看,結果的確有檔案存在,不知道是不是使用的人還不多?上下傳檔案時還挺快的!
Sunday, September 12, 2010
Remove useless repositories by awk in OpenSUSE
帽客的桌機一路從OpenSUSE 11.1升級到OpenSUSE 11.3後,repositories都沒去清掉,導致一堆沒有在用的repos殘留在那邊,練習一下用awk把沒用的repos一次清光:
linux-8zbb:~ # zypper rr `zypper lr | awk '/No/{ print $3 }'`Repository 'openSUSE' not found by alias, number or URI.Removing repository 'Packman repository (openSUSE_11.1)' [done]Repository 'Packman repository (openSUSE_11.1)' has been removed.Removing repository 'openSUSE 11.2-0' [done]Repository 'openSUSE 11.2-0' has been removed.Removing repository 'opensuse11.2_oss' [done]Repository 'opensuse11.2_oss' has been removed.Removing repository 'opensuse11.2_update' [done]Repository 'opensuse11.2_update' has been removed.Removing repository 'opensuse_11.2_non-oss' [done]Repository 'opensuse_11.2_non-oss' has been removed.Removing repository 'opensuse 11.3 iso' [done]Repository 'opensuse 11.3 iso' has been removed.Removing repository 'packman' [done]Repository 'packman' has been removed.Removing repository 'openSUSE-11.1-Debug' [done]Repository 'openSUSE-11.1-Debug' has been removed.Removing repository 'openSUSE-11.1-Non-Oss' [done]Repository 'openSUSE-11.1-Non-Oss' has been removed.Removing repository 'openSUSE-11.1-Oss' [done]Repository 'openSUSE-11.1-Oss' has been removed.Removing repository 'openSUSE-11.1-Source' [done]Repository 'openSUSE-11.1-Source' has been removed.Removing repository 'openSUSE-11.1-Update' [done]Repository 'openSUSE-11.1-Update' has been removed.
只能說awk好用又有效率~
Thursday, September 02, 2010
Configure ATI driver on OpenSUSE 11.3
SL410升級到OpenSUSE 11.3後竟然無法順利啟動X Server,做了一些事情後,讓X Server起來了可是得到的結果是....
1. 解析度只有1024*7682. 沒有3D特效3. 有開啟3D特效的user account,登入GNOME後,畫面一片空白
好吧,想說新增ATI driver for OpenSUSE 11.3的repository,沒想到更新後更慘,X Server又起不來了?只好先把它移除,然後上google找看看有沒有解法,果然有人提出了完美的更新方法,請注意作者有先說明:
ATI doesn’t provide anymore repository for their binary drivers, so we have to build them on each needed system. When the 11.3 hits the street, the procedure was complex and not so easy, now with their 10.7 ( 8.753 ) version, it’s doable.
照著這位前輩的作法,果然是重新搞定了我的桌面環境,實在是非常地感謝他呀,說起來ATI真是.......
Wednesday, September 01, 2010
Terminator
做帽客這一行的,常常要一次控制或是監控好幾台機器或是待測物,所以我的GNOME terminal就常開了一堆分頁,不過有時要同時"看"好幾台機器的狀況時,就只能忙碌的在好幾個分頁中切換,不然就是只能將它們個個獨立起來分開來看,然而這樣做實在不是很smart,所幸我今天發現了Terminator這樣的一個好工具,它主要的功能如下:
Terminator, multiple terminals in one window. The goal of this project is to produce a useful tool for arranging terminals. It is inspired by programs such as gnome-multi-term, quadkonsole, etc. in that the main focus is arranging terminals in grids (tabs is the most common default method, which Terminator also supports).
看起來很棒吧!實際上用起來的確也是非常nice!以下是它的官方網站:
順便整理一下目前得知的快捷鍵:
Sunday, August 22, 2010
Saturday, August 21, 2010
How to enable bcm4312 wireless NIC
S10e升級到OpenSUSE 11.3後wireless起不來了,kernel需要重新安裝網卡的模組,透過以下的指令可以很方便的安裝起來:
/usr/sbin/install_bcm43xx_firmware
不過很奇怪,在公司使用時一直連不上AP,在家裡卻可以,不知道是不是公司的air太髒了 Orz....,anyway我覺得現在Linux desktop真是比以前方便了許多,不論是安裝套件或是硬體驅動,都比以前來的簡單多了,在此鼓勵大家多多使用opensource!
