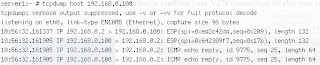
1. Test Environment:Left PC ----- Right PC
Letf PC:
IP address: 192.168.0.2/24
OS: opensuse 10
Install openswan-2.4.4-1.1
Right PC:
IP address: 192.168.0.100/24
OS: CentOS 5.0
Install openswan-2.4.9-31.el5
2.Setup procedure:2.1 Left PC:
2.1.1 Setup PSK:
# vi /etc/ipsec.secrets
192.168.0.2 192.168.0.100 : PSK "1234567890"
192.168.0.100 192.168.0.2 : PSK "1234567890"
2.1.2 Setup IPSec:
# vi /etc/ipsec.conf
conn hosttohost
# Left security gateway, subnet behind it, nexthop toward right.
left=192.168.0.2
#leftsubnet=192.168.0.0/24
#leftnexthop=10.4.0.1
# Right security gateway, subnet behind it, nexthop toward left.
right=192.168.0.100
#rightsubnet=192.168.1.0/24
#rightnexthop=10.5.30.254
# To authorize this connection, but not actually start it,
# at startup, uncomment this.
type=tunnel
auto=add
authby=secret
2.1.3 Start IPSec
# rcipsec start
# ipsec auto --up hosttohost
2.2 Right PC:
2.2.1 Setup PSK:
# vi /etc/ipsec.secrets
192.168.0.100 192.168.0.2 : PSK "1234567890"
192.168.0.2 192.168.0.100 : PSK "1234567890"
2.2.2 Setup IPSec:
# cp /etc/ipsec.d/examples/linux-linux.conf ..
# vi /etc/ipsec.d/linux-linux.conf
conn linux-to-linux
#
# Simple use raw RSA keys
# After starting openswan, run: ipsec showhostkey --left (or --right)
# and fill in the connection similarly to the example below.
#
left=192.168.0.100
# optional
# leftsubnet=10.0.1.0/24
#leftid=@bofh.xelerance.com
#leftrsasigkey=0sAQPWTXt8DDlEhTZJ91ngNMxTSyuos6JZxXQmtRcwUl6ppUCcuuWvjXrF/qiz6eiL1LMlpGJyG1oVhtFhTaFJl7ZkF/4J1B9LCFzYxvYI97AnLuC0op5pVAZ1SZx29+aRjeMcKC4zbZ6dMMjUdn9H1gqG9rpE0MBEFNSVLEu9U8rtlz14RfxQAQ9ePj64HnGLfgJlDB0VYhKEIcRihy72bvjZ4eoX16S1EY1FgnHyrveZPxRi8sgn6Q19RytEzSmUAlGjvMDhNfenq6WCSYMeqgj0jFSArTNBQmR2QBkUG6NSOXfb+18c6jDPicGmbmWfoRx/PUJo46WiRF4RRmsxnFpbHpklILFzEJ+/k6qHVAekpVfp
# The remote user.
#
right=192.168.0.2
#rightid=@tla.xelerance.com
# optional
# rightsubnet=10.0.2.0/24
#rightrsasigkey=0sAQNxf6caKULJklYZycuo66Ko0U+iHaJUDr0QZHnG4MJ9IRNYi5H6kPxcwKIXkg+OGo+NeUyyWDEc+ox27BFYViAHQNEyBRLZu0kyE681h+cHm7lfCSy0AOEBSCyZF3aGcL8GWxVhtimpJQ4tNxXZg7tLX5sfYw8mZnUBjkHvyccIred/q3cNWbDlq2WU4TL+NBb5FnxXi9Hk/SRV7sMe56fvZuXkcJu4e2C7uocltzzF1b0BZx7yeXwHjzqAWnW/UA54fbSTvzgnrpSC+FMuhWTI1EdxcqGaOFIjGWWGV2nxg/QaPU9i8vpwFwrEEdCJTiqlbYYNudblg4vYthnVNez0/RkfZHfhAaHdbJRSaQzOu88h
authby=secret
auto=add
type=tunnel
2.2.3 Start IPSec:
# service ipsec start
# ipsec auto --up linux-to-linux
3.Verify:Ping Right PC from Left PC and to check that traffic actually got encrypted!