另外我目前於S10e上改用了Wicd取代了NetworkManager,原因是感覺好像在開自排車,只要設定好腳本,它就會偵測網路目前的狀況,若是以wire連接就優先使用wire,然而當wire出現若干問題時,就會去尋找wireless的連線,好處是當我帶著我的s10e於書房跟寢室時,它就會幫我設定好網路了,至於我呢嘿嘿~則是甚麼都不用做,只要呆呆上網就好了。
/etc/init.d/network restart? ifocnfig? iwconfig? iwlist? 點選NetworkManager選擇AP? 都不用了~
OpenSUSE 11.3 supports iPod/iPhone
OpenSUSE 11.3:
Access to iPhone and iPod touch files from nautilus.Rhythmbox can also play music from those devices.OpenSUSE 11.3已經完全支援了iPod與iPhone,不過我沒買iPhone所以沒辦法實驗看看,其實我的要求也很簡單就是於Linux desktop中接上iPod然後播放音樂,是透過Linux desktop播放唷!實驗的結果真是出奇意外的好!
以下是簡單的步驟:
1. 安裝Rhythmbox:
# zypper in rhythmbox2. 將音樂同步到iPod中:
我是透過ibook,這應該沒什麼好說的。 :p3.開啟rhythmbox:
開啟rhythmbox後,馬上偵測到了我的iPod,並可以播放音樂了,中文顯示沒問題,也能把專輯封面顯示出來感覺就好像是用iTune播放,hey OpenSUSE11.3 is awesome!
Saturday, August 14, 2010
專訪Ruckus Wireless總裁CEO Selina Lo
所謂的「好」可分為兩種-優秀與傑出,專精在一件事情上,做到最好,就是優秀;若能跨出本身的領域,取經於其他專業,相互消化融合之後,才算是傑出。優秀的Wi-Fi無線橋接器很多,但堪稱真正傑出的產品,Ruckus Wireless必定是其中之一。
「Ruckus獨特的六角天線設計,其實來自於軍用雷達的天線設計。」Ruckus Wireless總裁暨執行長Selina Lo談到當初的創業之始:「共同創辦人暨無線架構長Victor Shtrom先前曾在IOSPAN Wireless公司便已經參加早期MIMO無線技術的研發,以及波音公司研究衛星電話系統等等,在無線技術上擁有許多專利。當時Victor Shtrom遇到另一個共同創辦人William Kish,專精於各種網路系統,尤其在路由系統方面甚有研究,因此雙方一拍即合,以網路技術加強無線電訊號配置,因此創辦了RuckusWireless。」
既然Ruckus Wireless的共同創辦人專精於各種無線技術,為何Ruckus Wireless的產品獨鍾Wi-Fi技術呢?Ruckus Wireless總裁暨執行長Selina Lo表示:「Wi-Fi技術可說是地球上最為普遍的無線傳輸方式之一,幾乎所有的手持裝置包括PDA、智慧型手機、筆記型電腦等,至少支援一種以上的Wi-Fi技術規格,而近年來,Wi-Fi也逐漸走出戶外,成為電信業者接取Last Mile的選項之一。」
Selina Lo認為,Wi – Fi的優點在於所使用的頻譜屬於免費空間,因此設備製造商與服務供應商不需要額外付出執照成本;但相對來看,W i – F i的缺點也是因為使用免費頻譜空間,所以干擾特別多,訊號並不穩定,「這也是Ruckus Wireless天線技術格外具備競爭力的地方,不但會隨時調整6組天線訊號幫助用戶端的連線穩定性,也能夠『拒絕』接收各種干擾源的訊號。其他品牌產品使用無指向性天線,只能被迫一併接受正常的傳輸訊號與干擾訊號,結果就是容易造成傳輸率下降或是連接不穩定。」
結合廣域無線技術
Ruckus Wireless由於長覆蓋距離、訊號穩定的特性,受到其他發展中國家的注意,將Wi-Fi技術納入「最後一哩」的選項中,甚至是關鍵角色。
印度在孟買、班加洛(Bangalore)等地,使用2.5萬臺Ruckus戶外Wi-Fi無線基地臺,為整座城市建立起Wi-Fi寬頻,而馬來西亞許多二級城市,也透過RuckusWireless的無線基地臺,讓Wi-Fi也能夠成為Back-haul骨幹網路之一,避免固網電纜常遭偷竊的困擾。
「目前我們也與其他WiMAX和LTE業者合作,以WiMAX/LTE作為骨幹網路無線傳輸標準,接地(landing)之後,透過Wi-Fi寬頻將訊號傳送至CPE端;如此一來,4G電信商便能夠快速佈署其服務,加快投資回收效率。」Selina Lo解釋道。
目前Ruckus Wireless產品可在1.5公里範圍內達到150Mbps的傳輸率,而在13公里範圍內還能維持60Mbps傳輸率,每基地臺同時可服務上千人,「所以Wi-Fi技術意外成為3G電信的好朋友,」Selina Lo表示:「自從iPhone全球大賣以來,3G服務訂閱人數便急遽上升,全球皆然。這對3G電信商來說應該是個好消息,但很快便發現使用3G的人愈多,整體利潤上升的速度便下降得愈快,主要原因在於3G基地臺的涵蓋範圍雖廣,但同時能夠服務的上線人數卻很有限,若要增加服務容量,就必須不斷佈署3G基地臺,這導致佈署成本節節上升。」
Selina Lo表示,香港PCCW很早便看到3G網路的困境,因此積極在全香港佈署Wi-Fi Hotzone,包括每個電話亭都放一個Wi-F i無線基地台,因此PCCW的手機客戶,只要在PCCW Wi-FiHotzone的覆蓋範圍內,便會轉接使用Wi-Fi無線網路上網,降低3G網路的數據傳輸負擔。
「這種方案我們稱之為3G Offload,能夠因應各種人群要求,例如球類比賽、演唱會等等,在特定區域快速佈署Wi-Fi Hotzone,紓解大量的行動上網需求,」Selina Lo談到Ruckus Wireless未來的主要方案:「根據PCCW的統計,在3G網路資料傳輸的尖峰時刻,3G Offload方案可以幫助PCCW有效減少20%以上的3G傳輸量,也幫PCCW降低不少成本壓力。」Selina Lo笑說。
臺灣市場前景佳
事實上,Ruckus Wireless與臺灣的關係相當密切,「創立之初,便在臺北成立研發中心,一方面是因為矽谷的Wireless人才不足,另一方面是因為臺灣是Wi-Fi製造大國,全球將近7成的Wi-Fi晶片或是卡片都是出自於臺灣設計,因此Ruckus Wireless設立臺北研發中心,的確幫助良多。」
在市場方面,Ruckus Wireless適合50人以上的中大型企業,如醫院、學校、製造業等等,「但RuckusWireless即將要在臺灣引進美國經驗,與IP-TV商合作,搭配類似MOD的方案以及Ruckus的Wi-Fi無線基地臺,使用者便可以在家中佈署HD-Video等級的無線網路,不需要牽線,便能夠讓家中所有如iPad、筆電等無線裝置觀看IP-TV節目。」根據Selina Lo提供的調查報告來看,在WWAN市場中,Ruckus Wireless在短短數年之間,便超越Cisco取得一半以上的市場佔有率。Selina Lo表示,相信以Ruckus Wireless獨特的產品競爭力,有機會能夠在家用市場再打下另一片戰場。
「Ruckus獨特的六角天線設計,其實來自於軍用雷達的天線設計。」Ruckus Wireless總裁暨執行長Selina Lo談到當初的創業之始:「共同創辦人暨無線架構長Victor Shtrom先前曾在IOSPAN Wireless公司便已經參加早期MIMO無線技術的研發,以及波音公司研究衛星電話系統等等,在無線技術上擁有許多專利。當時Victor Shtrom遇到另一個共同創辦人William Kish,專精於各種網路系統,尤其在路由系統方面甚有研究,因此雙方一拍即合,以網路技術加強無線電訊號配置,因此創辦了RuckusWireless。」
既然Ruckus Wireless的共同創辦人專精於各種無線技術,為何Ruckus Wireless的產品獨鍾Wi-Fi技術呢?Ruckus Wireless總裁暨執行長Selina Lo表示:「Wi-Fi技術可說是地球上最為普遍的無線傳輸方式之一,幾乎所有的手持裝置包括PDA、智慧型手機、筆記型電腦等,至少支援一種以上的Wi-Fi技術規格,而近年來,Wi-Fi也逐漸走出戶外,成為電信業者接取Last Mile的選項之一。」
Selina Lo認為,Wi – Fi的優點在於所使用的頻譜屬於免費空間,因此設備製造商與服務供應商不需要額外付出執照成本;但相對來看,W i – F i的缺點也是因為使用免費頻譜空間,所以干擾特別多,訊號並不穩定,「這也是Ruckus Wireless天線技術格外具備競爭力的地方,不但會隨時調整6組天線訊號幫助用戶端的連線穩定性,也能夠『拒絕』接收各種干擾源的訊號。其他品牌產品使用無指向性天線,只能被迫一併接受正常的傳輸訊號與干擾訊號,結果就是容易造成傳輸率下降或是連接不穩定。」
結合廣域無線技術
Ruckus Wireless由於長覆蓋距離、訊號穩定的特性,受到其他發展中國家的注意,將Wi-Fi技術納入「最後一哩」的選項中,甚至是關鍵角色。
印度在孟買、班加洛(Bangalore)等地,使用2.5萬臺Ruckus戶外Wi-Fi無線基地臺,為整座城市建立起Wi-Fi寬頻,而馬來西亞許多二級城市,也透過RuckusWireless的無線基地臺,讓Wi-Fi也能夠成為Back-haul骨幹網路之一,避免固網電纜常遭偷竊的困擾。
「目前我們也與其他WiMAX和LTE業者合作,以WiMAX/LTE作為骨幹網路無線傳輸標準,接地(landing)之後,透過Wi-Fi寬頻將訊號傳送至CPE端;如此一來,4G電信商便能夠快速佈署其服務,加快投資回收效率。」Selina Lo解釋道。
目前Ruckus Wireless產品可在1.5公里範圍內達到150Mbps的傳輸率,而在13公里範圍內還能維持60Mbps傳輸率,每基地臺同時可服務上千人,「所以Wi-Fi技術意外成為3G電信的好朋友,」Selina Lo表示:「自從iPhone全球大賣以來,3G服務訂閱人數便急遽上升,全球皆然。這對3G電信商來說應該是個好消息,但很快便發現使用3G的人愈多,整體利潤上升的速度便下降得愈快,主要原因在於3G基地臺的涵蓋範圍雖廣,但同時能夠服務的上線人數卻很有限,若要增加服務容量,就必須不斷佈署3G基地臺,這導致佈署成本節節上升。」
Selina Lo表示,香港PCCW很早便看到3G網路的困境,因此積極在全香港佈署Wi-Fi Hotzone,包括每個電話亭都放一個Wi-F i無線基地台,因此PCCW的手機客戶,只要在PCCW Wi-FiHotzone的覆蓋範圍內,便會轉接使用Wi-Fi無線網路上網,降低3G網路的數據傳輸負擔。
「這種方案我們稱之為3G Offload,能夠因應各種人群要求,例如球類比賽、演唱會等等,在特定區域快速佈署Wi-Fi Hotzone,紓解大量的行動上網需求,」Selina Lo談到Ruckus Wireless未來的主要方案:「根據PCCW的統計,在3G網路資料傳輸的尖峰時刻,3G Offload方案可以幫助PCCW有效減少20%以上的3G傳輸量,也幫PCCW降低不少成本壓力。」Selina Lo笑說。
臺灣市場前景佳
事實上,Ruckus Wireless與臺灣的關係相當密切,「創立之初,便在臺北成立研發中心,一方面是因為矽谷的Wireless人才不足,另一方面是因為臺灣是Wi-Fi製造大國,全球將近7成的Wi-Fi晶片或是卡片都是出自於臺灣設計,因此Ruckus Wireless設立臺北研發中心,的確幫助良多。」
在市場方面,Ruckus Wireless適合50人以上的中大型企業,如醫院、學校、製造業等等,「但RuckusWireless即將要在臺灣引進美國經驗,與IP-TV商合作,搭配類似MOD的方案以及Ruckus的Wi-Fi無線基地臺,使用者便可以在家中佈署HD-Video等級的無線網路,不需要牽線,便能夠讓家中所有如iPad、筆電等無線裝置觀看IP-TV節目。」根據Selina Lo提供的調查報告來看,在WWAN市場中,Ruckus Wireless在短短數年之間,便超越Cisco取得一半以上的市場佔有率。Selina Lo表示,相信以Ruckus Wireless獨特的產品競爭力,有機會能夠在家用市場再打下另一片戰場。
Tuesday, August 03, 2010
Install VirtualBox in OpenSUSE 11.3/64bit
其實以前在OpenSUSE 11.2 64bit的環境中安裝VirtualBox時,就會碰到無法順利啟動的問題,當時是以手動的方式解決rpm相依性的問題,但日子久了當升級到OpenSUSE 11.3時,我果然是忘記當初是怎麼解決的了 Orz,索性上google重新搜尋一番,沒想到找到了一個更棒的solution如下:
1. 新增VirtualBox的 software rep:
#zypper ar -f http://download.virtualbox.org/virtualbox/rpm/opensuse/11.3 vbox
2. 安裝VirtualBox:
# zypper in VirtualBox-3.2
3. 新增使用者至vboxusers group中:
比如我要account lawrence可以於X11中啟動VirtualBox時,必需將這個帳號新增到vboxusers group中。
# useradd(usermod) -G vboxusers lawrence
Monday, July 05, 2010
Speed up OpenOffice
找到了一篇說明如何加快執行OpenOffice的文章如下:
用OpenOffice 3.1.1搭配OpenSUSE 11.2,的確是感覺到啟動的速度加快了許多!Nice tip!
Friday, June 18, 2010
Saturday, May 01, 2010
[好文推薦] Collecting and analyzing Linux kernel crashes - crash
發現到一篇介紹如何分析Linux Kernel panic的好文章,先收藏起來有空再來研究下。
Sunday, April 25, 2010
OSX: ClickToFlash for Safari
在Linux下不論是使用Google Chrome或是Firefox,帽客都習慣安裝個外掛程式來把Flash block起來,原因是Flash實在是太吃CPU的resource了,尤其是在小筆電上開網頁跑Flash時是一件很痛苦的事情,今天花了一點時間找到了一個在OSX上for Safari的好工具來block Flash,使用過後整台Mac的效率提昇了不少,ClickToFlash實在是個好工具!老G4請繼續撐下去吧!
Saturday, April 24, 2010
Install Skype on OpenSUSE 11.2 64bit
安裝Skype於OpenSUSE 11.2 64bit版本時發現到無法正常啟動,錯誤訊息如下:
解決的方法:
./skype: error while loading shared libraries: libQtGui.so.4: cannot open shared object file: No such file or directory
解決的方法:
zypper install libQtGui.so.4z
FYI.
Wednesday, March 31, 2010
搞定802.11X
搞了一陣子,總算把802.11x的環境在家裡架了起來。
Test Environment:
- Windows XP SP3: 802.11x with PEAP and import CA that generated from FreeRADIU Server.
- OpenSUSE 11.2: 802.11x with PEAP and import CA that generated from FreeRADIUS Server.
- AP: Authentication via the Radius Server and configured data encrypt method as WPA2-AES.
- FreeRADIUS: Support PEAP as default.
總算是成功了:
Test Environment:
- Windows XP SP3: 802.11x with PEAP and import CA that generated from FreeRADIU Server.
- OpenSUSE 11.2: 802.11x with PEAP and import CA that generated from FreeRADIUS Server.
- AP: Authentication via the Radius Server and configured data encrypt method as WPA2-AES.
- FreeRADIUS: Support PEAP as default.
總算是成功了:
Tuesday, March 30, 2010
To implement FreeRADIUS for LDAPs
架設流程:
Step1 ~ Step4 參考上次推薦的文章就可以架設起來,然而要實現FreeRADIUS for LDAPs只需要執行Step5就可以完成了,事實上也只是改變幾個參數。
1. To establish LDAP Server
2. To establish FreeRADIUS
3. To configure FreeRADIUS for LDAP
4. To establish LDAPs (TLS)
5. To establish FreeRADIUS for LDAPs:
於Server端執行radiusd -X,並於Client端透過radtest做驗證,以下是Server端的log:
rad_recv: Access-Request packet from host x.x.x.x:32896, id=190, length=60
Step1 ~ Step4 參考上次推薦的文章就可以架設起來,然而要實現FreeRADIUS for LDAPs只需要執行Step5就可以完成了,事實上也只是改變幾個參數。
1. To establish LDAP Server
2. To establish FreeRADIUS
3. To configure FreeRADIUS for LDAP
4. To establish LDAPs (TLS)
5. To establish FreeRADIUS for LDAPs:
修改step3中的radiusd.conf,讓FreeRADIUS知道要用LDAPs做認證。測試:
# vi /etc/radiusd.conf
........................
ldap {
# set this to 'yes' to use TLS encrypted connections
# to the LDAP database by using the StartTLS extended
# operation.
# The StartTLS operation is supposed to be used with normal
# ldap connections instead of using ldaps (port 689) connections
start_tls = yes
tls_cacertfile = /etc/openldap/cacerts/client.pem
#tls_cacertdir = /usr/local/etc/openldap/ssl/
# tls_certfile = /path/to/radius.crt
# tls_keyfile = /path/to/radius.key
# tls_randfile = /path/to/rnd
tls_require_cert = "demand"
........................
}
於Server端執行radiusd -X,並於Client端透過radtest做驗證,以下是Server端的log:
rad_recv: Access-Request packet from host x.x.x.x:32896, id=190, length=60
219 User-Name = "ldapuser"Note: x.x.x.x 代表LDAP Server的FQDN或IP address。
220 User-Password = "123456"
221 NAS-IP-Address = 255.255.255.255
222 NAS-Port = 0
223 Processing the authorize section of radiusd.conf
224 modcall: entering group authorize for request 0
225 modcall[authorize]: module "preprocess" returns ok for request 0
226 modcall[authorize]: module "chap" returns noop for request 0
227 modcall[authorize]: module "mschap" returns noop for request 0
228 rlm_realm: No '@' in User-Name = "ldapuser", looking up realm NULL
229 rlm_realm: No such realm "NULL"
230 modcall[authorize]: module "suffix" returns noop for request 0
231 rlm_eap: No EAP-Message, not doing EAP
232 modcall[authorize]: module "eap" returns noop for request 0
233 users: Matched entry DEFAULT at line 152
234 users: Matched entry DEFAULT at line 206
235 modcall[authorize]: module "files" returns ok for request 0
236 rlm_ldap: - authorize
237 rlm_ldap: performing user authorization for ldapuser
238 radius_xlat: '(uid=ldapuser)'
239 radius_xlat: 'dc=example,dc=com'
240 rlm_ldap: ldap_get_conn: Checking Id: 0
241 rlm_ldap: ldap_get_conn: Got Id: 0
242 rlm_ldap: attempting LDAP reconnection
243 rlm_ldap: (re)connect to x.x.x.x:389, authentication 0
244 rlm_ldap: setting TLS CACert File to /etc/openldap/cacerts/client.pem
245 rlm_ldap: setting TLS Require Cert to demand
246 rlm_ldap: could not set LDAP_OPT_X_TLS_REQUIRE_CERT option to demand
247 rlm_ldap: starting TLS
248 rlm_ldap: bind as / to x.x.x.x:389
249 rlm_ldap: waiting for bind result ...
250 rlm_ldap: Bind was successful
251 rlm_ldap: performing search in dc=example,dc=com, with filter (uid=ldapuser)
252 rlm_ldap: Added password {crypt}$1$/vvYrM2W$omOGg5A7NQVDxGcTb6afR1 in check items
253 rlm_ldap: looking for check items in directory...
254 rlm_ldap: looking for reply items in directory...
255 rlm_ldap: user ldapuser authorized to use remote access
256 rlm_ldap: ldap_release_conn: Release Id: 0
257 modcall[authorize]: module "ldap" returns ok for request 0
258 modcall: leaving group authorize (returns ok) for request 0
259 rad_check_password: Found Auth-Type LDAP
260 auth: type "LDAP"
261 Processing the authenticate section of radiusd.conf
262 modcall: entering group LDAP for request 0
263 rlm_ldap: - authenticate
264 rlm_ldap: login attempt by "ldapuser" with password "123456"
265 rlm_ldap: user DN: uid=ldapuser,ou=People,dc=example,dc=com
266 rlm_ldap: (re)connect to x.x.x.x:389, authentication 1
267 rlm_ldap: setting TLS CACert File to /etc/openldap/cacerts/client.pem
268 rlm_ldap: setting TLS Require Cert to demand
269 rlm_ldap: could not set LDAP_OPT_X_TLS_REQUIRE_CERT option to demand
270 rlm_ldap: starting TLS
271 rlm_ldap: bind as uid=ldapuser,ou=People,dc=example,dc=com/123456 to x.x.x.x:389
272 rlm_ldap: waiting for bind result ...
273 rlm_ldap: Bind was successful
274 rlm_ldap: user ldapuser authenticated succesfully
275 modcall[authenticate]: module "ldap" returns ok for request 0
276 modcall: leaving group LDAP (returns ok) for request 0
277 Sending Access-Accept of id 190 to x.x.x.x port 32896
Monday, March 29, 2010
Monday, March 22, 2010
Autoexpect Scenario
Autoexpect固然方便,但是很多時候還是必須手動改正Autoexpect所錄製過的script才能順利運行,以下將透過SSH登入本機後執行vmstat的指令來說明:
1. 執行Autoexpect:
# autoexpect此時系統會產生一個autoexpect的shell環境,並將使用者的動作紀錄起來,離開時請輸入exit指令,之後系統會產生個script.exp的紀錄檔(By default)。
2. 執行script.exp:
lawrence@X60:~/Desktop> ./script.exp
spawn /bin/bash
lawrence@X60:~/Desktop> ssh root@127.0.0.1
Password:
此時會發覺停留在輸入Password:而不再有進一步的動作,這是為何呢?
3. 查看並修正script.exp:
原始script.exp(僅截取錄製的部份):set timeout -1spawn $env(SHELL)match_max 100000expect -exact "]2;lawrence@X60:~/Desktop]1;X60lawrence@X60:~/Desktop> "send -- "ssh root@10"expect -exact [K"send -- ""expect -exact [K"send -- "127.0.0.1\r"expect -exact "127.0.0.1\rThe authenticity of host '127.0.0.1 (127.0.0.1)' can't be established.\rRSA key fingerprint is fa:19:31:7a:ac:04:41:af:4c:38:b7:58:16:a3:14:f8.\rAre you sure you want to continue connecting (yes/no)? "send -- "yes\r"expect -exact "yes\rWarning: Permanently added '127.0.0.1' (RSA) to the list of known hosts.\r\rPassword: "send -- "1234\r"expect -exact "\rLast login: Fri Mar 12 17:06:12 2010\r\rHave a lot of fun...\r[1m[31mX60:~ # [m"send -- "vmstat -n 1 5\r"expect -exact "vmstat -n 1 5\rprocs -----------memory---------- ---swap-- -----io---- -system-- -----cpu------\rr b swpd free buff cache si so bi bo in cs us sy id wa st\r14 0 25644 20660 26124 464024 0 1 17 23 881 255 7 3 89 1 0\r0 0 25644 20148 26124 464536 0 0 0 0 1725 2206 6 2 93 0 0\r0 0 25644 20404 26124 464264 0 0 0 0 1877 2234 3 3 95 0 0\r0 0 25644 20404 26124 464224 0 0 0 0 1736 2186 4 1 95 0 0\r0 0 25644 20404 26124 464224 0 0 0 0 1628 2168 3 2 95 0 0\r[1m[31mX60:~ # [m"send -- "ex"expect -exact [K"send -- ""expect -exact [K"send -- "logout\r"expect -exact "logout\rConnection to 127.0.0.1 closed.\r\r]2;lawrence@X60:~/Desktop]1;X60lawrence@X60:~/Desktop> "send -- "exit\r"expect eof問題1:The authenticity of host '127.0.0.1 (127.0.0.1)' can't be established.\rRSA key fingerprint is fa:19:31:7a:ac:04:41:af:4c:38:b7:58:16:a3:14:f8.\rAre you sure you want to continue connecting (yes/no)? "預設SSH Server/Client連接時,會去紀錄對方的金鑰,也就是因為這個原因,讓expect沒有得到預期的輸出,因為SSH第n次連線後就不需要紀錄彼此的金鑰了。問題2:Last login: Fri Mar 12 17:06:12 2010\r\rHave a lot of fun...\r^[\[1m^[\[31mX60:~ # ^[(B^[\[m"每次登入系統的時間一定會是不一樣的,所以把它也註解掉。問題3:procs -----------memory---------- ---swap-- -----io---- -system-- -----cpu------\rr b swpd free buff cache si so bi bo in cs us sy id wa st\r14 0 25644 20660 26124 464024 0 1 17 23 881 255 7 3 89 1 0\r0 0 25644 20148 26124 464536 0 0 0 0 1725 2206 6 2 93 0 0\r0 0 25644 20404 26124 464264 0 0 0 0 1877 2234 3 3 95 0 0\r0 0 25644 20404 26124 464224 0 0 0 0 1736 2186 4 1 95 0 0\r0 0 25644 20404 26124 464224 0 0 0 0 1628 2168 3 2 95 0 0\r^[\[1m^[\[31mX60:~ # ^[(B^[\[m"當然不需要上一次vmstat的輸出結果,所以也需要註解掉。修改過後:set timeout -1spawn $env(SHELL)match_max 100000expect -exact "]2;lawrence@X60:~/Desktop]1;X60lawrence@X60:~/Desktop> "send -- "ssh root@10"expect -exact [K"send -- ""expect -exact [K"send -- "127.0.0.1\r"expect -exact "Password: "send -- "1234\r"expect -exact "#"send -- "vmstat -n 1 5\r"expect -exact "#"send -- "ex"expect -exact [K"send -- ""expect -exact [K"send -- "logout\r"expect -exact "logout\rConnection to 127.0.0.1 closed.\r\r]2;lawrence@X60:~/Desktop]1;X60lawrence@X60:~/Desktop> "send -- "exit\r"expect eof
4. 執行:
lawrence@X60:~/Desktop> ./script2.expspawn /bin/bashlawrence@X60:~/Desktop> ssh root@127.0.0.1Password:Last login: Mon Mar 22 16:11:29 2010 from localhostHave a lot of fun...X60:~ # vmstat -n 1 5procs -----------memory---------- ---swap-- -----io---- -system-- -----cpu------r b swpd free buff cache si so bi bo in cs us sy id wa st0 0 31016 27124 23500 454188 0 1 16 23 880 303 7 3 89 1 00 0 31016 29204 23500 451648 0 0 0 20 1815 1834 2 3 95 0 00 0 31016 29204 23500 451676 0 0 0 0 1821 1878 2 2 96 0 00 0 31016 29700 23500 451232 0 0 0 0 1763 2029 3 2 95 0 00 0 31016 29700 23500 451184 0 0 0 0 1807 2241 2 2 95 0 0X60:~ # logoutConnection to 127.0.0.1 closed.lawrence@X60:~/Desktop> exitexitlawrence@X60:~/Desktop>
Autoexpect雖然有以上的小缺點,但還是能加快script開發的速度。
Friday, March 19, 2010
於Linux中偵測HD溫度
於原文eliu兄分享的方法延伸出再多一點的應用如下:
1. 將HD溫度每60秒紀錄在/var/log/message中:
# hddtemp -d /dev/hda -S 60Mar 19 15:08:54 server hddtemp[3253]: /dev/hda: ST320011A: 33 CMar 19 15:09:54 server hddtemp[3253]: /dev/hda: ST320011A: 33 C
2. 開機時啟動hddtemp:
# vi /etc/sysconfig/hddtempHDDTEMP_OPTIONS="-l 192.168.0.1 -d /dev/hda -S 60"#-l: listen on a specific interface (in TCP/IP daemon mode)#-d: run hddtemp in TCP/IP daemon mode (port 7634 by default.)#-S: log temperature to syslog every s seconds.# /etc/init.d/hddtemp start# chkconfig hddtemp on
3. 透過另一台主機即時監看HD溫度:
# while true; do date +%F-%H-%M-%S;nc 192.168.0.1 7634;echo"";sleep 1; done2010-03-19-15-13-23|/dev/hda|ST320011A|33|C|2010-03-19-15-13-24|/dev/hda|ST320011A|33|C|2010-03-19-15-13-25|/dev/hda|ST320011A|33|C|2010-03-19-15-13-26|/dev/hda|ST320011A|33|C|2010-03-19-15-13-27|/dev/hda|ST320011A|33|C
Thursday, March 18, 2010
To configure vendor specific information on Linux DHCP Server
This article will to explain how to configure the vendor specific information i.e., option 43 on Linux DHCP Server, maybe I'll use this function in the future.
Step1. To open and modify /etc/dhcpd.conf
1 ddns-update-style interim;2 ignore client-updates;3 option opt-43 code 43 = ip-address;45 subnet 192.168.1.0 netmask 255.255.255.0 {67 # --- default gateway8 option routers 192.168.1.1;9 option subnet-mask 255.255.255.0;1011 option nis-domain "domain.org";12 option domain-name "domain.org";13 option domain-name-servers 192.168.1.1;1415 option time-offset -18000; # Eastern Standard Time16 # option ntp-servers 192.168.1.1;17 # option netbios-name-servers 192.168.1.1;18 # --- Selects point-to-point node (default is hybrid). Don't change this unless19 # -- you understand Netbios very well20 # option netbios-node-type 2;2122 range dynamic-bootp 192.168.1.128 192.168.1.254;23 default-lease-time 21600;24 max-lease-time 43200;25 option opt-43 = "192.168.1.100";2627 # we want the nameserver to appear at a fixed address28 #host ns {29 # next-server marvin.redhat.com;30 # hardware ethernet 12:34:56:78:AB:CD;31 # fixed-address 207.175.42.254;32 #}33 }
Step 2. Restart DHCP Server:
# /etc/init.d/dhcpd restart# chkconfig dhcpd on
Step 3. Identify via packets record tool:
Wednesday, March 17, 2010
Wireless Network Basics guide
找到一本介紹Wireless Network基本常識的電子書,它是由NETGEAR所提供的,寫得還不錯,有興趣的朋友可以閱讀看看。
題外話:
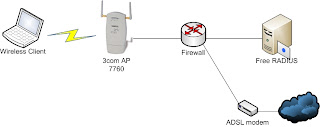
前幾天在家做了個測試,將位於3F的3com AP 7760的Power mode由Minimum設定成Full,然後跑到1F發現到laptop依然可以連接上AP,線上播放Youtube的Flash video還算流暢,瀏覽網頁還好,沒有很頓的感覺,訊號強度還有25%,這台AP應該是SISO的架構,有這樣的表現實在是很不錯,不過AP與我房間只有一牆之隔,所以還是把它改回到minimum了。
另外也把加密方法由WEP改成WPA2-AES了,我可不想被卡皇或螞蟻戰車這樣類似的破解AP加密的設備破解後,變成好鄰居AP呀~
Friday, March 12, 2010
[Shell Script] 長時間測試FTP穩定度
Script:
1 #!/bin/bash2 while (true)3 do4 lftp $1 -u ftp,ftp -e "cd /pub;get file;bye"5 lftp $1 -u ftp,ftp -e "cd /pub;put file;bye"6 done
Explain:
Line4: 以ftp account登入到FTP Server,並透過-e的指令將多個指令合併依序執行(切換到pub/抓取file/登出FTP)。Line5: 以ftp account登入到FTP Server,並透過-e的指令將多個指令合併依序執行(切換到pub/上傳file/登出FTP)。
How to execute:
server1:~/bin # ./ftpcon.sh 192.168.0.1
透過此script可以對DUT不間斷的做FTP下載與上傳的動作,FYI。
當然如果要做更advance的測試,建議用curl-loader應該會更好一點。
Subscribe to:
Posts (Atom)